漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0118326
漏洞标题:花集网漏洞问题打包
相关厂商:浙江花集网科技有限公司
漏洞作者: M4sk
提交时间:2015-06-05 12:26
修复时间:2015-07-23 11:12
公开时间:2015-07-23 11:12
漏洞类型:敏感信息泄露
危害等级:中
自评Rank:10
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-06-05: 细节已通知厂商并且等待厂商处理中
2015-06-08: 厂商已经确认,细节仅向厂商公开
2015-06-18: 细节向核心白帽子及相关领域专家公开
2015-06-28: 细节向普通白帽子公开
2015-07-08: 细节向实习白帽子公开
2015-07-23: 细节向公众公开
简要描述:
RT
详细说明:
SVN信息泄露:
http://115.236.77.174:81/.svn/entries
http://baike.huaji.com/.svn/entries
http://shop.huaji.com/.svn/entries
还有好多
http://bbs.huaji.com/images/wind/file/.svn/entries
http://bbs.huaji.com/.svn/entries
http://bbs.huaji.com/images/face/.svn/entries
http://bbs.huaji.com/images/post/smile/wangwang/.svn/entries
http://bbs.huaji.com/images/post/smile/default/.svn/entries
http://bbs.huaji.com/images/wind/level/.svn/entries
http://bbs.huaji.com/images/wind/thread/.svn/entries
http://bbs.huaji.com/images/.svn/entries
http://bbs.huaji.com/images/wind/index/.svn/entries
-------------------------------------------------------------------------------------
server-status信息泄露:
http://a.huaji.com/server-status
http://help.huaji.com/server-status
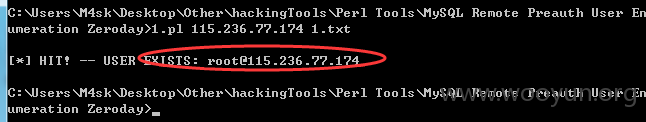
MySQL User Enumeration:枚举mysql用户名
http://115.236.77.174
脚本如下:
SQL报错:
http://www.huaji.com/member/home
A Database Error Occurred
Error Number: 1064
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '',130110326828) GROUP BY `goods`.`goods_id`' at line 4
SELECT `goods`.`goods_id`, `goods`.`goods_no`, `goods`.`store_id`, `goods`.`goods_name`, `goods`.`price`, `goods`.`default_image`, `goods`.`itype`, `seller`.`floristname` FROM (`goods`) JOIN `seller` ON `seller`.`uniqueid` = `goods`.`store_id` WHERE `goods`.`goods_no` in (130110326828',130110326828) GROUP BY `goods`.`goods_id`
Filename: /home/huaji/www/html/models/seller/mproduct.php
Line Number: 76
漏洞证明:
综上 问题太多了 还有没提交的建议自检
修复方案:
你们会的
版权声明:转载请注明来源 M4sk@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:6
确认时间:2015-06-08 11:11
厂商回复:
感谢提交
最新状态:
暂无