之前提交了 http://wooyun.org/bugs/wooyun-2015-0114708
(标题:一种可大规模定向钓鱼携程旅游网千万用户的攻击过程重放(附案例,非携程用户依然躺枪)
这个比较鸡肋,因为还需要高深的html技术去构造,并且后面的表单并不能去掉,只能在一块区域自定义内容
那么so,附上直接版的吧,大招。
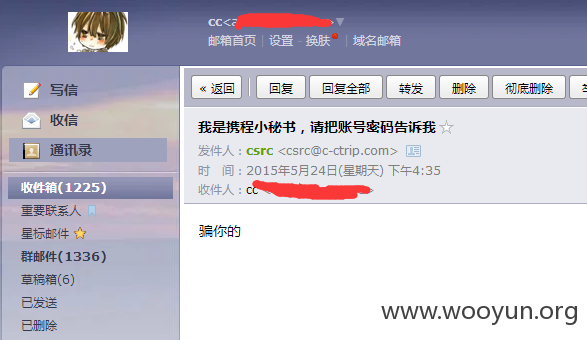
携程有两个域名
ctrip.com 和 c-ctrip.com
其中
ctrip的mx和txt记录:
c-ctrip.com的mx和txt记录:
diff 一下
ctrip.com域下作了spf
但是
c-ctrip.com域下并没有DNS记录txt类型的spf记录登记邮件服务器IP
看证明: