漏洞概要
关注数(24)
关注此漏洞
漏洞标题:浙江教育考试院网站又一SQL注入漏洞,可读取浙江考生信息
提交时间:2015-03-16 11:19
修复时间:2015-05-04 11:12
公开时间:2015-05-04 11:12
漏洞类型:SQL注射漏洞
危害等级:中
自评Rank:8
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
Tags标签:
无
漏洞详情
披露状态:
2015-03-16: 细节已通知厂商并且等待厂商处理中
2015-03-20: 厂商已经确认,细节仅向厂商公开
2015-03-30: 细节向核心白帽子及相关领域专家公开
2015-04-09: 细节向普通白帽子公开
2015-04-19: 细节向实习白帽子公开
2015-05-04: 细节向公众公开
简要描述:
最近大家都在挖浙江教育考试院网站的漏洞,之前发现了个漏洞还被人抢先提交了。之前的SQL注入漏洞已经修复,但是在另一处仍可以注入
( •̀ .̫ •́ )✧ 。涉及浙江考生信息,求求你们认认真真的排查一下都修复掉好么。
详细说明:
对于登陆等操作确实进行了过滤,但是登陆成功将登陆学生的身份证号储存在本地的cookies中(名为usersfz P.S 对这种英文+拼音的命名方式感到无力Orz),之后的部分操作(例如这个会考成绩查询
)直接调用了这个cookie并放入数据库中拼接查询,没有经过任何过滤,很容易注入。
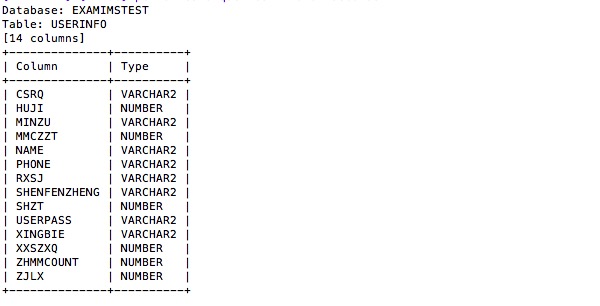
漏洞证明:
sqlmap截图及部分数据库结构
修复方案:
cookies里的数据是不可控的! 不要将用户登陆的凭证放在cookies里,同时也不要直接读取cookies里的数据不经过滤直接拼接放入数据库中查询!
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:10
确认时间:2015-03-20 11:10
厂商回复:
CNVD确认所述情况,已经转由CNCERT下发给分中心,由其后续协调网站管理单位处置。
最新状态:
暂无



