漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2014-088516
漏洞标题:支付宝钱包本地拒绝服务
相关厂商:支付宝
漏洞作者: elong
提交时间:2014-12-25 16:22
修复时间:2015-03-25 16:24
公开时间:2015-03-25 16:24
漏洞类型:拒绝服务
危害等级:低
自评Rank:2
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2014-12-25: 细节已通知厂商并且等待厂商处理中
2014-12-25: 厂商已经确认,细节仅向厂商公开
2014-12-28: 细节向第三方安全合作伙伴开放
2015-02-18: 细节向核心白帽子及相关领域专家公开
2015-02-28: 细节向普通白帽子公开
2015-03-10: 细节向实习白帽子公开
2015-03-25: 细节向公众公开
简要描述:
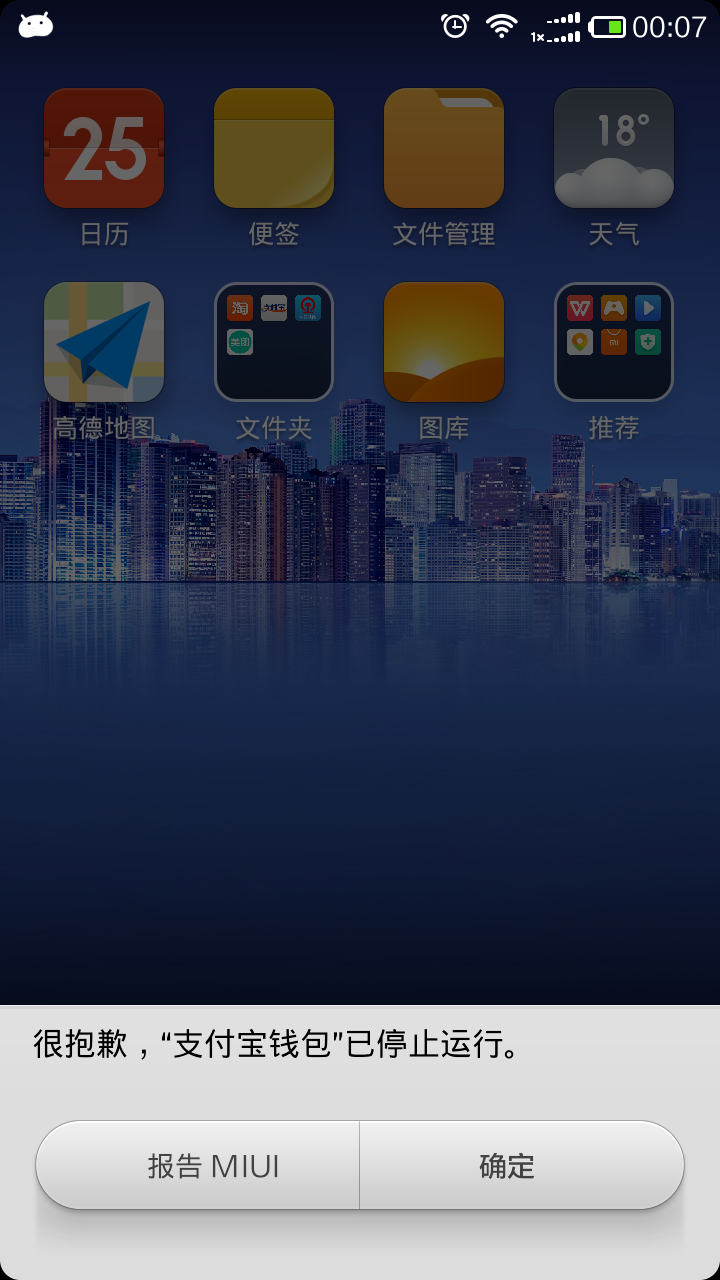
支付宝钱包存在本地拒绝服务问题,导致被攻击时,无法提供服务
详细说明:
暴露了未正常实现的组件
12-24 23:47:52.088: E/AndroidRuntime(26909): java.lang.RuntimeException: Unable to instantiate activity ComponentInfo{com.eg.android.AlipayGphone/com.alipay.mobile.campuscard.ui.CampusCardMainActivity}: java.lang.ClassNotFoundException: com.alipay.mobile.campuscard.ui.CampusCardMainActivity
12-24 23:47:52.088: E/AndroidRuntime(26909): at android.app.ActivityThread.performLaunchActivity(ActivityThread.java:2016)
12-24 23:47:52.088: E/AndroidRuntime(26909): at android.app.ActivityThread.handleLaunchActivity(ActivityThread.java:2117)
12-24 23:47:52.088: E/AndroidRuntime(26909): at android.app.ActivityThread.access$600(ActivityThread.java:140)
12-24 23:47:52.088: E/AndroidRuntime(26909): at android.app.ActivityThread$H.handleMessage(ActivityThread.java:1213)
12-24 23:47:52.088: E/AndroidRuntime(26909): at android.os.Handler.dispatchMessage(Handler.java:99)
12-24 23:47:52.088: E/AndroidRuntime(26909): at android.os.Looper.loop(Looper.java:137)
12-24 23:47:52.088: E/AndroidRuntime(26909): at android.app.ActivityThread.main(ActivityThread.java:4914)
12-24 23:47:52.088: E/AndroidRuntime(26909): at java.lang.reflect.Method.invokeNative(Native Method)
12-24 23:47:52.088: E/AndroidRuntime(26909): at java.lang.reflect.Method.invoke(Method.java:511)
12-24 23:47:52.088: E/AndroidRuntime(26909): at com.android.internal.os.ZygoteInit$MethodAndArgsCaller.run(ZygoteInit.java:808)
12-24 23:47:52.088: E/AndroidRuntime(26909): at com.android.internal.os.ZygoteInit.main(ZygoteInit.java:575)
12-24 23:47:52.088: E/AndroidRuntime(26909): at dalvik.system.NativeStart.main(Native Method)
12-24 23:47:52.088: E/AndroidRuntime(26909): Caused by: java.lang.ClassNotFoundException: com.alipay.mobile.campuscard.ui.CampusCardMainActivity
12-24 23:47:52.088: E/AndroidRuntime(26909): at dalvik.system.BaseDexClassLoader.findClass(BaseDexClassLoader.java:61)
12-24 23:47:52.088: E/AndroidRuntime(26909): at java.lang.ClassLoader.loadClass(ClassLoader.java:501)
12-24 23:47:52.088: E/AndroidRuntime(26909): at java.lang.ClassLoader.loadClass(ClassLoader.java:461)
12-24 23:47:52.088: E/AndroidRuntime(26909): at android.app.Instrumentation.newActivity(Instrumentation.java:1053)
12-24 23:47:52.088: E/AndroidRuntime(26909): at com.lbe.security.service.core.client.b.x.newActivity(Unknown Source)
12-24 23:47:52.088: E/AndroidRuntime(26909): at android.app.ActivityThread.performLaunchActivity(ActivityThread.java:2007)
12-24 23:47:52.088: E/AndroidRuntime(26909): ... 11 more
漏洞证明:
修复方案:
N/A
版权声明:转载请注明来源 elong@乌云
漏洞回应
厂商回应:
危害等级:低
漏洞Rank:3
确认时间:2014-12-25 18:39
厂商回复:
感谢您对支付宝安全的关注
最新状态:
暂无