第二发,求上首页~
信息:
上海市普陀区中心医院健康体检站 :报告查询
链接:http://www.sptdch.cn:8080/happy/reportsearch.asp
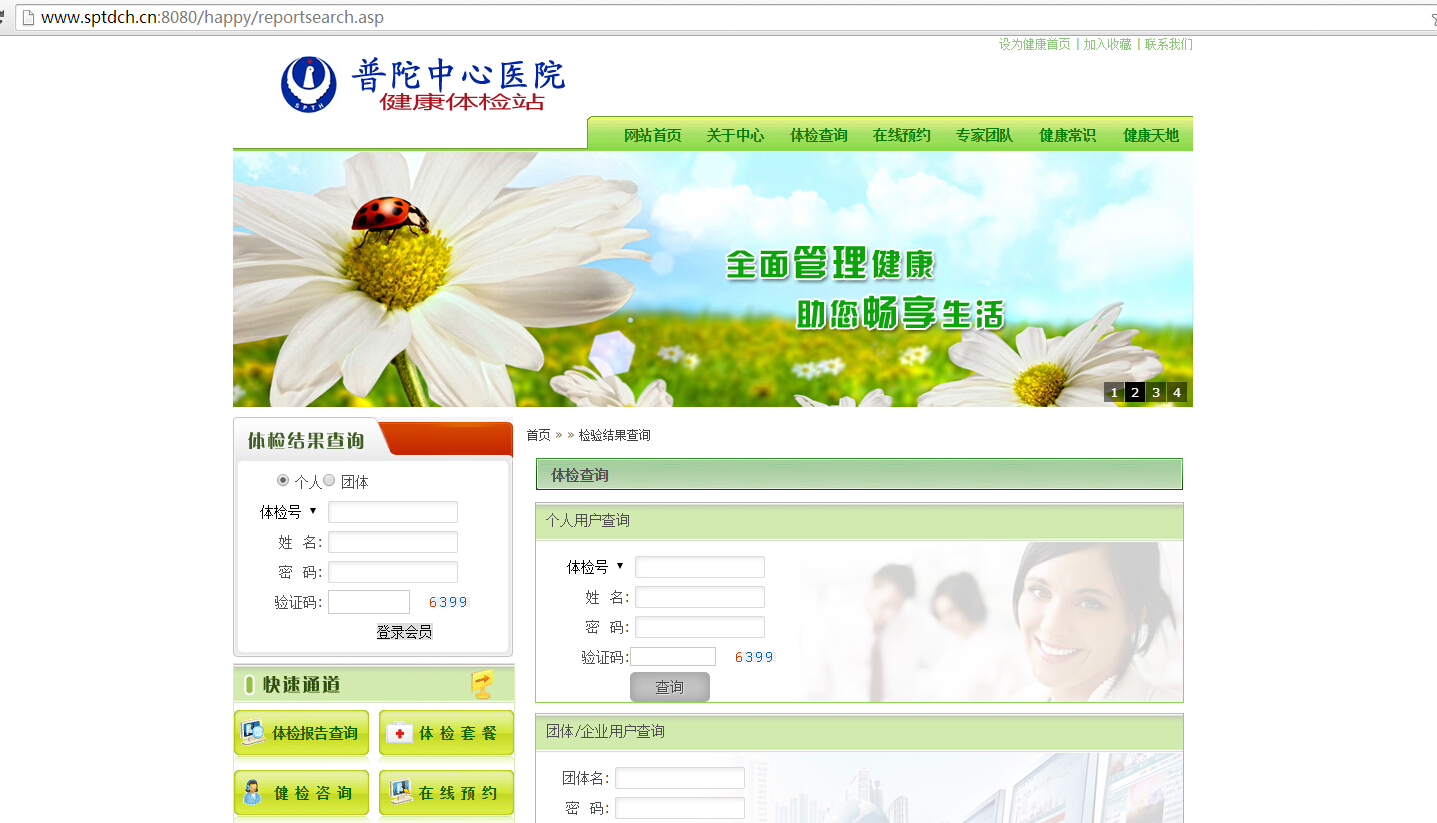
注入点:
查询处POST注入,验证码不会过期(审核验证时请重新拦截请求,防止验证码因时间过长而失效)
SQLMAP:
表名以B结尾的是不同科室的检查结果,加起来几百万
表dbo.JCXX为体检用户信息,数据量127943,表结构如下,一百多个字段
登陆页面出查询所需信息为体检号、姓名、查询密码对应字段ID、XM、PASSWORD
这里举一个例子证明
6212270069 汤俊杰 767793
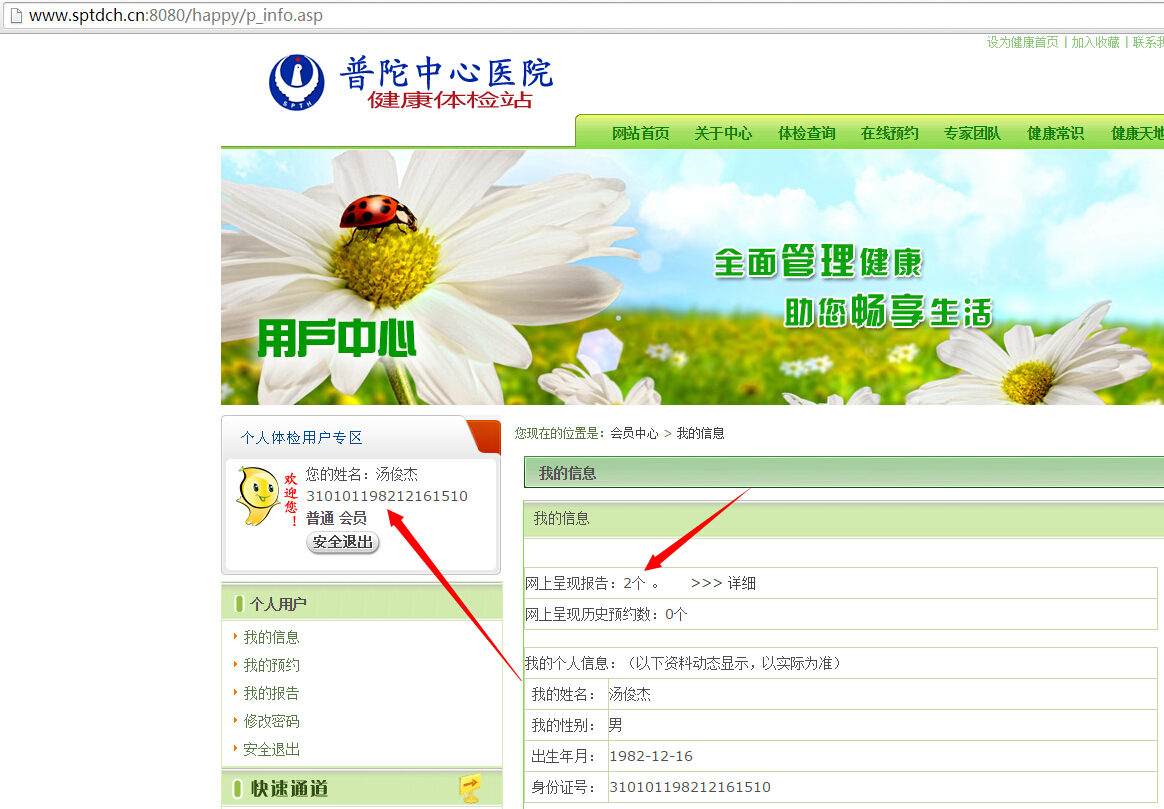
可查询、下载体检报告
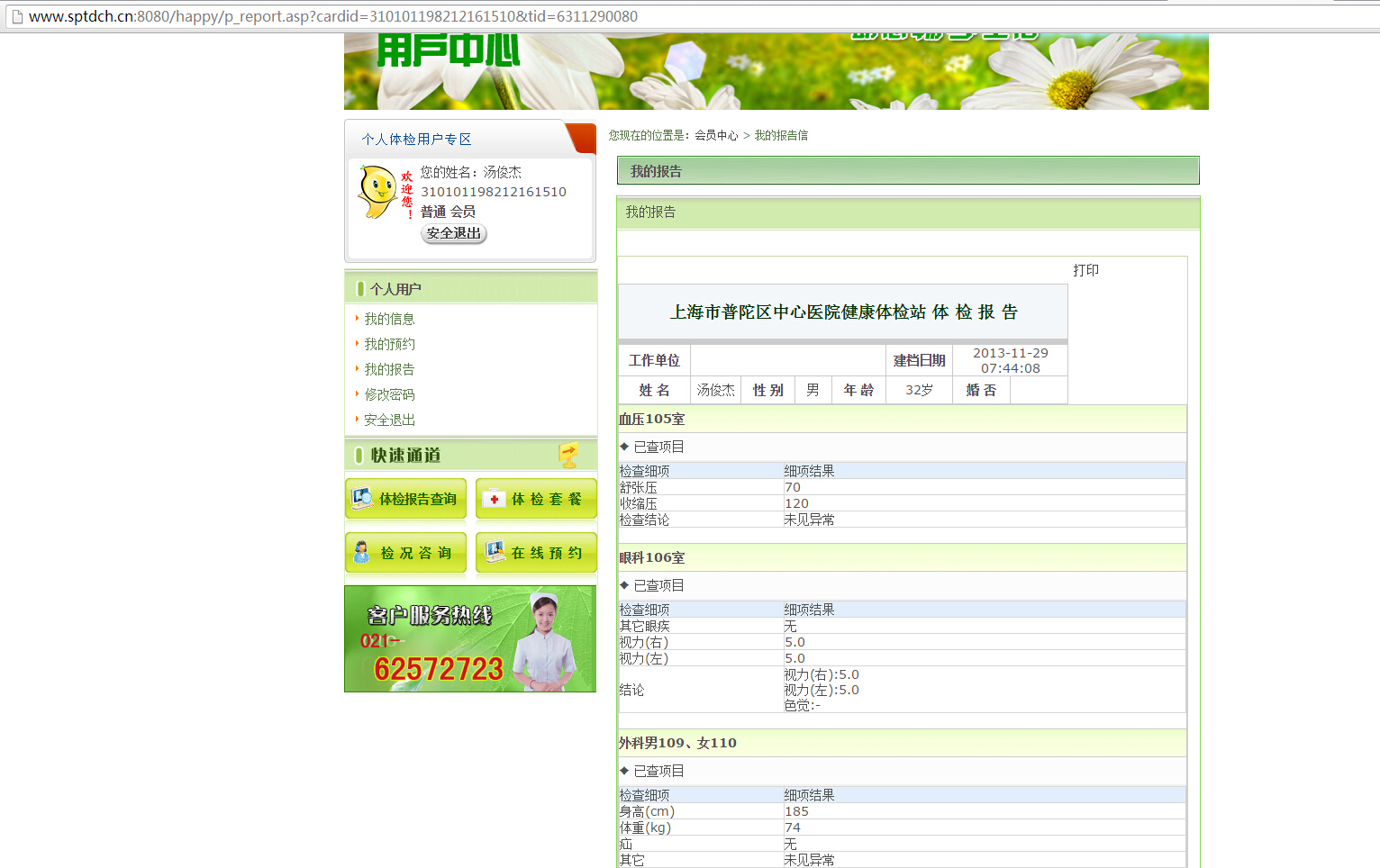
以一个人一份体检报告,至少有12W+,如果一人两份,则是24W+
还有一个表zk_WebYH为web预约用户信息,记录数34252,可以登陆,里面有身份证号等信息,这里就不列了
两个合起来就有15W+的用户





