漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2014-059168
漏洞标题:搜狗某应用SQL注射(泄漏NagiOS等敏感信息)
相关厂商:搜狗
漏洞作者: 超威蓝猫
提交时间:2014-05-02 13:21
修复时间:2014-06-16 13:22
公开时间:2014-06-16 13:22
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:19
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2014-05-02: 细节已通知厂商并且等待厂商处理中
2014-05-04: 厂商已经确认,细节仅向厂商公开
2014-05-14: 细节向核心白帽子及相关领域专家公开
2014-05-24: 细节向普通白帽子公开
2014-06-03: 细节向实习白帽子公开
2014-06-16: 细节向公众公开
简要描述:
有一个库中有近2亿条MD5,不知道是什么东西..
详细说明:
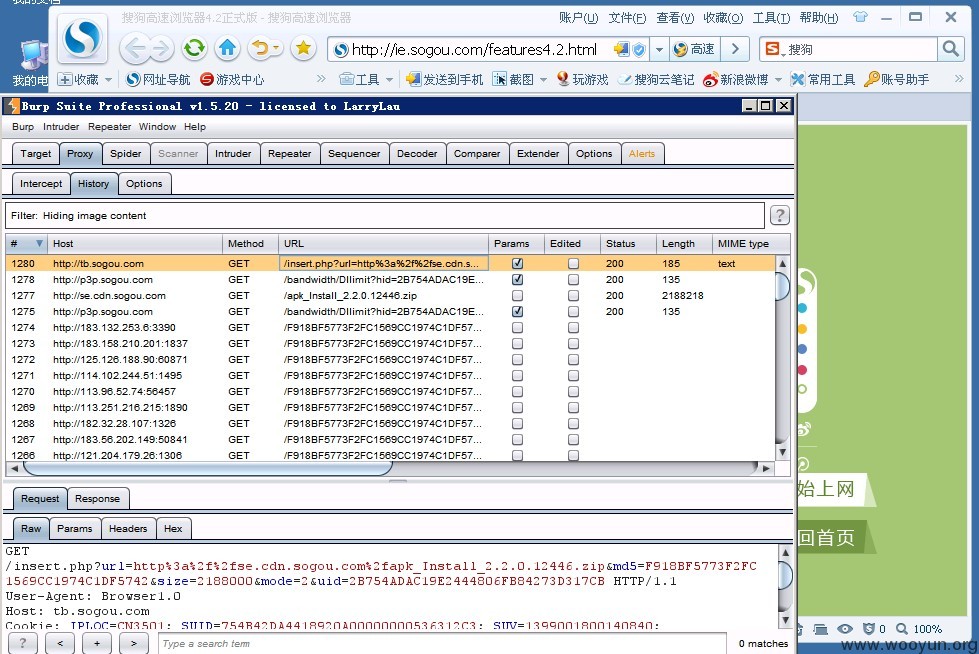
安装最新版本的"搜狗高速浏览器",打开后使用Burp抓包,发现浏览器对如下地址发起了一次HTTP请求:
其中,md5参数存在布尔型盲注。
--count了一下发现nagios的库,应该是可以进一步渗透的。p4p库中有近两亿条MD5,不知道是什么东西..
漏洞证明:
修复方案:
你们更专业:)
版权声明:转载请注明来源 超威蓝猫@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:10
确认时间:2014-05-04 16:45
厂商回复:
感谢支持!
欢迎到SGSRC提交搜狗漏洞,地址: http://
最新状态:
暂无