1.拿到程序后,我们先来看看 登录页面。(login.php)
先来看看管理登录页面(admin/adminlogin.php)的核心代码
从
和
这两句发现,似乎用户名只允许使用admin 并且密码被md5加密。
现在似乎还无法绕过登录
我们再来看看用户登录页面(login.php)的核心代码
这个页面出现了一个比较经典的语句
这句SQL语句的意思是查询是否存在管理员,如果存在就提升权限。
看了一下周围的代码,没有发现任何过滤。
根据此SQL语句结构,我们构造一个"万能密码":
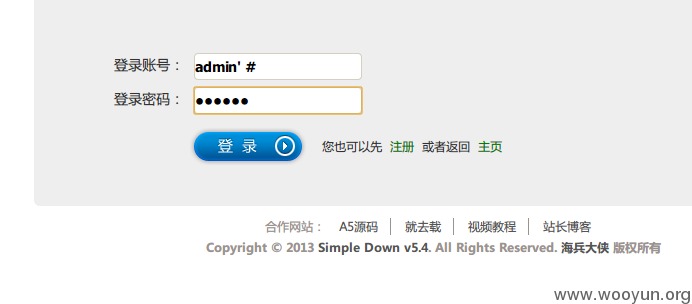
进入服务器后就会变成:
意为:查询目标表中是否存在admin用户名,而查询密码的语句已经被 # 所注释。
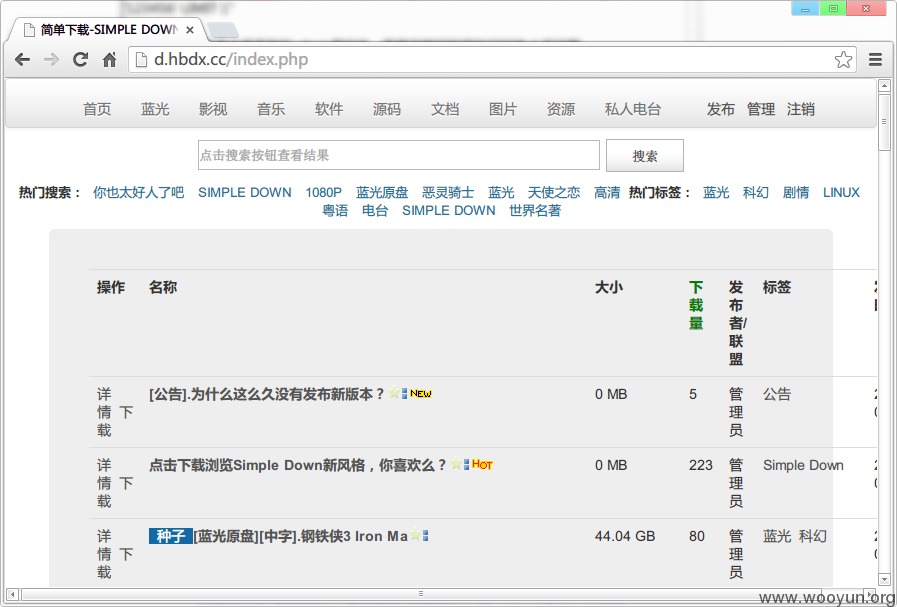
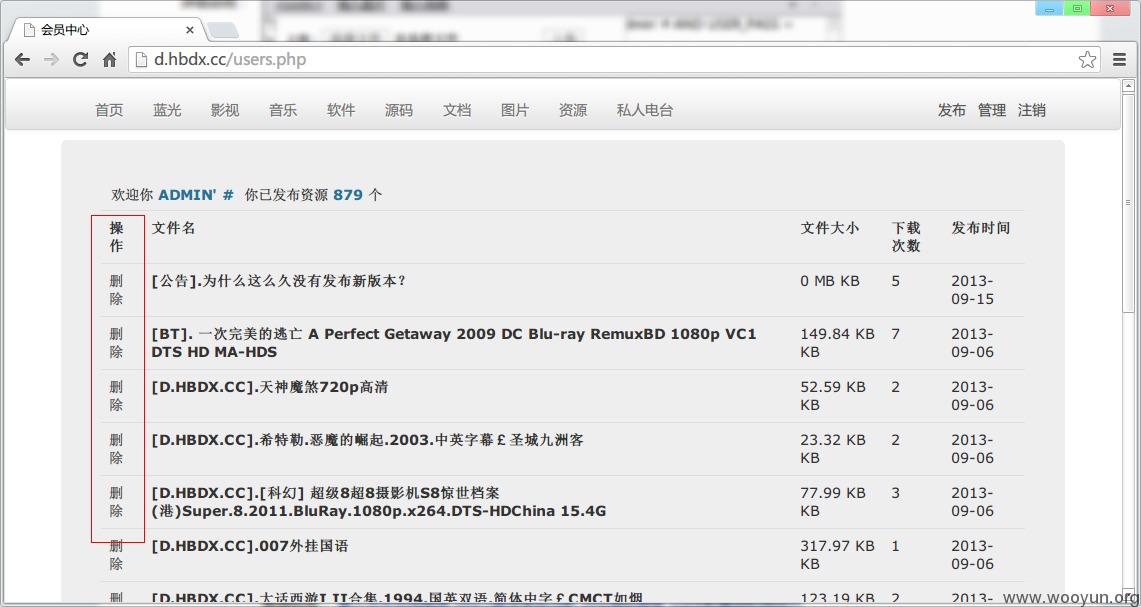
登录一下果然进入了:
2.再来看看注册页面。
同样无任何过滤,根据最后一层验证的SQL语句
我们可以构造一个form来绕过前端验证
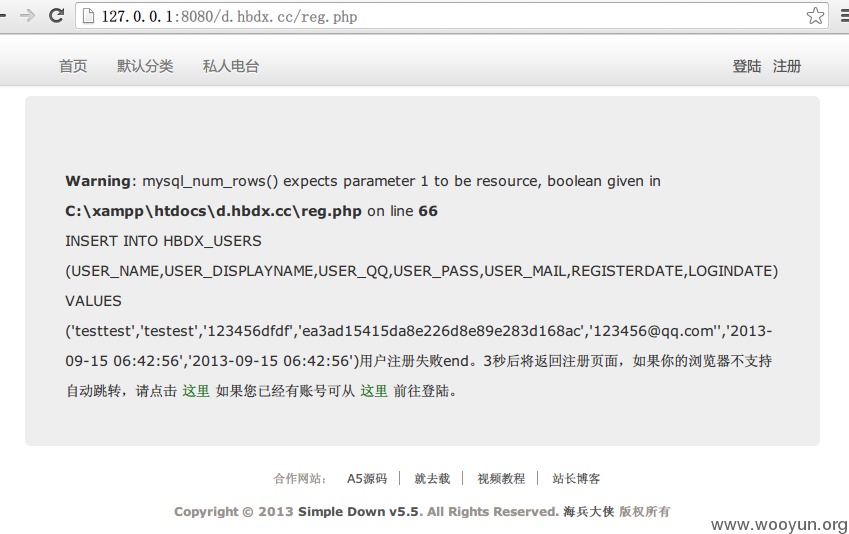
可以看见提交之后出现报错,我们可以使用子查询构造除了HBDX_USERS表以外的 读取任意表数据的 SQL语句
因为这个站的表除了HBDX_USERS,其他的表并没有什么敏感数据故不再演示。
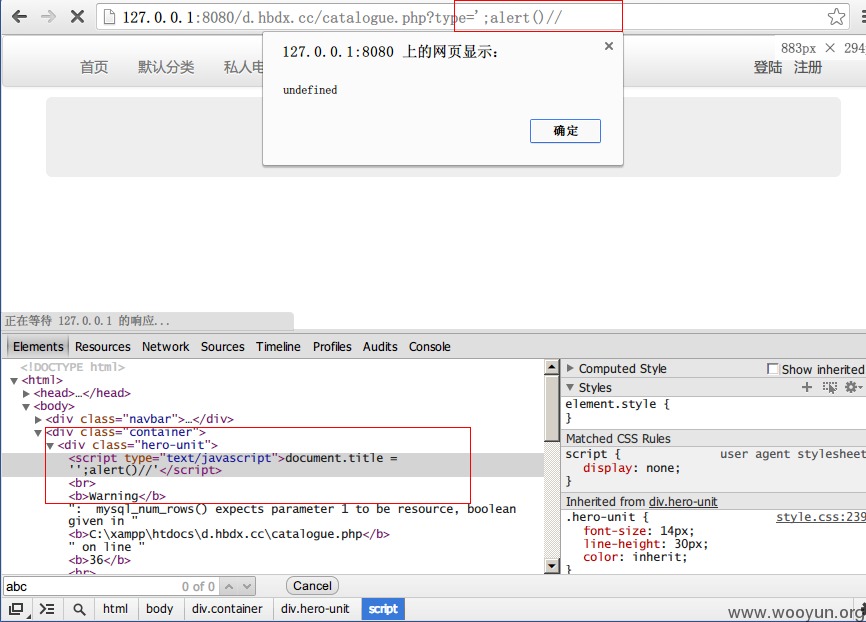
3.再来看看(catalogue.php)
这个页面可控参数太多
@$type = strval($_GET['type']); //得到type的值
@$page = intval($_GET['page']); //得到page的值
@$hot = strval($_GET['hot']); //得到type的值
$page = isset($_GET['page'])?intval($_GET['page']):1; //当前页数
这个页面也同样无任何过滤。我们尝试type参数,除了出现注入以外,还出现了输出在<script>中的情况
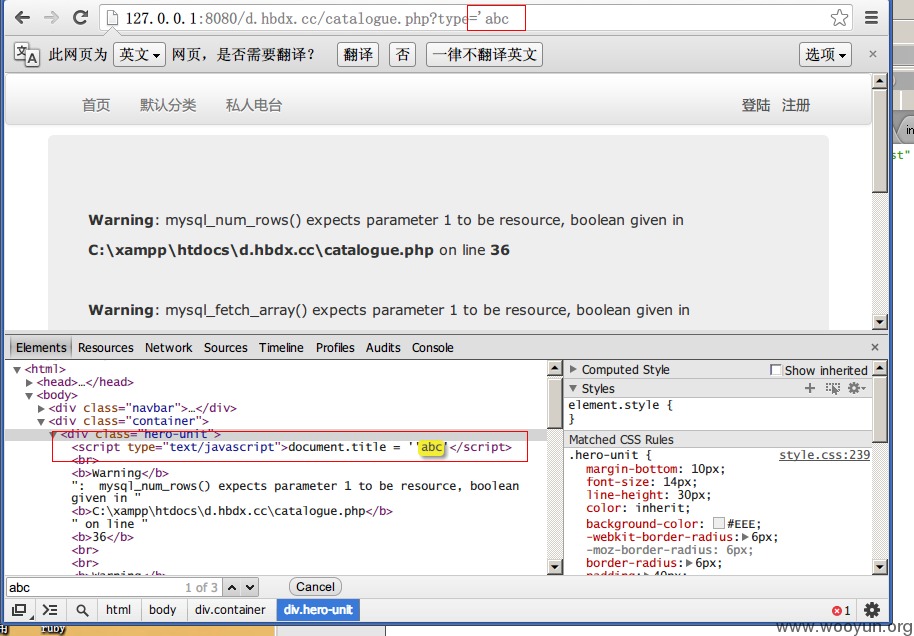
我们闭合之后: