漏洞概要
关注数(24)
关注此漏洞
漏洞标题:敏感信息泄露系列#2 开发运维管理不当可导致微博大V被控制
提交时间:2013-09-12 19:29
修复时间:2013-10-27 19:30
公开时间:2013-10-27 19:30
漏洞类型:敏感信息泄露
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
Tags标签:
无
漏洞详情
披露状态:
2013-09-12: 细节已通知厂商并且等待厂商处理中
2013-09-13: 厂商已经确认,细节仅向厂商公开
2013-09-23: 细节向核心白帽子及相关领域专家公开
2013-10-03: 细节向普通白帽子公开
2013-10-13: 细节向实习白帽子公开
2013-10-27: 细节向公众公开
简要描述:
有时候,一个微不足道的信息泄露问题就能造成整个企业安全的崩盘
过去几年中,安全领域在如何处理自身漏洞的评估方面取得了长足的进步,几乎每个企业或个人都越来越多地依托第三方系统来运营自身业务,第三方系统被入侵的同时也将导致相关企业威胁增加。
#安全需要顾全整体#
http://www.wooyun.org/bugs/wooyun-2013-032750 续集!
详细说明:
#1 检测发现vmaibo所有业务系统都存在SVN信息泄露
http://www.vmaibo.com/.svn/entries
http://biz.vmaibo.com/.svn/entries
http://read.vmaibo.com/.svn/entries
# 微博名人版
#2 通过SVN泄露的信息,间接利用
通过泄露的信息得知SVN服务器的物理真是地址,219.239.***.*,结合已经获取到的author信息,构造弱口令字典,进行自动化暴力猜解。
./hydra -L vmaibo_user.txt -P vmaibo_pass.txt 219.239.***.* Subversion
成功爆破出fqwang用户弱口令fqwang + 2013
#3 通过SVN check 开发版本源码
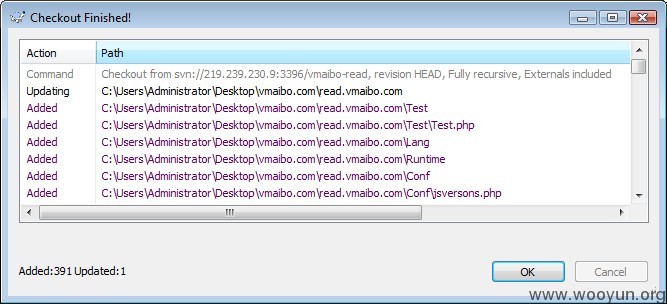
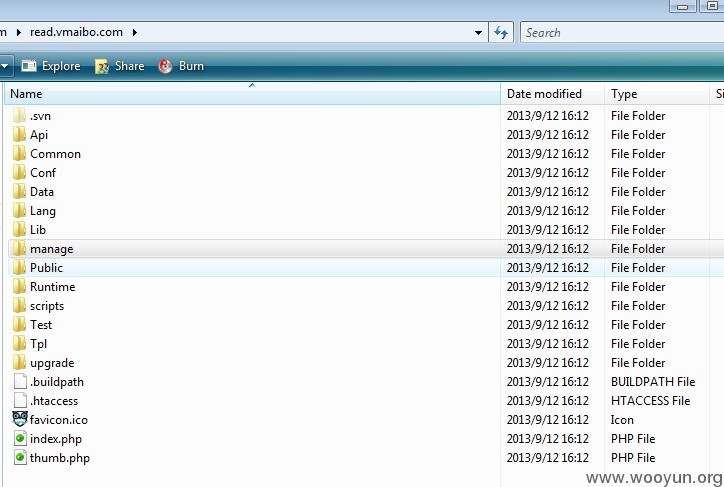
漏洞证明:
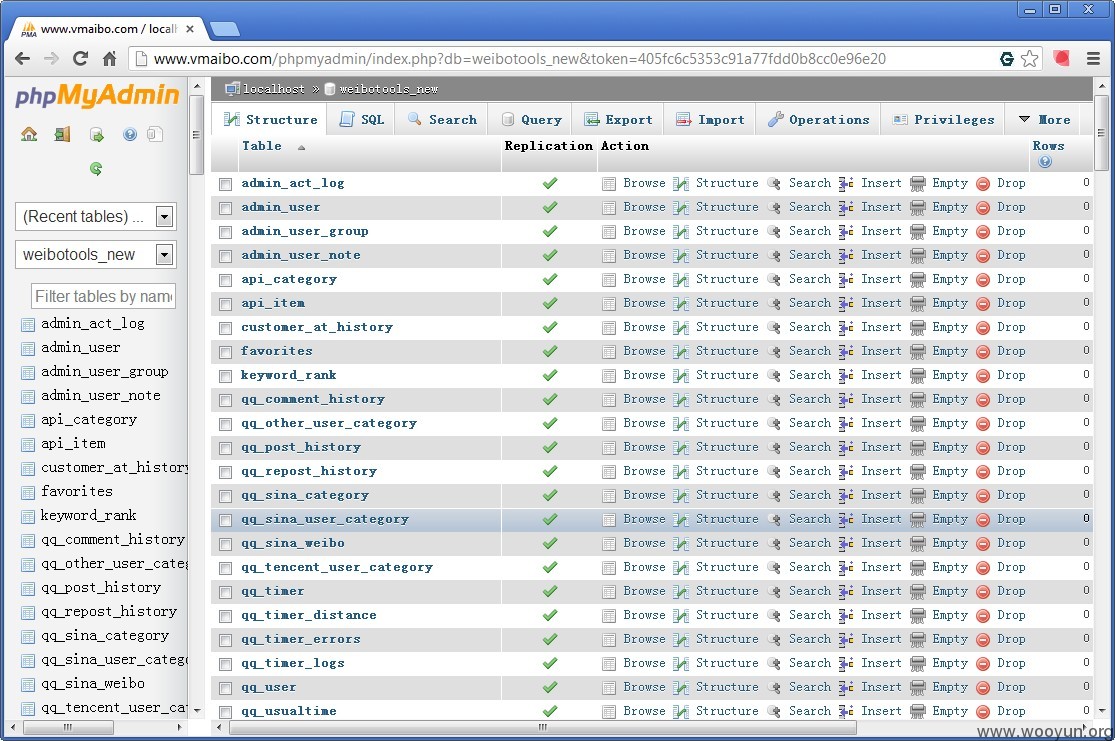
# 脉搏网自带phpmyadmin功能,通过源码目录找到的数据库密码连接
http://read.vmaibo.com/phpmyadmin/
http://www.vmaibo.com/phpmyadmin/
# 后台地址
http://adm.vmaibo.com/login
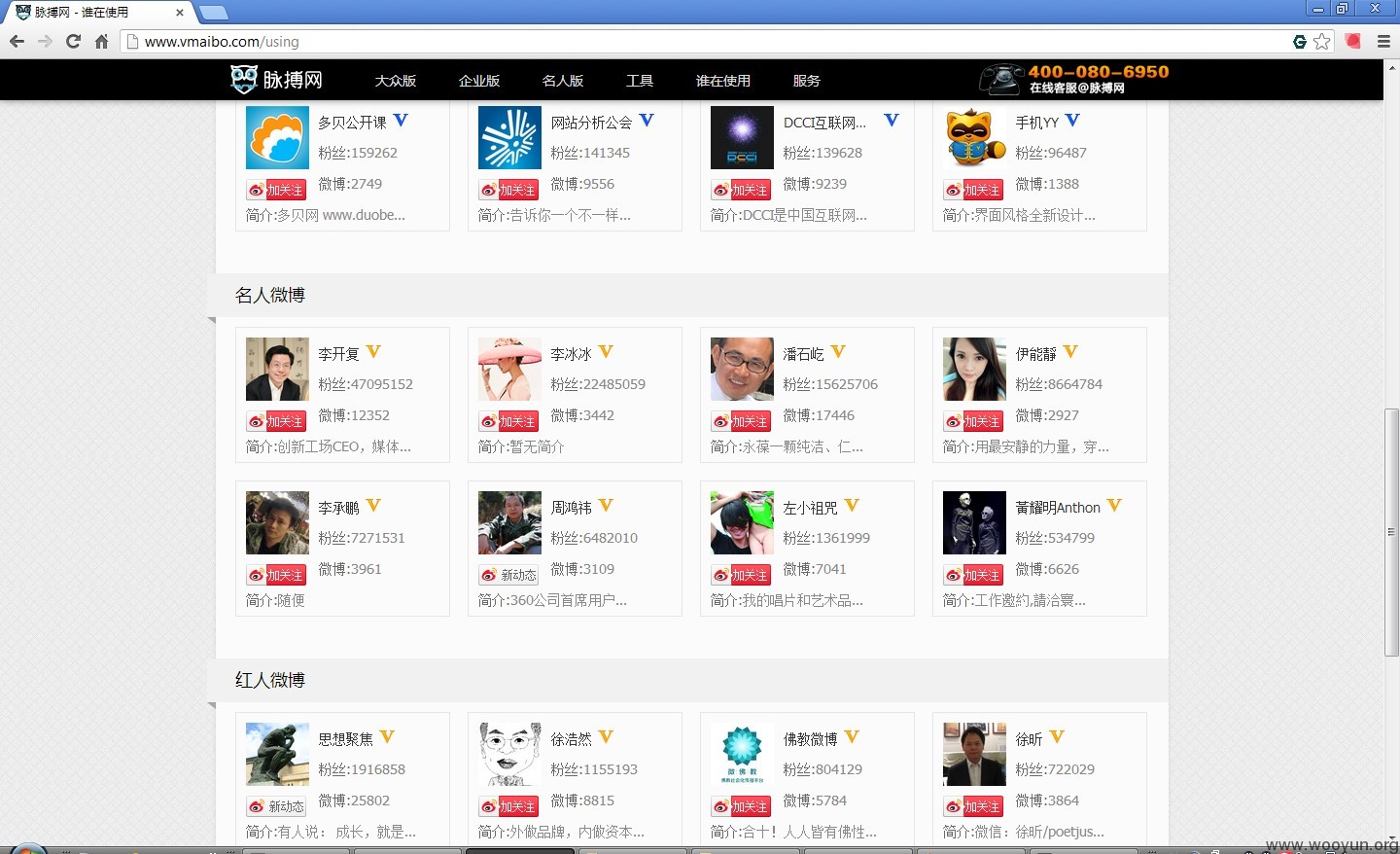
# 间接利用,可以直接获取到李开复同学的微博TOKEN
受影响的大V如下:http://www.vmaibo.com/using
修复方案:
#1 删除掉svn泄露地址
#2 重命名phpmyadmin地址
#3 svn服务端管理端口不对外开放
版权声明:转载请注明来源 猪猪侠@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:20
确认时间:2013-09-13 15:38
厂商回复:
感谢提出漏洞,我们已经着手处理了,并且正在进行安全处理,感谢猪猪侠!
最新状态:
暂无






