漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2013-022334
漏洞标题:中国教师网分站再爆致命漏洞(百万师表数据侧漏)
相关厂商:中国教师研修网
漏洞作者: 啦绯哥
提交时间:2013-04-22 22:20
修复时间:2013-06-06 22:20
公开时间:2013-06-06 22:20
漏洞类型:命令执行
危害等级:高
自评Rank:15
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2013-04-22: 细节已通知厂商并且等待厂商处理中
2013-04-26: 厂商已经确认,细节仅向厂商公开
2013-05-06: 细节向核心白帽子及相关领域专家公开
2013-05-16: 细节向普通白帽子公开
2013-05-26: 细节向实习白帽子公开
2013-06-06: 细节向公众公开
简要描述:
看到之前shack2提交过一次类似的漏洞,现其他分站再出类似情况
详细说明:
http://ucenter.teacherclub.com.cn/ucenter/user/regist!registUserInput.action
网站物理路径: /usr/local/ucenter
java.home: /usr/java/jdk1.5.0_06/jre
java.version: 1.5.0_06
os.name: Linux
os.arch: i386
os.version: 2.6.18-92.el5
user.name: root
user.home: /root
user.dir: /root
eth0 Link encap:Ethernet HWaddr 00:1E:C9:B8:95:9D
inet addr:192.168.1.13 Bcast:192.168.1.255 Mask:255.255.255.0
inet6 addr: fe80::21e:c9ff:feb8:959d/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:1367574738 errors:0 dropped:0 overruns:0 frame:0
TX packets:811675317 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:202566496226 (188.6 GiB) TX bytes:187154200360 (174.3 GiB)
Interrupt:169 Memory:f8000000-f8012100
eth1 Link encap:Ethernet HWaddr 00:1E:C9:B8:95:9F
inet addr:10.10.10.13 Bcast:10.10.10.255 Mask:255.255.255.0
inet6 addr: fe80::21e:c9ff:feb8:959f/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:554395930 errors:0 dropped:0 overruns:0 frame:0
TX packets:182724699 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:162249198852 (151.1 GiB) TX bytes:20384776529 (18.9 GiB)
Interrupt:169 Memory:f4000000-f4012100
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:16436 Metric:1
RX packets:3750930 errors:0 dropped:0 overruns:0 frame:0
TX packets:3750930 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:334641604 (319.1 MiB) TX bytes:334641604 (319.1 MiB)
lo:ucweb Link encap:Local Loopback
inet addr:192.168.1.217 Mask:255.255.255.255
UP LOOPBACK RUNNING MTU:16436 Metric:1
lo:0 Link encap:Local Loopback
inet addr:192.168.1.218 Mask:255.255.255.255
UP LOOPBACK RUNNING MTU:16436 Metric:1
lo:8769 Link encap:Local Loopback
inet addr:192.168.1.219 Mask:255.255.255.255
UP LOOPBACK RUNNING MTU:16436 Metric:1
jdbc.master.driverClassName=com.mysql.jdbc.Driver
jdbc.master.url=jdbc:mysql://master.ucenter.db:3306/ucenter?useUnicode=true&characterEncoding=UTF-8
jdbc.master.username=grid
jdbc.master.password=grid
jdbc.slaver.driverClassName=com.mysql.jdbc.Driver
jdbc.slaver.url=jdbc:mysql://slave.ucenter.db:3306/ucenter?useUnicode=true&characterEncoding=UTF-8
jdbc.slaver.username=grid
jdbc.slaver.password=grid
同时强烈建议彻查10.10.10.81此服务器的后门及各种权限,修改系统密码、数据库密码;
jdbc.driverClassName=org.gjt.mm.mysql.Driver
#jdbc.url=jdbc:mysql://localhost:3306/teacherclubauthority?useUnicode=true&characterEncoding=UTF-8
#jdbc.url=jdbc:mysql://10.10.10.110:3306/dtsauthority?useUnicode=true&SelectMethod=Cursor&characterEncoding=UTF-8
jdbc.url=jdbc:mysql://db.dts.host:3306/dtsauthority?useUnicode=true&SelectMethod=Cursor&characterEncoding=UTF-8
jdbc.username=root
jdbc.password=srttest
eth0 Link encap:Ethernet HWaddr 00:30:48:D5:F6:4A
inet addr:192.168.1.81 Bcast:192.168.1.255 Mask:255.255.255.0
inet6 addr: fe80::230:48ff:fed5:f64a/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:59064843065 errors:35555 dropped:1348 overruns:0 frame:29361
TX packets:84287274407 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:17203587269987 (15.6 TiB) TX bytes:79208430866539 (72.0 TiB)
Memory:fc400000-fc420000
eth1 Link encap:Ethernet HWaddr 00:30:48:D5:F6:4B
inet addr:10.10.10.81 Bcast:10.10.10.255 Mask:255.255.255.0
inet6 addr: fe80::230:48ff:fed5:f64b/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:38447892281 errors:7 dropped:0 overruns:0 frame:4
TX packets:39092771155 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:28023906757374 (25.4 TiB) TX bytes:8813716604203 (8.0 TiB)
Memory:fc500000-fc520000
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:16436 Metric:1
RX packets:14353954794 errors:0 dropped:0 overruns:0 frame:0
TX packets:14353954794 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:83788103836248 (76.2 TiB) TX bytes:83788103836248 (76.2 TiB)
lo:0 Link encap:Local Loopback
inet addr:192.168.1.3 Mask:255.255.255.255
UP LOOPBACK RUNNING MTU:16436 Metric:1
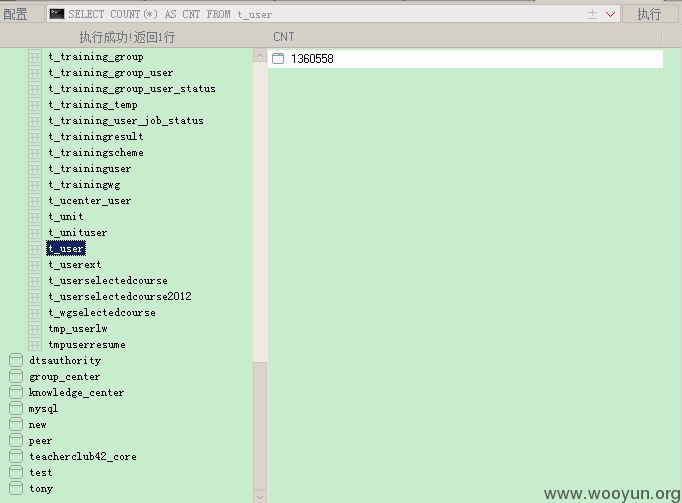
漏洞证明:
http://ucenter.teacherclub.com.cn/ucenter/user/regist!registUserInput.action
网站物理路径: /usr/local/ucenter
java.home: /usr/java/jdk1.5.0_06/jre
java.version: 1.5.0_06
os.name: Linux
os.arch: i386
os.version: 2.6.18-92.el5
user.name: root
user.home: /root
user.dir: /root
eth0 Link encap:Ethernet HWaddr 00:1E:C9:B8:95:9D
inet addr:192.168.1.13 Bcast:192.168.1.255 Mask:255.255.255.0
inet6 addr: fe80::21e:c9ff:feb8:959d/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:1367574738 errors:0 dropped:0 overruns:0 frame:0
TX packets:811675317 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:202566496226 (188.6 GiB) TX bytes:187154200360 (174.3 GiB)
Interrupt:169 Memory:f8000000-f8012100
eth1 Link encap:Ethernet HWaddr 00:1E:C9:B8:95:9F
inet addr:10.10.10.13 Bcast:10.10.10.255 Mask:255.255.255.0
inet6 addr: fe80::21e:c9ff:feb8:959f/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:554395930 errors:0 dropped:0 overruns:0 frame:0
TX packets:182724699 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:162249198852 (151.1 GiB) TX bytes:20384776529 (18.9 GiB)
Interrupt:169 Memory:f4000000-f4012100
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:16436 Metric:1
RX packets:3750930 errors:0 dropped:0 overruns:0 frame:0
TX packets:3750930 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:334641604 (319.1 MiB) TX bytes:334641604 (319.1 MiB)
lo:ucweb Link encap:Local Loopback
inet addr:192.168.1.217 Mask:255.255.255.255
UP LOOPBACK RUNNING MTU:16436 Metric:1
lo:0 Link encap:Local Loopback
inet addr:192.168.1.218 Mask:255.255.255.255
UP LOOPBACK RUNNING MTU:16436 Metric:1
lo:8769 Link encap:Local Loopback
inet addr:192.168.1.219 Mask:255.255.255.255
UP LOOPBACK RUNNING MTU:16436 Metric:1
jdbc.master.driverClassName=com.mysql.jdbc.Driver
jdbc.master.url=jdbc:mysql://master.ucenter.db:3306/ucenter?useUnicode=true&characterEncoding=UTF-8
jdbc.master.username=grid
jdbc.master.password=grid
jdbc.slaver.driverClassName=com.mysql.jdbc.Driver
jdbc.slaver.url=jdbc:mysql://slave.ucenter.db:3306/ucenter?useUnicode=true&characterEncoding=UTF-8
jdbc.slaver.username=grid
jdbc.slaver.password=grid
同时强烈建议彻查10.10.10.81此服务器的后门及各种权限,修改系统密码、数据库密码;
jdbc.driverClassName=org.gjt.mm.mysql.Driver
#jdbc.url=jdbc:mysql://localhost:3306/teacherclubauthority?useUnicode=true&characterEncoding=UTF-8
#jdbc.url=jdbc:mysql://10.10.10.110:3306/dtsauthority?useUnicode=true&SelectMethod=Cursor&characterEncoding=UTF-8
jdbc.url=jdbc:mysql://db.dts.host:3306/dtsauthority?useUnicode=true&SelectMethod=Cursor&characterEncoding=UTF-8
jdbc.username=root
jdbc.password=srttest
eth0 Link encap:Ethernet HWaddr 00:30:48:D5:F6:4A
inet addr:192.168.1.81 Bcast:192.168.1.255 Mask:255.255.255.0
inet6 addr: fe80::230:48ff:fed5:f64a/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:59064843065 errors:35555 dropped:1348 overruns:0 frame:29361
TX packets:84287274407 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:17203587269987 (15.6 TiB) TX bytes:79208430866539 (72.0 TiB)
Memory:fc400000-fc420000
eth1 Link encap:Ethernet HWaddr 00:30:48:D5:F6:4B
inet addr:10.10.10.81 Bcast:10.10.10.255 Mask:255.255.255.0
inet6 addr: fe80::230:48ff:fed5:f64b/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:38447892281 errors:7 dropped:0 overruns:0 frame:4
TX packets:39092771155 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:28023906757374 (25.4 TiB) TX bytes:8813716604203 (8.0 TiB)
Memory:fc500000-fc520000
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:16436 Metric:1
RX packets:14353954794 errors:0 dropped:0 overruns:0 frame:0
TX packets:14353954794 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:83788103836248 (76.2 TiB) TX bytes:83788103836248 (76.2 TiB)
lo:0 Link encap:Local Loopback
inet addr:192.168.1.3 Mask:255.255.255.255
UP LOOPBACK RUNNING MTU:16436 Metric:1
修复方案:
下载修复补丁:
http://struts.apache.org/download.cgi#struts234
版权声明:转载请注明来源 啦绯哥@乌云
漏洞回应
厂商回应:
危害等级:低
漏洞Rank:5
确认时间:2013-04-26 16:16
厂商回复:
CNVD确认并复现所述情况,已在24日由CNVD直接联系上网站管理方处置,对方技术人员已经确认并着手修复。
按通用软件漏洞进行评分,rank 5
最新状态:
暂无