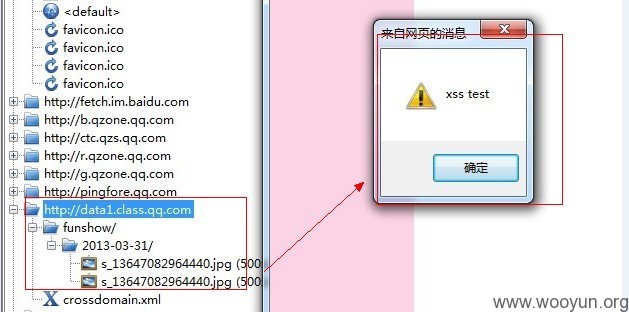
时隔多天,今天空闲了点,就去看看腾讯对上一个报告修复的如何了。 结果,修是修了,不过之前出现的错误修复再一次出现了,并且我在系列9修复方案中所担心会出现的修复方式,也出现了。因此,问题依然存在。 前些天某同学在乌云上提交的某漏洞被腾讯认为“不构成危害”忽略了,这里变废为宝,拿绕过腾讯的过滤方式挺不错的~~
1. 可以看到腾讯按照修复意见,对load的URL采用了checkURL函数进行判断。
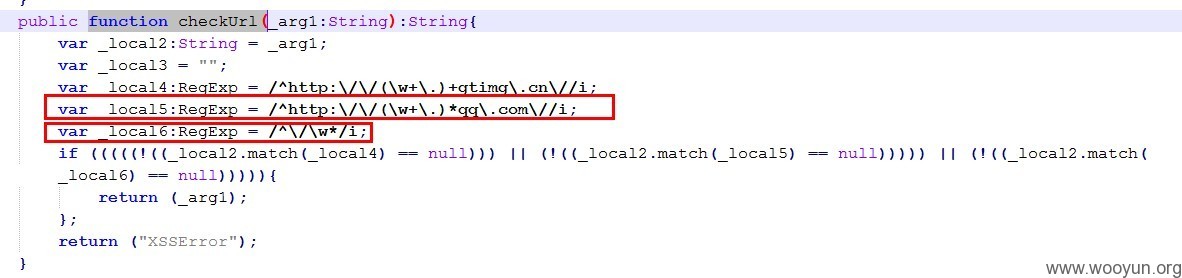
上面这种判断,显然是存在问题的。
2. 一方面,开发人员又采用了 / 开头的正则, 作为判断相对路径的依据,前面已经犯过的错误。
同系列9,采用 //xsst.sinaapp.com/Xss.swf 即可绕过。
发布日志时,修改字段gridJson如下:
3. 另一方面,系列9的修复方案中,我已经说到了,最好不要使用 *.qq.com/... 的方式来判断外部资源URL。
结果这里就是采用的这种方式来判断的,因而我这里给出个简单的绕过方法。
前些天腾讯忽略了一个文件上传的漏洞,我们拿来用一用。
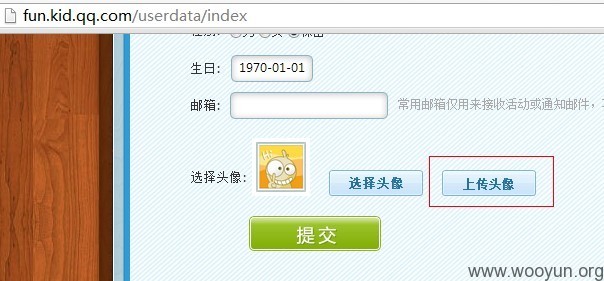
可以看到我们成功上传了一个FLASH文件,后缀采用JPG,腾讯这里没有对内容进行判断,仅仅是后缀。
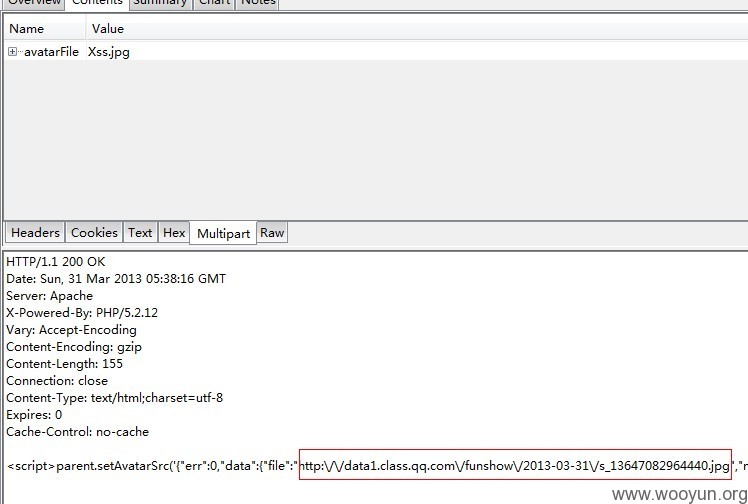
将image的URL指定为新上传的地址。 http://data1.class.qq.com/funshow/2013-03-31/s_13647082964440.jpg#.swf
发布日志时,修改字段gridJson如下:
可以看到打开日志时,成功加载我们上传的文件,并执行XSS。