漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2016-0170351
漏洞标题:163网易邮箱存储型XSS漏洞
相关厂商:网易
漏洞作者: mramydnei
提交时间:2016-01-16 13:10
修复时间:2016-03-04 13:27
公开时间:2016-03-04 13:27
漏洞类型:XSS 跨站脚本攻击
危害等级:中
自评Rank:10
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2016-01-16: 细节已通知厂商并且等待厂商处理中
2016-01-19: 厂商已经确认,细节仅向厂商公开
2016-01-29: 细节向核心白帽子及相关领域专家公开
2016-02-08: 细节向普通白帽子公开
2016-02-18: 细节向实习白帽子公开
2016-03-04: 细节向公众公开
简要描述:
主要是抛出了一个异常,让问题变得简单了许多
详细说明:
通过网易邮箱测试内容量较大的htm文件的预览时,抛出了了这样的异常。
感觉类名挺个性的,就去github找了一下。发现了这个:
build.xml中多处出现163.org,netease的字样。这多半是和网易脱离不了干系了。
果断把下面的jar抱回家看了下,xss怎么过滤的:
看了下base-config.properties:
过滤了什么没过滤什么一目了然,也就没啥好分析的了。
构造poc,pwn之。
漏洞证明:
将下面的内容存储为pwn.htm
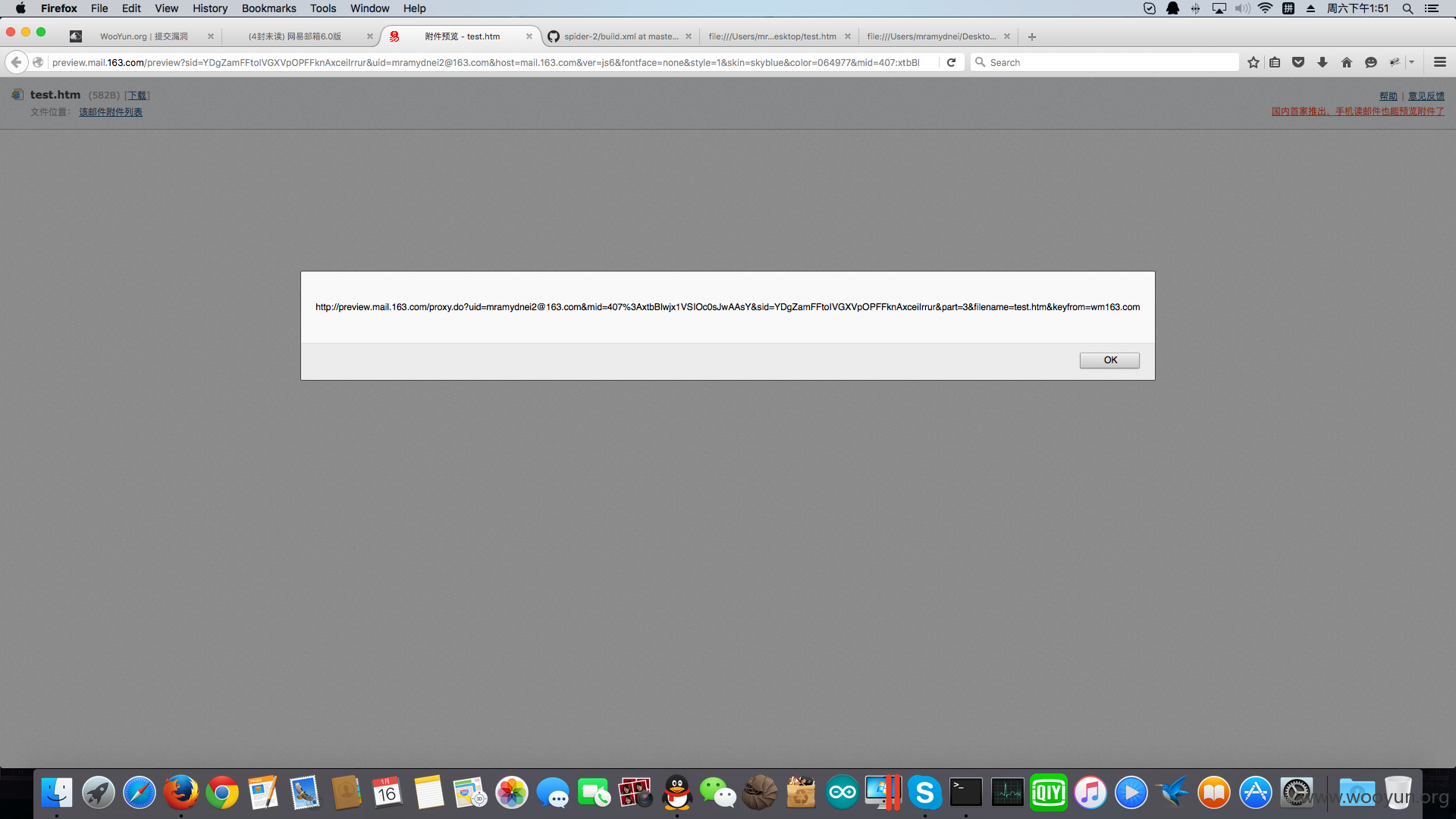
添加到邮件附件,发送给victim。victim对文件进行浏览时:
游戏就结束了。上面的poc需要在ff下进行验证。
如果觉得影响范围不足够,可以和我联系。我可以进行进一步提供更通用的poc。
最后,如果上述问题属于coremail的问题,麻烦告知一下我好去拿奖金。
修复方案:
removeNodeTags加一个svg?
版权声明:转载请注明来源 mramydnei@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:10
确认时间:2016-01-19 15:38
厂商回复:
漏洞已确认,将于近期修复,感谢您对网易产品的关注。
最新状态:
暂无