1.创建镜像这个地方支持使用dockfile进行构建
https://c.163.com/dashboard#/m/repo/create/
那么我们知道dockfile是可以执行任意命令的
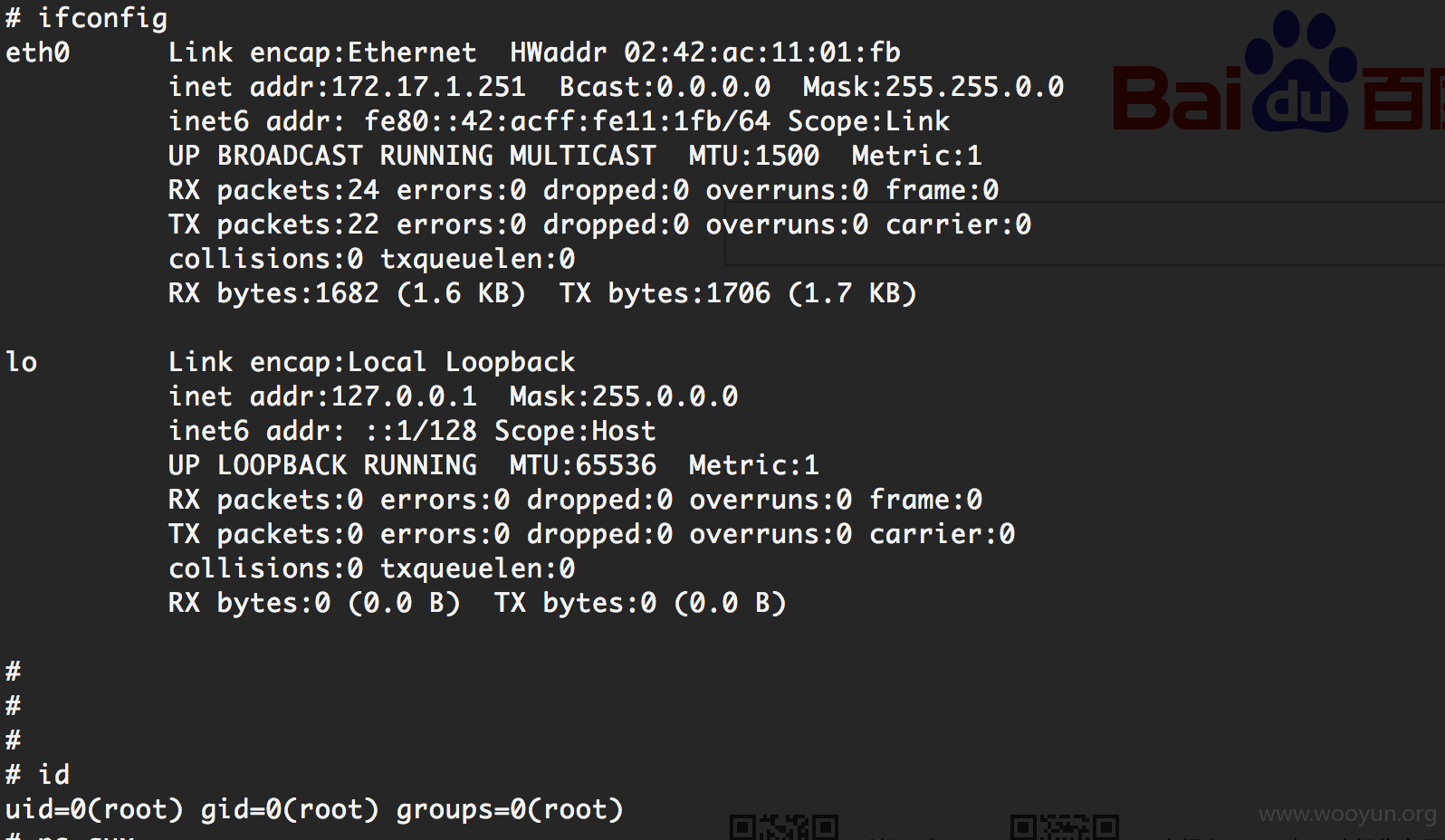
2.利用dockfile构建时执行任意命令,可shell
3.通过反弹shell获取其中一台构建服务器的权限,然后对172网段进行了一下探测,发现
通过分析172.17.42.1就是蜂巢的官网,而172.17.42.1:8081是内部api
通过这个接口大概能看到有1522个uid的信息
其他的一些接口就没有仔细测了