漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-093600
漏洞标题:联想某站点多处注入(附验证脚本)
相关厂商:联想
漏洞作者: Vigoss_Z
提交时间:2015-01-24 17:48
修复时间:2015-03-10 17:50
公开时间:2015-03-10 17:50
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:18
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-01-24: 细节已通知厂商并且等待厂商处理中
2015-01-26: 厂商已经确认,细节仅向厂商公开
2015-02-05: 细节向核心白帽子及相关领域专家公开
2015-02-15: 细节向普通白帽子公开
2015-02-25: 细节向实习白帽子公开
2015-03-10: 细节向公众公开
简要描述:
rt
详细说明:
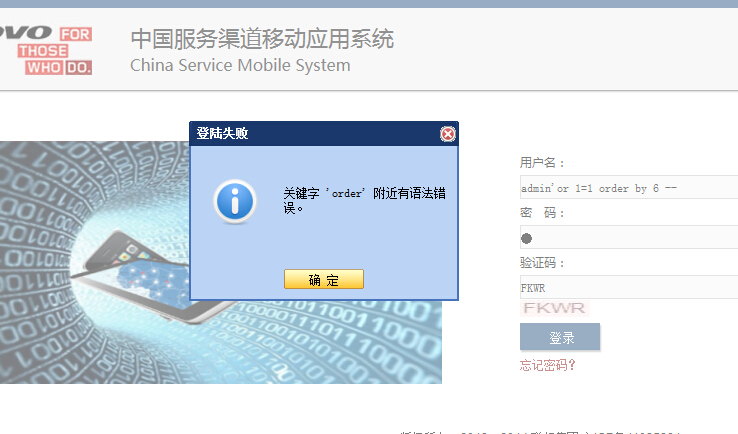
用户登录,用户名:'or '1'='1,用户未启用。
但是这里的登陆过程比较复杂,用户名和密码发送到服务端,利用ajax加密后,再代入请求中验证。。。(虽然有验证码,但是是摆设)
好吧,找另一处,找回密码处:
用户名错误请重新输入;用户或邮箱错误,注入
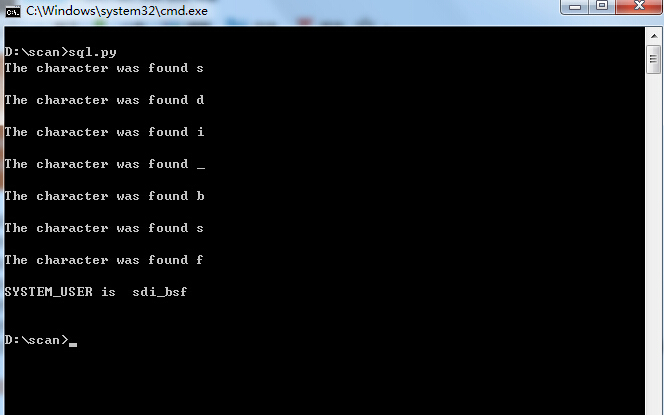
写了个脚本跑出sysem_user:
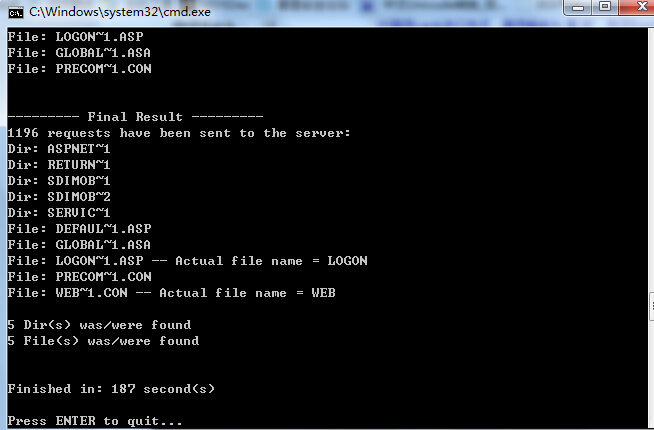
还有个iis枚举文件名:
漏洞证明:
用户登录,用户名:'or '1'='1,用户未启用。
但是这里的登陆过程比较复杂,用户名和密码发送到服务端,利用ajax加密后,再代入请求中验证。。。(虽然有验证码,但是是摆设)
好吧,找另一处,找回密码处:
用户名错误请重新输入;用户或邮箱错误,注入
写了个脚本跑出sysem_user:sdi_bsf
还有个iis枚举文件名:
修复方案:
版权声明:转载请注明来源 Vigoss_Z@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:10
确认时间:2015-01-26 14:46
厂商回复:
谢谢您对联想安全工作的支持,我们会尽快修复漏洞
最新状态:
暂无