LebiShop商城系统最新版验证码存在设计缺陷可无视验证码,及存储型XSS盲打后台
验证码设计缺陷:
LebiShop商城系统有两者验证码验证方式
1、直接判断POST提交的验证码已经COOKIE中的验证码是否相等
如前台普通用户登陆时
直接判断verifycode和CheckCodef是否相等
这里我们在发送请求时,将POST和COOKIE中的值设置为一样即可绕过
2、判断COOKIE的某值是否为空,然后在进行第1中方式的验证
如后台登陆
先判断COOKIE中的AdminLoginError是否为空,在进行code的判断
这里在发送请求时,直接将COOKIE中的AdminLoginError设置为空即可绕过验证码
XSS盲打后台
很多地方都存在盲打后台的地方,全局只进行了<,>,'三个符号的处理
但是在获取X-Forwarded-For时,没有使用全局处理,直接赋值
如在商家用户登陆处
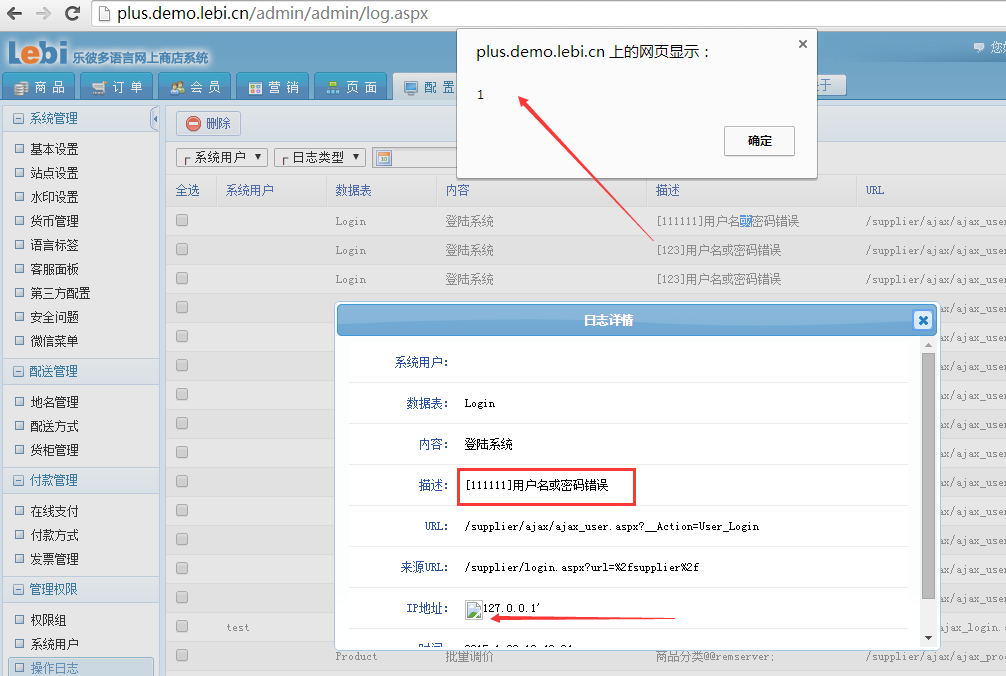
这里是否登录成功都会有log记录
跟进Log.Add函数
继续跟进
到最后,注意这里log.IP_Add = RequestTool.GetClientIP();
这里直接从HTTP_X_FORWARDED_FOR获取了内容,然后进入了log中