漏洞概要
关注数(24)
关注此漏洞
漏洞标题:高德导航某接口XML实体注入
提交时间:2015-12-14 09:05
修复时间:2016-01-28 17:10
公开时间:2016-01-28 17:10
漏洞类型:文件包含
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
Tags标签:
无
漏洞详情
披露状态:
2015-12-14: 细节已通知厂商并且等待厂商处理中
2015-12-16: 厂商已经确认,细节仅向厂商公开
2015-12-26: 细节向核心白帽子及相关领域专家公开
2016-01-05: 细节向普通白帽子公开
2016-01-15: 细节向实习白帽子公开
2016-01-28: 细节向公众公开
简要描述:
我不能再默默无闻下去了...
PS:我上次听说你们是要送礼物的?
详细说明:

在我对高德地图离线版进行测试时抓到一个接口
便进行了深入测试
实际产生漏洞的接口:
一个正常的页面
抓包内容:
测试了一下发现存在XML注入
构造代码读取etc/passwd
成功返回,root权限
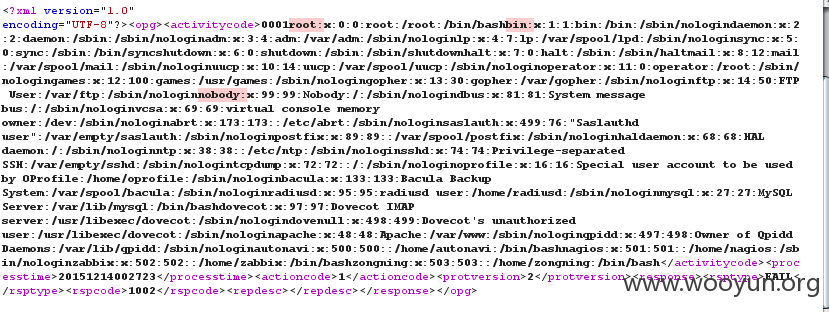
危害挺大,可以进行其它操作,或构造XML语句进行攻击!
漏洞证明:

在我对高德地图离线版进行测试时抓到一个接口
便进行了深入测试
实际产生漏洞的接口:
一个正常的页面

抓包内容:
测试了一下发现存在XML注入
构造代码读取etc/passwd
成功返回,root权限

危害挺大,可以进行其它操作,或构造XML语句进行攻击!
修复方案:
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:6
确认时间:2015-12-16 16:32
厂商回复:
亲,漏洞已经在处理中,感谢您对阿里巴巴的关注和支持!
最新状态:
暂无





